4. SCAN DES VULNERABILITES
AVEC NESSUS
Nessus est un outil de test de vulnérabilité. Il
fonctionne en mode client/serveur, avec une interface graphique. Une fois
installé, le serveur « Nessusd »,
éventuellement sur une machine distante, effectue les tests et les
envoie au client « Nessus » qui fonctionne sur une
interface graphique.
Nessus est un produit commercial diffusé par la
société TENABLE Network Security. Il peut toutefois
être utilisé gratuitement avec une base des
vulnérabilités dont la mise à jour est
décalée d'une semaine.
Les résultats peuvent être enregistrés
sous divers formats : NBE, NSR et html.
Notre but dans cette partie est surtout de présenter
les résultats des scans de vulnérabilités effectués
sur le réseau informatique de la First Bank. Nous avons scanné
les vulnérabilités connues de Nessus sur le serveur web, le
serveur DNS, les routeurs du VPN ainsi que les PIX des fournisseurs
d'accès à Internet.
Scan des vulnérabilités du serveur DNS
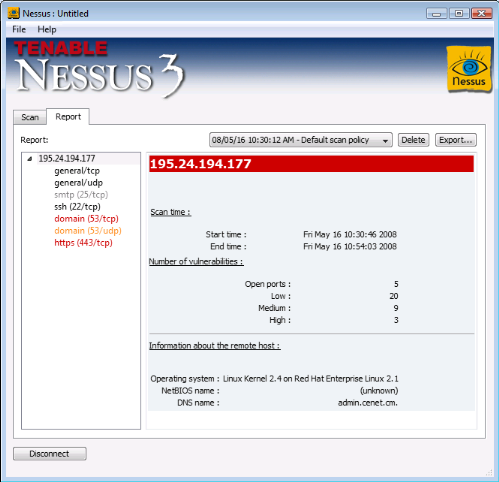
Vulnérabilités de niveau moyen
|
DNS Cache Snooping
|
|
Synopsis:
Remote DNS server is
vulnerable to cache snooping attacks.
Description:
The remote DNS server answers to queries for third-party
domains which do not have the recursion bit set.
This may allow a
remote attacker to determine which domains have recently been resolved via this
name server, and therefore which hosts have been recently visited.
For
instance, if an attacker was interested in whether your company utilizes the
online services of a particular financial institution, they would be able to
use this attack to build a statistical model regarding company usage of
aforementioned financial institution. Of course, the attack can also be used to
find B2B partners, web-surfing patterns, external mail servers, and more...
See also :
For a much more detailed discussion
of the potential risks of allowing DNS cache information to be queried
anonymously, please see:
http://www.nessus.org/u?0f22a4a4
Risk
factor :
Medium / CVSS Base Score :
5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Nessus ID :
12217
|
|
Usable remote name server
|
|
Synopsis:
The remote name server
allows recursive queries to be performed by the host running
nessusd.
Description:
It is possible to query
the remote name server for third party names.
If this is your internal
nameserver, then forget this warning.
If you are probing a remote
nameserver, then it allows anyone to use it to resolve third parties names
(such as
www.nessus.org). This allows hackers
to do cache poisoning attacks against this nameserver.
If the host
allows these recursive queries via UDP, then the host can be used to 'bounce'
Denial of service attacks against another network or system.
See
also:
http://www.cert.org/advisories/CA-1997-22.html
Solution:
Restrict recursive queries to the hosts that should use this nameserver
(such as those of the LAN connected to it).
If you are using bind 8, you
can do this by using the instruction 'allow-recursion' in the 'options' section
of your named.conf
If you are using bind 9, you can define a grouping of
internal addresses using the 'acl' command
Then, within the options
block, you can explicitly state: 'allow-recursion { hosts_defined_in_acl
}'
For more info on Bind 9 administration (to include recursion), see:
http://www.nominum.com/content/documents/bind9arm.pdf
If
you are using another name server, consult its documentation.
|
|
Weak Supported SSL Ciphers Suites
|
|
Synopsis:
The remote service
supports the use of weak SSL ciphers.
Description:
The remote host supports the use of SSL ciphers that offer
either weak encryption or no encryption at all.
See also:
http://www.openssl.org/docs/apps/ciphers.html
Solution:
Reconfigure the affected application if possible to avoid use
of weak ciphers.
