|

September 2013
E-commerce capabilities assessment:
-Security of
e-payment systems-
Case of the Democratic republic of
Congo
Master Thesis
Author: Esperant NGONGO
Supervisor: Prof. Roberta Bernardi
Page | 2
Outline
E-commerce capabilities assessment: security of e-payment
systems. Case of the Democratic republic of Congo
Table of Content
Abstract Preface
Acknowledgement
1. Introduction 6
1.1. Introduction 6
1.2. Motivation of the subject 6
1.3. Problem statement 7
1.4. Research questions 7
1.5. Scope and limitations 7
1.6. Methodology 8
2. Literature review 9
2.1. Overview 9
2.2. Definition of e-commerce 9
2.3. Types of e-commerce 10
2.4. M-commerce 12
2.5. E-commerce capabilities overview 12
2.6. Information system capabilities 13
2.6.1. Introduction 13
2.6.2. Information system capabilities overview 13
2.6.3. Information system capabilities in the scope of
e-commerce 15
2.6.4. Information technology infrastructure for e-commerce
16
2.7. Information security capabilities for e-commerce 18
2.7.1. Introduction 18
2.7.2. Overview of the security of e-commerce 18
2.7.3. Overview of the security of e-commerce network 26
2.8. Securing e-payment systems for B2C e-commerce 28
2.8.1. Payment cards 29
2.8.2. Electronic cash 30
2.8.3. Stored-value card 31
2.8.4. E-checking 31
2.8.5. Security of mobile payment 33
2.9. Conclusion on the literature review 33
3. Research methodology 34
3.1. Introduction 34
3.2. Research design and justification 34
3.2.1. Introduction 34
3.2.2. Choice of the methodology 36
3.3. Data collection and sampling 37
3.3.1. Sampling technique 37
3.3.2. Sampling definition 38
3.3.3. Data collection method 39
Page | 3
3.4. Data analysis 40
3.4.1. Introduction 40
3.4.2. Data analysis method 41
4. Research findings 42
4.1. Response rate 42
4.2. Research findings 42
4.2.1. Working experience of respondents 42
4.2.2. Job position 43
4.2.3. E-payment services offered 44
4.2.4. Issues faced by e-payment systems 44
4.3. Specific findings for CIA security concept 45
4.3.1. Confidentiality 45
4.3.2. Integrity 46
4.3.3. Availability 48
4.4. Summary 49
5. Conclusion and recommendations 50
5.1. Introduction 50
5.2. Conclusion 50
5.2.1. E-payment system 50
5.2.2. E-payment system security 50
5.3. Recommendations 52
5.4. Areas for further studies 53
5.5. Study limitations 53
6. References / Bibliography 54
7. Appendix 57
7.1. List of abbreviations 57
7.2. List of figures 58
7.3. List of table 58
7.4. Questionnaire 69
Statement of originality
In presenting this dissertation for assessment, I declare that
it is a final copy including any last revisions. I also declare that it is
entirely the result of my own work other than where sources are explicitly
acknowledged and referenced within the body of the text. This dissertation has
not been previously submitted for any degree at this or any other
institution.
Page | 4
Esperant NGONGO MBULI
Page | 5
Abstract
This research study investigates to what extend the e-payment
systems are secured in order to contribute to the development of e-commerce
capabilities in the Democratic Republic of Congo (DRC). This study has also
assesses the existence of adequate e-commerce capabilities in terms of
e-payment systems and how their security can be leveraged to really contribute
to their effective use in the electronic payment transaction.
The research uses the survey method with questionnaire based
on closed questions built from the checklist published by the International
Standards Organization (ISO) as framework for information security
assessment.
The major conclusion of this study is that some capabilities
for e-commerce such as e-payment systems are available in the country but their
security must be enforced and managed for the advert of e-commerce era which is
yet in its inception phase.
Acknowledgement
I would like to thank the following people who provided to me
significant support for the completion of my MBA program and this research,
namely:
- Professor Roberta Bernardi, my supervisor, she has been a
great source of advice and guidance in the development of this research and her
valuable
support on reading material was highly appreciated. Thank you so
much.
- My lovely wife, Tina who has been an important pillar and
source of motivation through my MBA program and during this research. Thank you
for your patience and lovely commitment shown.
- My children, Grace, Kelly, Joyce, Marie-Rose and Esperance
Junior to whom I missed during the time I was involved in my journey to MBA and
for the fun time sacrificed to the benefit of this research. This study is
dedicated to you as source of motivation and inspiration for your studies as
well.
- The professors at Robert Kennedy College who gave us
valuable intellectual foods and reading materials for the acquisition of
knowledge in Advanced Information Technology and Business Management. Thank you
for your devotion.
- Above all, the Mighty GOD for the blessing given to the
success of this achievement
Page | 6
Chapter 1: Introduction
I.1. Introduction
Modern electronic commerce (e-commerce) is one of the biggest
commercial activities using the internet as channel of diffusion. The advance
and continuing development of internet technologies in telecommunications and
mobile applications has propelled the growth of E-commerce. Consequently making
it much easier to do business over the internet and reach mass audiences
globally and even in remote places.
E-commerce is now part of our lives and companies trading via
the internet are exposed in a high speed changing environment where business
opportunities changed frequently, according to the customer needs and
technology innovations.
How this technology can be implemented in least developed
country with poor telecommunication infrastructure, poor electronic payment
systems, lack of regulation and capabilities in the subject matter?
Despite the fact that many studies focused on showing that
less developed countries face a lack of telecommunication infrastructures and
electronic payment systems, recent developments of mobile telephony in Africa
change the way e-commerce can be perceived in this part of World because of the
opportunities discovered in this emerged market.
So the question is not only about the infrastructures for
e-commerce, which really exist, but in term of the existence of capabilities
for e-commerce and how they can be leverage to develop the e-commerce.
I.2. Motivation of the subject
E-commerce is a new form of digital economy development where
no physical boundary and face-to-face interaction are necessary to do
commercial transaction.
In the Democratic republic of Congo (DRC), the fact that the
growth of mobile technology and the large penetration of mobile telephony
companies in the country, despite the fact that the telecommunication
infrastructure in not well developed, can constitute an opportunity for the
e-commerce development.
However, there is no research available to assess effectively
the capabilities readiness of the country for the development of e-commerce.
The aim of this work is to assess if adequate e-commerce
capabilities exist in the country and how they can be leveraged to the
development of e-commerce. The focus will be given to the payment systems and
their security.
I.3. Page | 7
Problem Statement
E-commerce is related to Internet technologies and electronic
payment systems which are not well developed in most of the least developed
countries like the Democratic republic of Congo (DRC). However, the development
of the mobile telephony market offers some opportunities of getting internet
access and m-commerce facilities in most of urban and suburban areas with high
concentration of population.
The objective of this work is to define how e-commerce can be
implemented in DRC taking into account all constraints of e-commerce
capabilities.
Because the internet access in only present in urban areas,
the research will focus only on companies located in such areas.
The poor penetration of the internet and the lack of
electronic payment systems can be recognized as a detriment to the development
of e-business in the country. Even if there is a regulation board for
telecommunication and information technology, there are no rules defined for
electronic commerce and electronic payment.
I.4. Research Question
Among many research questions which can be raised in the
e-commerce field in the developing country like DRC, the choice for this
research is to respond to the most fundamental question regarding e-commerce
capabilities.
Do adequate e-commerce capabilities exist in the
country and how to leverage them to the development of e-commerce? Does
adequate security of payment systems exist in order to promote online
payment?
I.5. Scope and limitation
This research in not intended to examine all capabilities
involved in the development of e-commerce. According to the actual stage of
telecommunication infrastructure development in the country, the adoption of
the mobile telephony system as primary telecommunication media and the
opportunity currently exploited by three major operators in mobile fund
transfer system, the scope of this work will be limited to the main
capabilities which are likely to be preponderant to an effective e-commerce
development.
The following capabilities will be covered by the study:
1. Information and communication technology (ICT) which will
include telecoms and computer infrastructure.
2. Payment systems capabilities which must be used for online
transactions.
3. Security of the identified payment systems which can be
used for the development of e-commerce.
Of course some aspect of regulation will be considered also as
governance capabilities.
Page | 8
The study will be limited to the capital city of the country,
Kinshasa, where there is a potentiality of e-commerce development according to
the fact it is the first business center in the country where most of big
businesses and banks have their head quarters.
Findings and recommendations will be then easily replicated to
the most of urban areas of the country where minimal capabilities are
available.
I.6. Methodology
There are no available statistics published in the country
about e-commerce; the e-commerce is not yet in inception phase. This work will
be among the first step in the research about the e-commerce development in the
country.
