4.4.7.1 Logical design
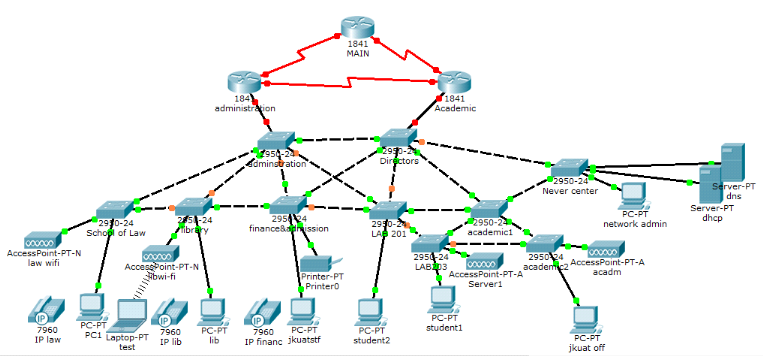
Figure 4.14. Proposed logical design
The merits of the new proposed logical design Ares;
ü Make the network scalable
ü Availability
ü Reduce large domain failure.
ü Create link and devices redundancy by adding 3 router to
ensure if one fails 2 will keep running and serve.
ü Allow integration of voice and video in one network.
ü Reduce broadcast domain.
4.4.7.1 Proposed
security strategies
The new system has the following security features;
a. Port shutdown or port security, which blocks any attempt of
port sniffing.
b. Implementation of VLAN virtual local area network, this
segment network into sub network. Which will separate user in the network. The
purpose is to deny access students or unauthorized staff to access critical
information like database of marks and finance.
c. Secured wireless access point (WAP) and deploy wireless round
the campus.
| 