Risk factor :
Medium / CVSS
Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Plugin
output :
Here is the list of weak SSL ciphers supported by the
remote server :
Low Strength Ciphers (< 56-bit
key)
SSLv2
EXP-R-CBC-MD5 Kx=RSA(512) Au=RSA Enc=R(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
SSLv3
EXP-EDH-RSA-DES-CBC-SHA Kx=DH(512) Au=RSA Enc=DES(40) Mac=SHA1
export
EXP-DES-CBC-SHA Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-R-CBC-MD5 Kx=RSA(512) Au=RSA Enc=R(40) Mac=MD5 export
EXP-RC4-MD5
Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export
TLSv1
EXP-DES-CBC-SHA
Kx=RSA(512) Au=RSA Enc=DES(40) Mac=SHA1 export
EXP-R-CBC-MD5 Kx=RSA(512)
Au=RSA Enc=R(40) Mac=MD5 export
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40)
Mac=MD5 export
The fields above are :
{OpenSSL
ciphername}
Kx={key exchange}
Au={authentication}
Enc={symmetric
encryption method}
Mac={message authentication code}
{export
flag}
Nessus ID :
26928
|
|
SSL Certificate Expiry
|
|
The SSL certificate of the remote service expired Jul 18 11:58:05
2005 GMT!
Nessus ID :
15901
|
|
Deprecated SSL Protocol Usage
|
|
Synopsis:
The remote service
encrypts traffic using a protocol with known weaknesses.
Description:
The remote service accepts
connections encrypted using SSL 2.0, which reportedly suffers from several
cryptographic flaws and has been deprecated for several years. An attacker may
be able to exploit these issues to conduct man-in-the-middle attacks or decrypt
communications between the affected service and clients.
See
also:
http://www.schneier.com/paper-ssl.pdf
Solution:
Consult the application's documentation to disable SSL 2.0 and
use SSL 3.0 or TLS 1.0 instead.
Risk factor :
Medium / CVSS Base Score :
5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Nessus ID :
20007
|
|
PHP Mail Function Header Spoofing
Vulnerability
|
|
The remote host is running a version of PHP <=
4.2.2.
The mail() function does not properly sanitize user input. This
allows users to forge email to make it look like it is coming from a different
source other than the server.
Users can exploit this even if SAFE_MODE
is enabled.
Solution: Contact your vendor for the
latest PHP release.
Risk factor : Medium
CVE : CVE-2002-0985, CVE-2002-0986
BID : 5562
Other
references : OSVDB:2111
Nessus ID :
11444
|
|
PHP Multiple Unspecified Vulnerabilities
|
|
The remote host is running a version of PHP which is older
than 5.0.3 or 4.3.11
The remote version of this software is vulnerable
to a set of vulnerabilities in the EXIF module which have been fixed by the PHP
Group.
See also :
http://www.php.net/ChangeLog-5.php#5.0.4
http://www.php.net/ChangeLog-4.php#4.3.11
Solution
: Upgrade to PHP 5.0.3 or 4.3.11
Risk factor :
Medium
BID : 13143, 13163, 13164
Nessus ID :
18033
|
|
Apache Remote Username Enumeration
Vulnerability
|
|
Synopsis:
The remote Apache
server can be used to guess the presence of a given user name on the remote
host.
Description:
When configured with the
'UserDir' option, requests to URLs containing a tilde followed by a username
will redirect the user to a given subdirectory in the user home.
For
instance, by default, requesting /~root/ displays the HTML contents from
/root/public_html/.
If the username requested does not exist, then
Apache will reply with a different error code. Therefore, an attacker may
exploit this vulnerability to guess the presence of a given user name on the
remote host.
Solution:
In httpd.conf, set the
'UserDir' to 'disabled'.
Risk factor :
Medium /
CVSS Base Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
CVE :
CVE-2001-1013
BID : 3335
Other references : OSVDB:637
Nessus ID :
10766
|
|
HTTP TRACE / TRACK Methods
|
|
Synopsis:
Debugging functions are
enabled on the remote web server.
Description:
The remote webserver supports the TRACE and/or TRACK methods. TRACE and
TRACK are HTTP methods which are used to debug web server connections.