Therefore, the objective of the research can only be achieved
by collecting data from different available sources of information in areas
where e-commerce capabilities are likely to be present ; academic researches,
special journal in IS and web resources. The research will also use data
collected from survey via interviews of organizations which will be involved in
the e-commerce development, mostly banks, regulation board and Mobile
operators.
Page | 9
Chapter 2: Literature review
II.1. Introduction
This chapter will discuss e-commerce terminologies involve in
the good understanding of the key concepts of e-commerce like its definition,
forms and organization. It'll also provide a clear understanding of
capabilities which are necessary for the development of e-commerce.
There are a lot of reading resources available covering the
e-commerce subject but a very few manual about e-commerce capabilities have
been available for this research. Most of available information has been
collected through master or doctoral thesis and form special technological
journal.
II.2. Definition of e-commerce
Many authors defined e-commerce by designing a commercial
activity conducted by the use of internet and/or electronic systems (Turban et
al. 2008, Laudon and Laudon, 2006, Cobham, 2005).
Among the definitions chosen, Turban et al. (2008: p4)
describe e-commerce as «a process of buying, selling, transferring, or
exchanging products, services, and/or information via computer networks,
including the Internet».
The Laudon's used the term Internet and web for the business
transaction to define e-commerce (K. Laudon & J. Laudon, 2006), while a
year before Graham Curtis and David Cobham (2005, p212) defined e-commerce in
its broadest context as «any exchange of information or business
transaction that is facilitated by the use of information and communication
technologies».
In the same vision as Curtis and Cobham, Beynon-Davies (2002)
separate the concept e-commerce which constitute the exchange of goods and
services between businesses, individuals or groups by the use of Information
and Communication technology (ICT) and I-commerce which is the use of internet
technologies to enable e-commerce.
It means that the development of e-commerce couldn't be
possible without the development of ICT and specially the Internet technology
which is one of the key drivers for e-commerce development.
Page | 10
II.3. Types of e-commerce
It is better to know how e-commerce is classified to
understand the different business models provided by this new economy.
Turban et al. 2008, K. Laudon and J. Laudon, 2006, David
Cobham, 2005) classify electronic commerce by the nature or the way the
participants involve in the electronic transaction. According to this point of
view, three forms of e-commerce are identified:
1. Business-to-consumer e-commerce (B2C)
2. Business-to-business e-commerce (B2B)
3. Consumer-to-consumer e-commerce (C)
However, with the development of mobile and wireless
technologies, the use of e-commerce, which was primarily conducted through
fixed computers and networked terminals, can now be conducted wirelessly. This
new development gives a new concept of e-commerce called Mobile commerce or
m-commerce (Turban et al. 2008).
II.3.1. B2C e-commerce
It is an e-commerce between a company and its customers (Paul
Beynon-Davies, 2002). Turban et al. (2008) and Kenneth C. Laudon and Jane P.
Laudon (2006) also describe B2C e-commerce as retailing transaction of goods or
services from a business to individual shoppers.
In this category of e-commerce, customers are using ICT
capabilities to buy goods and/or services from businesses and making payment
online without intermediary.
This kind of e-commerce is the most suitable to the less
developed countries because of its ease of implementation. In fact, in this
e-commerce model the infrastructure is not so sophisticated like for the B2B
e-commerce which requires advanced technology for the interaction among
business partners.
In this model, customer needs just internet connectivity and
web browser (special program to read web page) to participate to e-commerce
transactions.
Page |11
II.3.2. B2B e-commerce
As it is cleared described in the designation, B2B e-commerce
involves participation of businesses or organizations in the e-commerce
transaction.
Turban & al. (2008: p219) defines B2B e-commerce as
«transactions between businesses conducted electronically over the
internet, extranets, intranets, or private networks».
This definition shows implication of advanced technologies
which are used in the B2B e-commerce to support and operate transactions among
businesses.
II.3.3. C e-commerce
C e-commerce is the form of e-commerce where participants to
electronic transactions are individuals, not businesses.
It is «e-commerce model in which consumers sell directly
to other consumers» (Turban et al. 2008, p400).
Because consumers can't have their own infrastructure to
implement a particular e-commerce infrastructure, this form of e-commerce in
conducted using auctions which are implemented by specialized
intermediaries.
Figure 1: form of e-commerce
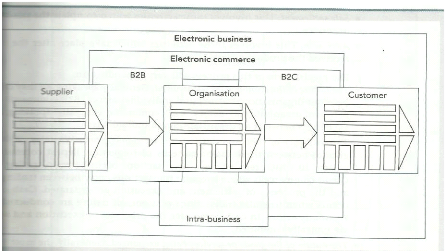
Source Paul Beynon-Davies (2002, p 487)
II.4. Page | 12
Mobile Commerce (M-commerce)
The definitions of e-commerce given in previous sections
stated the use of ICT to conduct commercial transaction; these technologies use
fixed computer or network access terminal.
Turban et al. (2008, p431) defines Mobile commerce as
«any business activity conducted via wireless telecommunications network.
This includes B2C and B2B commercial transaction as well as the transfer of
information and services via wireless mobile devices».
The advert of Smartphones with full keyboard capabilities and
web browser application, coupled to the new standards of broadband mobile
telecommunication (3G and 4G) which offer large bandwidth on handheld
equipments make the technology mature to conduct business online with
mobility.
II.5. E-commerce capabilities overview
Technology plays a major role in the development of the
e-commerce. However, regarding the nature of the e-commerce activity, many
other capabilities must be considered for the development of e-commerce.
To better understand capabilities concept in e-commerce it is
good to have a clear understanding of e-commerce framework as described in the
figure below.
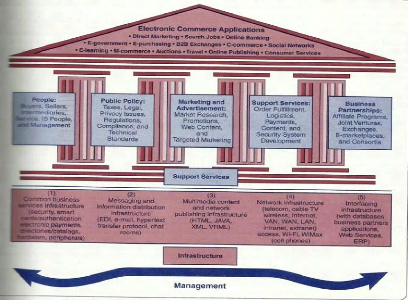
Fig 2. E-commerce framework. Source Turban et al. (2008, p7)
Page | 13
In this framework the e-commerce is represented like a
building with three main components:
- Roof: represents the e-commerce applications
- Walls: which sustain applications represent all support
services for the e-commerce
- Foundation: represents the e-commerce infrastructure.
All these capabilities must be managed and governed in a best
way for a successful e-commerce development.
For the context of this study, payment systems can be included
in the IT capabilities for the nature of the infrastructure used for the
payment systems. Their importance for e-commerce development motivates the
choice of studying it as particular capability because it is a vital part of
the e-commerce infrastructure.
II.6. Information system capabilities
II.6.1. Introduction
This section will present definitions of capabilities and
resources which are two concepts which will be used in this work regarding
capabilities.
Day (1994) and Grant (1996) cited by Abhay N. Misha and Ritu
Argarwal (2010) define capabilities as «firms capabilities, skills, and
accumulated knowledge that enable it to repeatedly perform task that create
value».
It emerges from this definition the concept of resource which
includes «all assets, capabilities, organizational process, attributes,
information knowledge, etc, controlled by a firm that enable the firm to
conceive and implement strategies that improve its efficiency and effectiveness
(Draft 1983)» (Barney 1991,p101) cited by Aurelio Raverini (2010).
II.6.2. Information system (IS) capabilities
overview
Resources and capabilities in information system concept can
be «termed as Information system capabilities» which are
«skills, competences and abilities, upon which the value of the physical
Information technology (IT) resource can be leveraged» (N.F. Doherty and
M. Therry, 2009, p4).
According to Collis, D. J.(1994) cited by T. Ravichandran and
C. Lertwomgsatien (2005), «capabilities are social complex routines that
determine the efficiency with which firms transform inputs into
outputs».
Page | 14
Figure 3. Initial structure of IT capabilities (Bharadwaj,
1999)
Source: A Raverini (2010, p87)
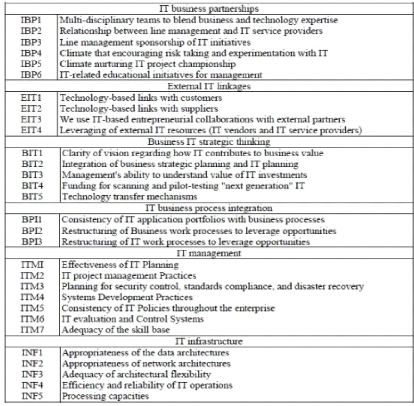
In his research A. Raverini (2010, p.99) gives a broadest and
complete definition of IT capability in these terms: «IT capability is the
capacity, diffused within the whole organization, to plan, use and manage the
resources based on IT-complementarily and jointly with the other resources and
capacities of the organization- in order to achieve a specific organizational
objective and obtain a competitive and sustainable advantage over
competitors».
Page | 15
II.6.3. Information system capabilities in the scope of
e-commerce
II.6.3.1 Overview of the information system capabilities
for e-commerce
According to the framework presented by Turban (Turban et al.
2008, p7), among the five (5) groups of infrastructures presented in his book,
the first category called «Common business services infrastructures»
includes; security, smart card/authentication, electronic payments,
directories/catalogs, hardware and peripherals.
From this framework, this study will focus on the security of
e-payment systems because it is the core of the electronic commerce capability
which allows the concretization of the transaction.
From this choice of e-payment systems as a prime focus of this
research, another implication is that it is not easy to talk about electronic
payment systems that are using IT capabilities (systems, software, and human)
without having a look at the way online transactions are to be secured in order
to enable effective e-commerce development.
That's why this particular aspect of the IT capabilities of
e-payment systems which consists on security of online payment system is the
focus of this research about e-commerce capabilities readiness in DRC.
The target of this research in the bank sector will be focused
on the following payment systems; online banking payment system and the local
(private) and international well known bank cards provided by local commercial
banks.
It must be understood that in the scope of this research, some
local banks are using well known international cards such as Visa and
MasterCard that are used worldwide as payment system (online and offline) and
therefore providing some confidence to the user because of their brand name
recognition and the existence of payment systems installed at the banks and
shops.
This study will also assess the security readiness of the
e-payments systems and any other online payment system proposed by local
commercial banks in order to leverage them for an effective e-payment system
for the development of e-commerce in RDC.
Also, as stated previously in this section, the advert of
mobile network with gsm operator providing money transfer facility via mobile
phone handsets, a new e-payment system is born in the country which is of big
interest on e-commerce development; mobile payment which is described below.
Page | 16
II.6.3.2 Mobile payment (M-payment)
The development of mobile network opens an opportunity to
mobile operators to provide money transfer and payment system facilities using
available communication credit loaded into the sim card.
Mobile phone users can then, as for the stored-value card,
store money as telecommunication credit in their mobile phone which can be used
to pay goods and services to merchants, participating as partners of mobile
operators.
In DRC, some mobile operators are working with banks to link
m-payment account to real bank account.
This payment system is used to pay salaries for public
administration's staff in areas without banking facilities.
Because this activity is not developed by the government;
regulation is the main concern for this payment system. However, in this study,
as for the other e-payment systems described in the research, security of the
m-payment system will be assessed for its effective participation in e-commerce
transaction.
II.6.4. Information technology infrastructure for
e-commerce
E-commerce, as defined earlier in this work embedded new
processes which require necessary physical IT infrastructure, managerial and
organizational capabilities in order to succeed.
All definitions of e-commerce show its dependency to
information system infrastructure and processes to conduct business activities
online. There is an evident relationship between e-commerce capabilities and IS
infrastructure (Kevin Zhu, 2004).
P. Weill and M. Broadbent (1998) cited by Kevin Zhu (2004)
define IT infrastructure as a technology platform and information foundation
from which enterprise applications emanate and it includes «hardware,
software, networks, and data processing architecture».
E-payment systems will use IT infrastructure to enable
processing of payment transactions
Figure 4: IT infrastructure component.
Source: Kenneth C. Laudon and Jane P. Laudon, 2006, p185
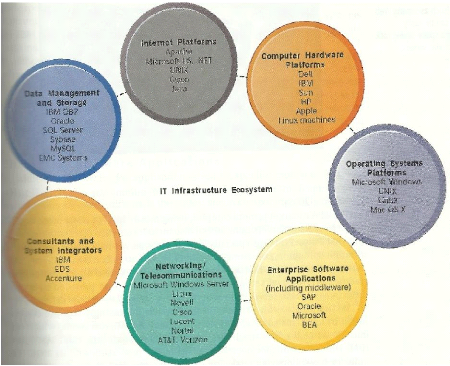
Page | 17
Page | 18
II.7. IT security capabilities for e-commerce II.7.1
Introduction
There are many capabilities required and needed to implement an
effective e-commerce business, among which most important are:
+ Web servers hardware and software
+ Electronic commerce software
+ Electronic commerce security systems
+ Electronic commerce payment systems
II.7.2 Security of online payment systems used for
e-commerce
E-commerce security is a vast subject covering:
+ Securing online transaction
+ Securing clients computers and internet access devices like PDA
and smart
phone.
+ Securing communication channels between computers
+ Securing servers.
Security, in the context of e-commerce is an important attribute
and one of the key
elements for its adoption, that's why server infrastructure and
software used for e-
commerce need to be secured.
The security framework of the information technology which is
considered in this
research is ISO 27001 framework that presents eleven (11)
high-level objectives for
the security standards (Timothy P. Layton, 2007, pp77-113):
O Security policy
O Organization of information security
O Asset management
O Human resources security
O Physical and environment security
O Communications and operations management
O Access control
O Information systems acquisition, development and maintenance
O Information security incident management
O Business continuity management
O Compliance.
Page | 19
II.7.2.1 Overview of the framework for security and
control of Information system
For the security of information technology, protection of
information resources is defined through a set of standards for security and
controls published as norm by the International Standards Organization (ISO)
and the International Electro technical Commission (IEC), grouped in joint
committee, under the norm ISO/IEC 17799 which is the reference code of practice
about the security of information system (Kenneth C. Laudon and Jane P. Laudon,
2006 and Anthony Tarantino, 2008).
The definition of the international security management system
(ISMS) standard under the reference ISO/IEC 27001:2005 (called ISO 27001) in
replacement of the British standard institute code of conduct in IS security
«BS 77799-2:2002» inaugurates the new era of information security
management (Anthony Tarantino, 2008, p169).
ISO 27001 titled «Information technology -
security techniques - information security management systems -
requirements», is not a technical specification but a management
system which is a first of international security standards, defined by ISO
which have number series ISO 27000 (A. Tarantino, opcit, p172).
The ISO/IEC 17799:2005 (ISO 17799) later named ISO 27002, has
been developed under the title «Information technology - security
techniques - code of practice for information security
management» as a set of guidelines for the implementation of the
ISO 27001security standards.
According to ISO 27002, there are three fundamental attributes
of an information asset (data representing a value for an organization);
confidentiality, availability and integrity which can
be impacted by risks from a wide range of threats: fraud or criminal activity,
system failure, user errors, etc (A. Tarantino, 2008, p174).
For this research the concept of security of the information
is the one provided by ISO 27002: «information is characterized within ISO
17799» (ISO 27002) «as the preservation of:
? Confidentiality - Ensuring that information is accessible
only to those authorized to have access to it,
? Integrity - safeguarding the accuracy and completeness of
information and processing methods,
? Availability-Ensuring that authorized users have access to
information and
associated assets when required» (IT Governance Institute,
2006).
II.7.2.2 Security of online e-commerce transaction
The highest worry about e-commerce users is that their
personal information, especially credit card number, bank account details, can
be stolen when proceeding online transaction or on the server of the company
running the online business.
According to Timothy P. Layton (2007, p100), ISO 27001
controls about e-commerce include fraud, insurance, confidentiality,
and authorization to data access while the control related to online
transaction is related to «the security and protection of data and
information involved in network transactions».
II.7.2.3 Security Policy
Why security policy is important in the context of security of
e-payment systems?
As described above in this research, security of Information
system is defined within a framework of guidance and requirements developed by
ISO/IEC under the ISO 27001/2 framework for the development of an Information
Security System Management (ISMS).
Figure 5: Level of acceptable security for
e-commerce
Source: Gary Schneider, 2011, p443
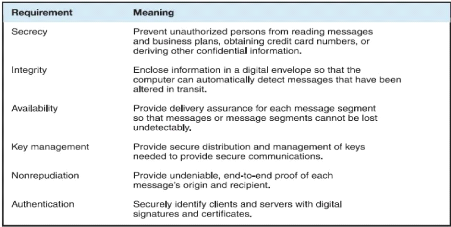
Page | 20
Page | 21
The most important for the security policy development is to
make sure that answers can be provided to the following questions:
V' Who is accessing the site? => Authentication of
the user
V' Who is allowed to connect and access to the site?
=> Access control V' Who is granted access to information? =>
Confidentiality or security V' Who is allowed to modify information?
=> Integrity
V' Who or what causes a specific event to occur on
the system and when it happens? => Audit
These fundamental questions will be the drivers for en
effective security policy implementation for an e-commerce information
system.