In addition, it has been shown that servers supporting the TRACE method
are subject to cross-site scripting attacks, dubbed XST for "Cross-Site
Tracing", when used in conjunction with various eaknesses in browsers. An
attacker may use this flaw to trick your legitimate web users to give him their
credentials.
See also:
http://www.cgisecurity.com/whitehat-mirror/WH-WhitePaper_XST_ebook.pdf
http://www.apacheweek.com/issues/03-01-24
http://www.kb.cert.org/vuls/id/867593
Solution:
Disable these methods.
Risk factor :
Medium / CVSS Base
Score : 5.0
(CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N)
Solution :
Add the
following lines for each virtual host in your configuration file
:
RewriteEngine on
RewriteCond %{REQUEST_METHOD}
^(TRACE|TRACK)
RewriteRule .* - [F]
Alternatively, note that Apache
versions 1.3.34, 2.0.55, and 2.2 support disabling the TRACE method natively
via the 'TraceEnable' directive.
Plugin output :
The server
response from a TRACE request is :
TRACE /Nessus2324.html
HTTP/1.1
Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg,
image/png, */*
Accept-Charset: iso-8859-1,*,utf-8
Accept-Language:
en
Connection: Close
Host: admin.cenet.cm
Pragma:
no-cache
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT
5.0)
CVE : CVE-2004-2320
BID : 9506, 9561, 11604
Other references
: OSVDB:877, OSVDB:3726
Nessus ID :
11213
|
Vulnérabilités de niveau
élevé
|
BIND 9 overflow
|
|
The remote BIND 9 DNS server, according to its version
number, is vulnerable to a buffer overflow which may allow an attacker to gain
a shell on this host or to disable this
server.
Solution: upgrade to bind 9.2.2 or downgrade to
the 8.x series
See also:
http://www.isc.org/products/BIND/bind9.html
http://cert.uni-stuttgart.de/archive/bugtraq/2003/03/msg00075.html
http://www.cert.org/advisories/CA-2002-19.html
Risk
factor: High
CVE : CVE-2002-0684
Other references :
IAVA:2003-B-0001
Nessus ID :
11318
|
|
php PHP_Variables Memory Disclosure
|
|
The remote host is running a version of PHP which is older
than 5.0.2 or
4.39.
The remote version of this software is vulnerable
to a memory disclosure vulnerability in PHP_Variables. An attacker may exploit
this flaw to remotely read portions of the memory of the httpd process on the
remote host.
See also:
http://www.php.net/ChangeLog-5.php#5.0.2
Solution: Upgrade to PHP 5.0.2 or
4.3.9
Risk factor: High
BID : 11334
Nessus ID :
15436
|
|
php4/5 Vulnerabilities
|
|
The remote host is running a version of PHP which is older
than 5.0.3 or 4.3.10.
The remote version of this software is vulnerable
to various security issues which may, under certain circumstances, to execute
arbitrary code on the remote host, provided that we can pass arbitrary data to
some functions, or to bypass safe_mode.
See also :
http://www.php.net/ChangeLog-5.php#5.0.3
Solution : Upgrade to PHP 5.0.3 or
4.3.10
Risk factor : High
CVE : CVE-2004-1018, CVE-2004-1019, CVE-2004-1020,
CVE-2004-1063, CVE-2004-1064, CVE-2004-1065
BID : 11964, 11981, 11992,
12045
Other references : OSVDB:12410
Nessus ID :
15973
|
Nous avons également effectué le scan des
vulnérabilités sur les VPN de Douala, Bafoussam, Bamenda, Garoua,
Kousséri, Nkongsamba, Limbé, Maroua ainsi que le serveur web/mail
de la banque.
Comme nous pouvons le constater à travers les tableaux
précédents, Nessus présente les résultats des scans
de vulnérabilités de manière très didactique : pour
chaque faille, on a une présentation claire du problème et une
solution simple. Cet outil peut très certainement permettre à un
attaquant d'évaluer les faiblesses d'un réseau en vue d'une
attaque, en indiquant quelles failles exploiter et avec quelles techniques. Par
contre, tout administrateur devrait prendre une longueur d'avance sur les
attaquants en se servant en premier d'un tel outil pour éviter au moins
les attaques connues de Nessus.
|
|