II.7.2.4 Computer security overview
This research considers computer security in the context of
all kinds of threats that an information system can face that is able to
destroy abuse or corrupt the information: unauthorized access, use,
modification or deletion of information.
To protect against threat, countermeasure; «physical or
logical procedure that recognizes, reduces, or eliminates a threat», must
be taken to ensure that the risk associated to the so called threat is
mitigated. (Gary Schneider, 2011, p440).
In today's computer use, the big threat is called hackers or
crackers who are able to break security of information system and gain
unauthorized access to computers or servers to steal information or damage the
system.
II.7.2.5 Overview of the client computer security
Client computers (laptop and desktop) or wireless devices are
used to connect to the internet in order to participate to the e-commerce.
These client machines or devices must be protected against threats or harmful
programs contained in web sites.
In this section an overview of web sites contents which
represent a threat to the client computers such as cookies, web bugs, active
contents, java applets, java script, active control, and graphics or plug in,
viruses and worms will be discussed.
Cookies
In the context of security, the definition that describes well
cookie is provided by Turban (Turban et al., 2006, p.165) who defines a cookie
as «a data file that is placed on a user's hard drive by a remote web
server, frequently without disclosure or the user's consent that collects
information about the user's activities at the site».
This definition states clearly that a cookie is like a spy who
observes user's online activity, therefore susceptible to illegal activity on a
client machine.
Page | 22
For e-commerce, web server's cookies store useful information
about user activity such as shopping card information which will be required by
the payment processing system.
Web bugs
Turban et al. (2006) and G. Schneider (2011) identify web bugs
as «tiny graphics» which can be embedded in web pages or emails to
store cookies on a user's computer in order to monitor his activity on the
web.
Active content, java applets, active
control
G. Schneider (2011, p446) defines active content as
«program that are embedded transparently in web pages and cause action to
occurs», to extend the functionality of html.
In the context of e-commerce, active content permits for
example to place items in a shopping cart, calculate the total amount of the
invoice and deduct the tax, add shipping cost and any other fees automatically
when a user shop online.
Active content can be java applets, JavaScript, Vbscript and
active controls which are used on the web site to implement automation or
execution of some actions.
Activex control is to be associated to object on the web page
in which programs and properties have been embedded.
Active content, java applets, active control can implement
malicious instructions which can break security of the client computers.
Viruses, worms, antivirus
Virus is program that attaches itself to another program in
the computer to cause damage in the host computer every time when this
application program will be executed.
A worm is a «type of virus that replicates itself on the
host machine» to spread out the infection. (G. Schneider, 2011).
The countermeasure against virus and worm is antivirus
software installed on all computers and servers in the network.
Page | 23
Digital certificate, digital
signature
Like for the epistolary communication with signed letters or
documents to identify the sender by its signature, electronic communication
uses digital signature in place of the personal signature.
Digital signature uses the encryption technology to ensure
that only authenticated users can access to the resource.
Digital certificate or digital ID is defined by G. Schneider
(2011, p455) as «an attachment to an email message or a program embedded
in a web page that verifies that the sender or web site is who or what it
claims to be».
Digital signature and digital certificate are used to ensure
confidentiality of the transaction on the web site; they can help to ensure
secured online transaction for e-commerce.
II.7.2.6 Overview of the security of the communication
channel
Data packets flowing to the internet are not using the same
path to reach the server. Information sent over the net can be intercepted,
altered or deleted before it can reach the receiver.
E-commerce will face integrity, confidentiality and
availability threat inherent to the nature of the Internet as communication
channel.
Confidentiality threat
The main concern of confidentiality is to make sure that
information is protected against unauthorized disclosure, while the privacy is
concerned by the legal instrument and policy to ensure the protection of
private information.
The theft of sensitive information or personal data such as
credit card number, names, and addresses is one of the most important threats
for e-commerce. Therefore, e-commerce infrastructure must address this threat
with highest priority.
One of the technology solutions used to ensure data
confidentiality is the encryption tools and solutions.
What is the encryption?
In this study, the definition given by G. Schneider (2011,
p465) is considered: «Encryption is the coding of information by using a
mathematically based program and a secret key to produce a string of characters
that is unintelligible».
Encrypted information can travel around the internet to ensure
that it can't be disclosed easily.
Page | 24
Integrity threats
An integrity threat appears when information or data can be
object of unauthorized modification, alteration, creation or deletion.
Cyber vandalism is one of the examples of integrity violation
because it destroys or modifies information on existing web sites.
Integrity prevention can be achieved by intrusion
detection systems which monitor suspicious activity on the network or
computer to prevent unauthorized access to information stored on the system or
transmitted on the network.
Availability threats
Turban et al. (2006, p517) defines availability as
«assurance that access to data, website, or other electronic commerce data
service is timely, available, reliable, and restricted to authorized
users».
The availability threat consists of all events which cause
delay or deny access to data. The most known is the Denial-of-Service (DOS)
attack which trouble normal operation of a computer or server and can conduct
on abnormal slowness of the server, network or electronic systems such as
Automated Teller Machine (ATM).
E-payment systems must be protected by IDS or Firewall able to
stop these kinds of attacks.
Authentication, authorization and non repudiation
To conclude on the communication channels, it is clearly
described in the previous sections that e-commerce relies on the
confidentiality, integrity and availability (CIA) of information and the
business web site (Turban et al., 2008, p. 517).
These functions depend on the authentication which is a
process to «assure the real identity of an entity which can be a user
computer, program, website or any Information resource (Turban et al. 2008, p
517).
Authorization is the process of ensuring that the
authenticated entity has been granted rights to access resource and which
operations it'll perform on it.
The non repudiation will ensure that authenticated entity
cannot falsely deny action it conducts online.
For e-commerce perspective non repudiation will be the
«assurance that online customers or trading partners cannot falsely deny
(repudiate) their purchases or transactions». (Turban et al, 2008,
p518).
Page | 25
Threats to physical security of the internet
communication channels The packet-switching infrastructure permits
to have many links to the internet.
In case of physical attack to one of the link; data packets
will be routed to another link to the internet.
For e-commerce business the countermeasure to this threat
will be to use redundant links to different Internet Service Providers
(ISPs) which in their turn have many different links to
internet.
Threat to Wireless network
Wireless access points (WAP) provide network connectivity to
computer (mostly laptops) and other mobile devices within a short range of
hundred meters to access to a shared resource, in the case of this study, the
internet.
If the wireless access point is not protected, anyone can
connect to the network and gain access to the resources on the network.
The security on wireless is implemented via a wireless
encryption protocol (WEP) which permits to encrypt and decrypt data over
wireless transmission.
Threat to server computer
There is no system which can be hundred percent secured, even
if strong security policies and measures are implemented, web servers will have
vulnerabilities which can be exploited to compromise them.
The confidentiality can be compromised by the web server
itself if it allows automatic display of directory listings and the folder
names are revealed to the web browser. (G. Schneider, 2011, p.474).
Web servers are connected to back-end storage server (database
servers) where valuable information about products and customers are stored; in
case of unauthorized access, that information can be disclosed.
Modern database management systems (DBMS) have security
features to authenticate users. This login information can be stolen by hidden
malicious programs installed by hackers in the servers.
Also, some organization will keep default DBMS credentials
which are provided by the editor; this will keep a security hole to the
database which can be exploiting by the hackers.
Page | 26
II.7.3. Overview of security of E-commerce network
In the previous sections, the research presents an overview of
threats that e-commerce and e-payment systems are likely to face.
Because of the diversity of threats and the way the networks are
attacked in today's internet era, organization or business cannot rely on a
single security technology; it must use security technologies at different
layers of the network.
Figure 7 below shows the three layers of the network which needs
to be protected.
Figure 6: layered security
Source: Turban et al. 2008, p 532
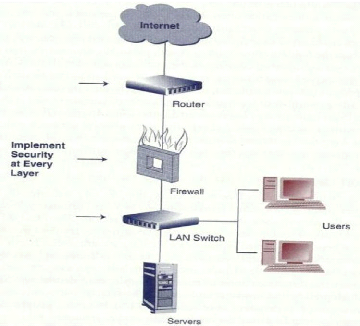
- Router level : perimeter security to internet
- Firewall: isolation of traffic communication between the
internet and the LAN - LAN switch: access security on local resources
Page | 27
II.7.3.1 Firewalls
Turban et al. (2008, p 533) defines firewall as a network
resource «consisting of both hardware and software that isolates a private
network from a public network».
Firewall examines all packets passing through it and allows or
denies the traffic according to the rules defined by the network
administrator.
Firewall can protect against many threats such as unauthorized
access, viruses, spams, harmful macro, applications backdoors, etc.
In e-commerce environment, firewall is used to block all
packets coming from un-trusted source or accessing to a specific resource on
the LAN.
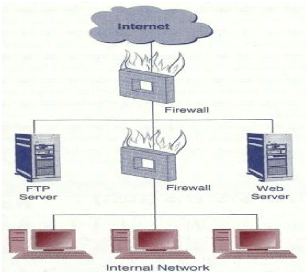
II.7.3.2 Demilitarized zone (DMZ)
Demilitarized zone is defined by Turban (Turban et al., 2008,
p534) as «a network area that sits between an organization's internal
network and the internet, providing physical isolation between the two networks
that is controlled by rules enforced by a firewall».
In e-commerce infrastructure web server will sit in the DMZ,
publicly accessible area and the database server will be installed in the
internal LAN protected by another firewall. In such deployment, network has two
firewalls to hardener the security.
Figure 7: DMZ deployment
Source: Turban et al.,2008, p535
Page | 28
II.7.3.3 Personal firewalls
Actually many home users have broadband connection to the
internet which allows them to get permanent connection to the Internet. This
permanent exposure to internet expose computer to attacks.
Personal firewall have been developed to protect desktop or
laptop by monitoring traffic flowing on the LAN interface card and taking
action according to the rule defined by the user.
II.7.3.4 Virtual Private Network (VPN)
G. Schneider (2011, p 86) defines a Virtual Private Network as
«an extranet that uses public networks and their protocols to send
sensitive data to partners, customers, suppliers, and employees using a system
called IP tunneling or encapsulation».
IP tunneling creates a private communication channels on the
internet in which information is encrypted to make it invisible to the other
internet users which are not involved in the communication transaction.
Protocol tunneling permits to encrypt data packets and
encapsulate them into packets to ensure confidentiality and integrity of data,
to be transmitted over the internet.
II.7.3.5 Overview of intrusion detection systems (IDS)
The necessity of monitoring the Information system for
unauthorized access permits the development of special systems and software
that can monitor activity on the network and detect illegal activities.
These appliances and software are called Intrusion prevention
system (IDS). II.8. Securing e-payment systems for B2C e-commerce
E-commerce needs a special payment system to enable online
payment of goods and services sold online.
According to the Laudon's (Kenneth C. Laudon and Jane P.
Laudon, 2006, p416), «electronic payment systems for the internet include
systems for digital credit card payments, digital wallets, accumulated balance
payment systems, store value payment systems, digital cash, peer-to-peer
payment systems, digital checking and electronic billing presentment
systems».
With the development of mobile telephony, another payment
system is available and consists of paying good and service using mobile phone.
This is known as m-payment system and will be developed shortly in e-commerce
transaction.
Page | 29
II.8.1 Payment cards systems
Payment cards are cards with payment of financial information
embedded in an electronic chip and which can be used for payment.
Three kinds of cars are currently used: (Turban et al., 2008,
p551)
? Credit card ? Debit
? Charge card
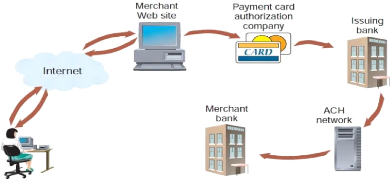
Card processing overview
Card payment processing consists on authorization of the
transaction and the settlement of the money.
Authorization is the phase during which verification is done to
check the validity of the card and the availability of the fund to be paid for
the transaction.
Settlement is the phase which consists on the transfer of money
from the buyer's card bank account to the seller's account.
Payment processing is a service offered by payment processing
service Provider (PSP).
Figure 8: Processing of a card transaction
Source: Gary
Schneider, 2011, p.501
Page | 30
The most threat for payment card is «the
fraud»; and tools have been developed to combat it (Turban et
al., 2008, pp 553-554).
> Address verification system (AVS): seller compare the
shipping address entered on the e-commerce portal with the address contained in
file at the cardholder's bank.
> Manual review: staffs review manually suspicious
transactions orders to detect fraudulent transaction. This method can be used
on business with small amount of transactions.
> Fraud screens and automated decision models: Intelligent
systems which use automated rules to determine if the transaction can be
accepted rejected or suspended.
> Card verification number (CVN): this number is printed on
the back of the credit card; the verification will ensure that the buyer has
the card into his hands. This verification will not be useful in case of stolen
number.
> Card association payer authentication services. This
service is provided by card issuer and offers the possibility for the card
holder to register with the system to ensure the protection of the card.
Merchant web portal will interact with this service to validate the
authenticity of the card. Mastercard offers «Mastercard securecode»
and Visa the «verified by visa» to authenticate and certify their
cards.
> Negative file. Customer and information about the
connection such as IP address name, shipping or billing address, contact
numbers, etc are stored in a file. When the transaction takes place on the web
portal it is matched against the information contained in the file and flag in
case of problem.
II.8.2 Electronic cash
Electronic cash (e-cash or digital cash) is «a general
term that describes any value storage and exchange system created by a private
(non-governmental) entity that doesn't use paper documents or coins and that
can serve as a substitute for government issued physical currency» (G.
Schneider, 2011, p502).
Security issue of e-cash
As for the credit card payment, privacy and security
of the transaction is the most important issue for e-cash
implementation in the e-commerce business.
Fraud is a big concern for e-cash; therefore
security system must be in place to prevent double spending which can happen
while the electronic cash is submitted twice for the same cash amount to two
different merchants.
To prevent this situation, cryptographic algorithms are
creating tamperproof electronic cash that can trace back the transaction to its
origin.
Page | 31
The e-cash has a significant disadvantage because it doesn't
provide an audit trail and can be used as money-laundering (conversion of
illegal owned money to cash) system.
E-cash needs to be supported by a strong regulation to
define standards with the supported secured system and banking in order to be
widely accepted as an alternative to credit/debit card.
II.8.3. Stored-value card
Stored-value card looks like a credit/debit card and function
like credit/debit card, however it has a currency value (amount) preloaded in
the electronic chip or magnetic strip.
Same security concerns as for the credit card systems must be
addressed for this e-payment system.
. II.8.4 E-checking
E-check is a valid electronic copy of the paper check which
contains all information contained on the paper check; however it requires a
special infrastructure to be in place.
The processing of e-check is done by an Automatic Clearing House
(ACH) which has its Information system connected to the different banks.
Figure 9: E-checking processing using
Authorize.net
Source: Turban et
al. 2008, p 567
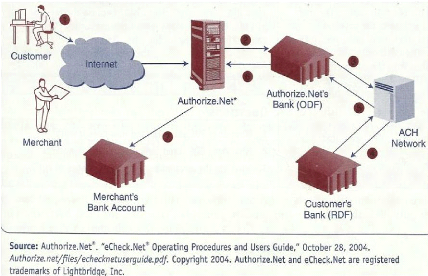
Page | 32
E-check security
As for the manual check, e-check security concern is the
fraud. The system must make sure that the check is signed by the authorized
person and the bank account has sufficient amount of money to pay the
transaction.
E-check payment system security will consist mostly on:
? digital signature and validity of e-check
? authorization of the transaction
? security of the transaction
? verification of the availability of the amount
? Effective policy to drive the ACH.
II.8.5 Security of M-payment
Mobile phone with integrated sim card which load encrypted
information, offers security and privacy, but for its use in the e-commerce
other security concerns have to be considered.
The lack of standards and disparity of the existing systems
are the main concerns for the use development of this payment system in online
transaction despite the fact that identification, security and authorization of
the transaction are already implemented in the m-payment systems.
To effectively use m-payment in e-commerce development, strong
partnership between banks, mobile operators and businesses must be developed
for the integration of their information systems to provide dynamic and secured
mobile payment system (P. Candance Deans, 2005, p 84).
This integration will raise issue of security of Information
systems that has been described in this work to ensure security of the online
transaction.
The nature of the mobile phone which can be stolen any time or
broken, the malfunction of mobile network because of technical issues will
surely raise issues such as fraud, repudiation of the transaction and
availability of service.
That's why, on top of all security measures which can be
implemented, this emerging system needs to have law and regulation in place.
Page | 33
II.9 Conclusion on the literature review
The literature review gives a broad view and understanding of
e-commerce concepts and Information technology capabilities.
Capabilities in e-commerce link together Information
technology capabilities with organizational processes to respond to the highly
changing nature of the e-commerce because of the dynamic changes involved in
its development.
The diversity of the payment systems studied in this research
and the challenge of their security is the fundamental element which will be
used in this research to assess the e-commerce capabilities in the Democratic
republic of Congo (DRC).
A particular attention will be given to the mobile payment
systems which appear as an emerging innovation in the country with the
development of the mobile networks.
The study will analyze the security of the existing e-payment
systems such as credit/debit card and other online payment offered by local
banks and their organizational processes to assess their readiness to the
emergence of e-commerce in DRC.
Security according to the CIA concept (Confidentiality,
integrity and availability) as described in the ISO 27001/2 framework and other
sources cited in the section II.7.2 of this work will be the driver for the
assessment which will be used in this study.
The objective of this research is to assess the status of
e-commerce capabilities in DRC with a specific focus on online payment systems
security in order to better understand how such capabilities can be better
leveraged for an effective development of e-commerce in DRC.
Page | 34
Chapter 3: Research Methodology
III.1 Introduction
This chapter discusses the methodology used to collect
information and the overall research design and justification. It also defines
the sampling; population used for data collection and the questionnaire
design.
The security of the payment system is the main concern which
must be addressed in order to bring confidence for the user. In their books
according to electronic payment systems for e-commerce the Laudon's (K. Laudon
and J Laundon, 2008) and G. Shneider (2011) presented the concept of CIA
(Confidentiality, integrity and availability) as a quality to which a payment
system must conform. So this research will use this concept to assess security
of online payment systems in DRC
The concept of the security of the information system as
provided by the ISO 27001/2 standards as described in the previous chapter of
this study highlights the important place taken by the CIA concept in terms of
the security of the online transaction used for the e-commerce in general and
particularly for e-payment systems. Of course the other elements of the
security focusing on human, physical infrastructure, etc are most likely to be
easy to set up and should exist in most of the bank IT infrastructure in the
country.
So CIA remains a challenge because as it is well known, all
other security elements regarding e-payment systems have as prime objective to
ensure confidentiality, integrity and availability of the system.
III.2 Research design and justification III.2.1
Introduction
The research design or methodology describes the process and
actions taken to collect responses or data and the way these responses have
been analyzed to give an answer the research question.
For this research, the literature review didn't provide
relevant information to the research question for this study; therefore it is
difficult to use secondary data collection method.
In fact, because of the specificity of the subject and the use
of component elements of a framework to assess the security of e-payment
systems in the specified country, the primary data collection method is the
best one for this research. Data (responses) will be collected directly from
participants to the survey which will use questionnaire built from
checklists.
Page | 35
E-commerce is on its inception phase in the country, therefore
it is not already perceived as part of the economical live. For this reason,
the research will also use interviews as to get some responses in a
face-to-face interaction with stakeholders in the e-payment and e-commerce
planet.
Prior to justify which methodology is better for this
research, it is better to give an overview of the two methodologies used for
data collection; qualitative and quantitative.
Qualitative research methodology
Jackson (2010, p 101) defines qualitative research as a
research method that «focuses on phenomena that occur in natural settings,
and the data are analyzed without the use of statistics.
«Qualitative research generates text which is often
interpreted in a subjective way (although it is possible in certain
circumstances to convert textual information to numbers)» (Gabriel J.,
2012).
These two definitions indicate clearly that qualitative
research is based on observation of specific field or area of research without
statistical analysis in the mind.
For qualitative research data or response is collected by the
mean of questionnaire or interviews.
Quantitative research methodology
It has been stated by professor G. Jacobs (2012) that
«quantitative research generates measurable information that can be
converted into numbers and analyzed statistically. Data is often gathered in
questionnaire surveys».
In quantitative research, even though data can be collected
some time using interview like for the qualitative methodology, the focus is to
simplify, objectify or quantify the observation so that data collected can be
easily interpreted using statistical tools.
The difference between the two methodologies is given in the
table below provided by Malhotra (2004, cited by Mirza et al. (2011, p 53-54))
based on objective, sample data collection and analysis and the outcome
basis.
Page | 36
Table 1: Qualitative vs quantitative research
methodologies
Source: Mirza et al. (2011, p53-54)
|
Basis
|
Qualitative
|
Quantitative
|
|
Objective
|
To gain the qualitative
understanding of the underlying reasons and motivation
|
To quantify the data and generalize the results from the sample
to the population of interest
|
|
Sample
|
Small number of non representative cases
|
Large number of representative cases
|
|
Data collection
|
unstructured
|
structured
|
|
Data analysis
|
Non statistical
|
statistical
|
|
Outcome
|
Developed an initial understanding
|
Recommend a final course of action
|
III.2.2 Choice of the methodology
The choice of the research methodology depends on the nature
of the research area and the way data have to be collected and analyzed.
The two methodologies present some similarities, such as:
(Sherril L. Jackson, 2010, p 106):
4 The researcher makes some type of inference based on data
collected 4 Data is analyzed in order to draw a conclusion
4 Findings are published so that they can be reviewed by
others.
However the data collection and the sampling methods are the
determinant elements for this research; because of the specificity of its
research question which is based on perceived values of the concept CIA
(confidentiality, integrity and availability) applied to the e-payment systems
in the DRC (Democratic republic of Congo).
These characteristics of the e-payment systems to be assessed
are most likely to be quantified. For example confidentiality perception can be
quantified by a scale of numbers; 5= confidential, 4=somehow confidential,
3=not applied, 2=unknown, 1=non confidential.
Of course for this research some interviews will be used to
clarify some concepts developed in the questionnaire to avoid misunderstood or
confusions in responses, however, depending on the way the questionnaire will
be structured by the use of checklist, responses will be easily translated into
quantified information.
Page | 37
For example to assess the availability of e-payment system,
the checklist can be used to determine either or not the system is redundant,
and if the redundancy consists on high availability system or not.
It appears, in the light of the two examples provided above,
quantitative research method is the most appropriate for this research because
the collected information or responses will be analyzed statistically to assess
at which extend the e-payment systems in DRC are compliant with the CIA
concept.
The structured data collection method, the statistical data
analysis and the primary data collection method through surveys which will be
used in this research confirm the choice of the quantitative research method
approach of this study.
III.3. Data collection and sampling III.3.1 Sampling
technique
It is clearly indicated in the previous section that this
research will use the survey as primary data collection method; this involves
the organization of participants to the survey by using sample of
representative population to ensure that collected data can be generalized for
a reliable conclusion.
There are two main ways to define a sampling; probability and
nonprobability. Sherril L. Jackson (2010, p117-118) defines these two sampling
techniques as follow.
? Probability sampling is «a sampling technique in which
each member of the population has an equal likelihood of being selected to be
part of the sample».
? Nonprobability sampling is «a sampling technique in
which individual members of the population do not have an equal likelihood of
being selected to be member of the sample».
Which sampling method to be used by this study?
According to what was defined previously about the choice of
the methodology regarding the specific nature of the research question, the
nonprobability sampling technique will be used.
However, there are two kinds of nonprobability; the
convenience sampling and the quota sampling (Sherril L. Jackson, 2010,
p119).
For this research, the quota sampling will be used because it
is the one which ensures that the sample is like the population in some
characteristics, but uses convenience sampling to obtain the participants»
(Sherril l. Jackson, 2010, p119).
Page | 38
The research question by its nature limits the participants to
the survey to: + Banking sector: where e-payment system are likely to be
installed
+ Mobile operators: developing and implementing m-payment
systems.
Within these two sectors, participants are chosen in the area
of security (management, regulation and implantation):
+ Executive level: because the «complexity and
criticality of information security and its governance demand that it be
elevated to the highest organizational levels. As a critical resource,
information must be treated like any other asset essential to the survival and
success of the organization» (IT governance institute, 2006)
+ IT department: in charge of implementation, management and
maintenance of the IS security
+ E-payment system manager/sales: dealing with customers in
terms of banking services offered to customers
+ Information system auditors: ensuring that security policy
are followed and ensure audit of the IS.
This structure of the sampling in this study shows that
definitely, the research is using the quota sampling technique.
III.3.2 Sampling definition
The survey will be conducted to sixteen (16) commercial banks
located in the capital city of the DRC (Kinshasa), the Central Bank of the DRC
and the three (3) main mobile operators offering m-payment services.
Commercial banks are those implementing e-payment systems and
offering e-payment services to customers while mobile operators are
implementing m-payment systems and offering m-payment services. On top of these
two organizations, the Central Bank is acting as the monetary authority in the
country and de facto regulator of the banking system in the country and
therefore in charge of defining e-payments regulation and rules.
Page | 39
For the commercial banks and the mobile operators sectors, the
sample will consist of:
> 1 C-level member (CEO or COO)
> 1 IT director or IT manager, the head of the IT
department
> 1 IT security officer within the IT department
> 1 e-payment or m-payment business system manager or sales
manager
> 1 Information system auditor
For the central bank, as the guarantor of the financial
regulation, answers will be provided by:
> 1 C-level or board member (Governor or Managing director)
> 1 Director in charge of regulation
> 1 Director in charge of operations
> 1 IT Director
> 1 IT Security officer
> 1 IS Auditor
This sampling definition ensures that all the existing
commercial banks in the country will participate in the survey and therefore
constitute the whole population of possible informants for this research. The
size of the sample for which we are expecting respondents for this survey is
101.
III.3.3 Data Collection method
For this research, the survey is the method of the data
collection.
Questionnaire uses closed-ended questions and checklists will use
likert rating scale which will provide all alternatives of the response.
The likert rating scale of 5 has been used for the alternative
responses in the way that 5 indicates the best option and 1 the worst option:
5=strongly agreed, 4=agree, 3=neutral, 2=disagree, 1=strongly disagree.
Surveys have been sent by email through the traditional mail
system (hands delivery to the reception) with an acknowledgement of the receipt
of the questionnaire.
For this reason, questions have been clearly explained to
allow self-explanation to the respondent. However, for the CEO and the IT
officer, some interviews have been requested to clarify particularity of
questions which have sensitive perception for them.
Page | 40
III.4. Data analysis method III.4.1 Introduction
Data collected through the survey have to be organized in such
way to be used by descriptive statistics tools because the research method used
is quantitative.
The first step consists of grouping data into tables;
therefore for this research the frequency distribution is the best method for
the organization of data collected.
The research question focuses on characteristics of e-payment
systems which are meaningful for its security. This limitation influences the
way collected data will be used to assess the security of e-payment systems.
In the literature review chapter, the research presented
elements that are likely to be considered in order to determine if the
information system on which e-payment system is built is compliant to the CIA
concept of this research.
Therefore, knowing the number of organizations involved in the
survey, the better way to represent the existence of specific element is the
frequency distribution. For example, the analysis will provide such information
like how many banks have firewall protecting their e-payment systems. This
information will be better represented in a frequency distribution.
The frequency distribution tables for some elements of the
survey will also be represented graphically using bars. Bar graphs will be used
instead of histogram because for this research responses collected through the
survey are «qualitative variable» which mean «categorical
variable for which each value represents a discrete category» (Sherril L.
Jackson, 2010, p218).
Page | 41
3.4.2 Data analysis technique
The descriptive statistics measures are most suitable to
analyze data for this research. Prior to mention which analysis technique is
used for this research, an overview of the three (3) main measures of central
tendency; mean, median and mode, is given in the table below.
Table 2: Types of central tendency measures
Source: Sherril
L. Jackson (2010, p225)
|
Mean
|
Median
|
Mode
|
|
Definition
|
The arithmetic average
|
The middle score in a distribution of scores organized from
highest to lowest or lowest to highest
|
The score occurring with greatest frequency
|
|
Use with
|
Interval and ration data
|
Ordinal, interval, and ratio data
|
Nominal, ordinal, interval or ratio
|
|
Cautions
|
Not for use with distribution with a few extreme score
|
|
Not q reliable measure of central tendency
|
For this research, data collected use the likert rating scale
with values ranging from 1 to 5; 5 being the best choice.
According to this rating, this research will use the mode as
data analysis technique because it is the appropriate method to assess the CIA
capability of the e-payment system by indicating the score occurring with the
highest frequency.
For example, if the survey returns that among sixteen (16)
banks 10 of them has a firewall in place, this information is more relevant
than the mean or the median.
However, to some extend, the mean can be used to define the
average of some capabilities according to the data collected and the element
which is assessed.
For example, to assess the existence of data backup capability
globally is the sample, it can be easier to say that this capability exists on
an average of 65%. This calculation uses the mean as data analysis technique to
assess the overall capability.
While the mode will be used to assess individual capability,
conclusion in the context of assessment of all the e-payments systems studied
will use the mean to state the average of organizations having such capability
implemented.
Page | 42
Chapter 4: Research findings
IV.1 Response rate
According to the sampling described in the previous chapter, a
questionnaire has been sent to sixteen (16) commercial banks and the three (3)
major mobile operators for five respondents per institution. This sampling gave
a number of ninety five (95) respondents. On top of this number, six
respondents were expected from the Central bank as regulator body of the
banking activity in the country.
From this sampling, only four (4) banks and two (2) mobile
operators responded to the questionnaire. From the banking sector, all expected
respondents filled the questionnaire while from the mobile operators, only one
CEO responded. This gives a total of twenty nine (29) respondents out of one
hundred and one (101), giving a response rate of 29 divided by 101,
representing 28.71% of response rate.
IV.2 Research findings
IV.2.1 Working experience of respondents
The number of years of experience of the respondents is key
information on the quality of the knowledge respondents possess in the subject
matter.
The table below summarizes the working experience of the
respondents
Table 3: repartition of respondents per working year
|
Year of experience
|
Number of respondent
|
percentage
|
|
<= 1
|
3
|
10.34%
|
|
1 - 5
|
5
|
17.24%
|
|
6 - 10
|
11
|
37.93%
|
|
>10
|
10
|
34.49%
|
|
Total
|
29
|
100%
|
From this table, more than 72% of respondents have more than 5
years of experience in the banking or e-payment sector and might have valuable
information in the use of electronic payment systems.
Page | 43
IV.2.2 Job position of respondents
The repartition of respondents according to their position in
the organization is given in the table below.
Table 4: Respondents by position in the company
|
Position
|
Number of respondent
|
percentage
|
|
CEO / Managing Director
|
5
|
17.24%
|
|
IT Director or IT Manager
|
6
|
20.69%
|
|
Information security Officer
|
6
|
20.69%
|
|
E-payment business manager
|
6
|
20.69%
|
|
Information system auditor
|
6
|
20.69%
|
|
Total
|
29
|
100%
|
The study results show that 41.38% of respondents occupy the
post within the IT department or Direction, 20.69% are business managers of
e-payment systems and 20.69% represent the IT auditor respondents. This implies
that respondents for this study have necessary technical and business expertise
in the e-payment system.
IV.2.3 E-payment services
The study reveals the e-payment methods in the table below.
Table 5: E-payment methods
|
services
|
Number of institutions
|
percentage
|
|
Visa
|
4
|
36.37%
|
|
Master Card
|
3
|
27.27%
|
|
Electronic cash (M-payment)
|
2
|
18.18%
|
|
Local debit card
|
2
|
18.18%
|
|
Total
|
|
100%
|
Page | 44
According to the table above, the most provided e-payment system
is Visa with 36% and MasterCard with 27% followed by M-payment and the local
debit card.
This result indicates that most of the banks use Visa or
MasterCard, both representing more than 63% of e-payment methods.
IV.2.3 Issues faced by e-payment systems
The table below indicates the main issues observed in the
different institutions assessed.
Table 6: List of issues faced by e-payment systems
|
Issues
|
Number of institutions
|
percentage
|
|
Fraud
|
4
|
18.18%
|
|
Theft
|
6
|
27.27%
|
|
Unavailability
|
6
|
27.27%
|
|
Disclosure of information
|
4
|
18.18%
|
|
Falsification
|
2
|
9.10%
|
|
Total
|
|
100%
|
The study reveals that all six institutions have faced issues
of theft of cards or mobile phones, and the unavailability of the e-payment
systems. These two main issues represent more than 54% of issues observed,
whereas the disclosure of confidential information represents 18% of total
responses and the falsification of the information is observed mostly on
m-payment system (9%).
Page | 45
IV.3 Specific findings regarding the Confidentiality,
Integrity, Availability (CIA) IV.3.1 Confidentiality
The confidentiality of the e-payment system is guaranteed by
the existence of the firewall and the encryption system in the network
infrastructure. The table below shows the results of the availability of these
two elements in the assessed organizations.
Table 7: Confidentiality elements
|
Element
|
Number of company
|
|
Firewall
|
6
|
|
Encryption
|
3
|
The study results show that 100% of the responding
institutions have a firewall installed in their IT infrastructure and 50% have
an encryption system deployed.
However, the integrity check of the firewall is an important
element to assess the real value of the firewall in the LAN infrastructure.
The table below shows the result of the integrity of the
e-payment systems reviewed. According to the likert scale used for the
questionnaire, the occurrence table of the integrity check of the firewall
configuration is provided per institution.
Table 8: Integrity check of the firewall configuration
|
Institution
|
Score
|
|
Bank 1
|
4
|
|
Bank 2
|
3
|
|
Bank 3
|
2
|
|
Bank 4
|
3
|
|
Mobile operator 1
|
2
|
|
Mobile operator 2
|
2
|
Page | 46
From the table above, the extracted table below shows how
often the configuration of the firewall is checked for integrity.
Table 9: Integrity check of the firewall configuration
|
Response / Score
|
Frequency
|
Percentage
|
|
Not sure / 2
|
3
|
50%
|
|
Monthly / 3
|
2
|
33.33%
|
|
Weekly / 4
|
1
|
16.67%
|
|
6
|
100%
|
This result shows that the most observed value is the score 2
(Not sure) which is the mode of this frequency distribution. This means that
50% of the observed institutions do not have an integrity check of the firewall
configuration in place increasing the vulnerability of the system. 33.33% have
a monthly check while only 16.67% have a weekly check.
So the integrity of the configuration of the firewall can be
compromised and it'll take at least a week to discover the exploit.
IV.3.2 Integrity
The integrity has to be assessed through the existence of
digital certificate system, authentication and authorization for data access,
and the protection against the virus.
Table 10: System integrity result
|
Capability
|
Number of institution
|
|
Digital certificate
|
1
|
|
Authentication
|
6
|
|
Authorization
|
6
|
|
Antivirus
|
6
|
|
|
The study result shows that the majority of assessed
institutions don't have a digital certificate system in place; only one of them
has a certificate server deployed.
Page | 47
The assessment of the integrity through the reporting of the
unauthorized attempts to sensitive data and physical access control to
computers hosting sensitive data is given in the table below.
Table 11: Reporting of unauthorized attempts to sensitive
data
|
Institution
|
Score
|
|
Bank 1
|
5
|
|
Bank 2
|
5
|
|
Bank 3
|
5
|
|
Bank 4
|
5
|
|
Mobile operator 1
|
2
|
|
Mobile operator 2
|
5
|
This table shows that the majority of the assessed companies have
a reporting system in place for unauthorized attempts to access sensitive
data.
However, the physical access control of the system holding
sensitive data is an important element to guarantee integrity of data.
Table 12: Additional physical access control
|
Institution
|
Score
|
|
Bank 1
|
2
|
|
Bank 2
|
2
|
|
Bank 3
|
1
|
|
Bank 4
|
1
|
|
Mobile operator 1
|
2
|
|
Mobile operator 2
|
1
|
The frequency distribution table of the additional physical
access control to system holding sensitive data is given in the table 13
below.
Table 13: Frequency distribution of additional physical access
control
|
Score
|
Frequency
|
Percentage
|
|
No / 1
|
3
|
50%
|
|
Not sure / 2
|
3
|
50%
|
|
6
|
100%
|
The table above shows that 100% of the assessed institutions
don't have a strict physical access control mechanism on top of logical access
controls for computers storing sensitive data. Even though unauthorized
attempts to sensitive data are reported, strong physical access control
mechanisms to computers systems holding sensitive data missed.
IV.3.3 Availability
Regarding the availability of e-payment system the study has
to provide input about key concepts which are likely to facilitate a system
recovery such as existence of uninterrupted power system, a formal contingency
or business resumption plan, and a backup facility for data and programs.
Table 14: Availability capabilities
|
Capability
|
Number of institutions
|
|
Uninterrupted power source
|
6
|
|
Data backup
|
6
|
|
Contingency plan
|
2
|
From the table above, all the responding institutions have
backup facilities for both data and power source in place. However the
availability of the system is sustained by a contingency or business resumption
plan, which is under development. This plan is available in only of the two
institutions contacted.
Page | 48
Page | 49
IV.4 Summary
This chapter presents a synthetic view of the status of the
security of the e-payment system in the country according to the CIA concepts
which are most important in the broadest view of the security of the
information system.
Table 15: Summary of the security capability
|
Description of capability
|
Status
|
|
Firewall
|
Available
|
|
Digital certificate
|
Not available
|
|
Antivirus protection
|
Available
|
|
Authentication
|
Available
|
|
Authorization
|
Available
|
|
Data backup
|
Available
|
|
Contingency Plan
|
Not available
|
Page | 50
Chapter 5: Conclusions and recommendations
V.1 Introduction
The previous chapter illustrated the status of the security of
the e-payment system through the results of the questionnaire collected in the
six institutions from which responses have been received.
This chapter discusses the conclusion and recommendations for
the effectiveness of the readiness of the banking system to really contribute
to the development of the e-commerce in the country by improving the security
of the e-payment system.
It will also make some recommendations to the use of this
research and the future researches on similar topics.
V.2 Conclusions
V.2.1 E-payment system
The two major players of the market are Visa and MasterCard.
Together, these two players represent more than 63% of e-payment methods used
in the country.
Because the security of these e-payment systems is not fully
handled by the IT infrastructure of the local banks, these two payment systems
provide a guaranty that e-commerce can be developed in the country using these
two e-payment channels. However, because this facility is linked to bank
account held by the local bank, the security of the IT infrastructure of local
banks become an imperative condition to the use of these two e-payment
systems.
V.2.2 E-payment system security
The summary given in the section 4.4 of the previous chapter
is the map representing the way of improvements in order to guaranty the
security of the e-payment system for an effective development of e-commerce.
V.2.2.1 Firewall
All the institutions have a firewall in their IT
infrastructure, however, it has been reported by this study that the integrity
check of the configuration of the firewall in not conducted on a daily basis.
According to this finding, the main security concern is to maintain the
integrity of the configuration of the firewall. The cost of the illegal access
can be very high because of the long delay of the check of the integrity of the
configuration of the firewall.
Page | 51
V.2.2.2 Digital Certificate
The study result reports that only one (1) among six (6)
assessed institutions has a certificate server installed. This means that in
most of these banks, electronic transactions are not signed. This implies high
risk of data falsification and transaction repudiation because the integrity of
data can't be guaranteed.
Commercial banks in DRC must implement digital certificate
infrastructure to ensure electronic transactions to be signed digitally to
enforce their integrity.
V.2.2.3 Antivirus
All the assessed IT systems have antivirus software installed
and managed to clean and fix all virus infection.
V.2.2.4 Authentication and Authorization
The study result reveals existence of authentication and
authorization facilities in all the assessed companies. However the physical
access control to the computers systems hosting very sensitive data need to be
addressed.
V.2.2.5 Contingency plan
E-payment systems, by their nature, must be accessible and
available any time. Their availability is one of the sine qua non conditions
for an effective use in e-commerce transaction.
Despite the fact that backup facilities exist for data and
power source, there is no written plan for business continuity. So in case of
failure, the e-payment systems can't be recovered in acceptable delay.
To illustrate this argument, during our research, one of the
mobile company assessed experienced a fire incident at one of its data center
and the m-payment system was affected during a period of five (5) days.
The availability of the e-payment system requires commercial
banks and mobile operators offering m-payment services to implement contingency
plan to improve the system recovery.
To answer to the main research question, from the
conclusions given above, it appears that the security of e-payment systems,
according the CIA concept used for this study, is yet to be implemented.
However, the two main fields of improvement are the integrity which is to be
enforced by the implementation of certificate servers and the availability
which must be sustained by a development of business contingency plans to
guarantee a quick recovery of the system in case of failure.
Page | 52
V.3. Recommendations
The main objective of this research was to investigate the
security of e-payment systems in the Democratic republic of Congo (DRC) to
assess their readiness for an effective development of e-commerce.
The security concept of the information system being wide, the
study focused on three major concepts; confidentiality, integrity and
availability.
In order to contribute really on the development of
e-commerce, commercial banks are recommended the following points:
1. The top management has to make sure that security plan is
developed in the bank regarding the e-payment system mostly to ensure that
e-payment system guarantee confidentiality, integrity of electronic
transactions, and availability of the e-payment system to allow its effective
use in e-commerce transaction.
2. The top management has to integrate the security of the
information system among the priority of their future IT infrastructure.
3. The e-commerce development will bring new business
opportunity for the banks and e-payment system is one of the strategic
components to ensure a competitive advantage in the sector. Therefore, plan
must be developed to anticipate the growth of this business in short term.
Therefore, improvement of security of e-payment system must be addressed as a
priority action.
4. E-payment systems must be developed with the aim to reduce
and fight against the main issues faced by the e-payment systems reported in
this study such as fraud, theft, unavailability and disclosure of sensitive
information.
V.4. Page | 53
Areas for further research
There are still many areas to cover in the field of the
security of the e-payment systems which can interest researchers such as
identity management, development of security policies and procedures,
regulation of the electronic transactions.
However, this study illustrated some other capabilities to
develop for an effective e-commerce development in the country. Among these
capabilities, support services for e-commerce such as order fulfillment,
logistics, and the development of the security systems are other areas of
interest for further studies.
This study has a merit of being among the first in the country
because the e-commerce development is yet in its inception phase. It will be
therefore subject to criticism for improvements to ensure that existing
e-payment systems be leveraged for an effective development of e-commerce in
the country.
V.5. Study limitations
The conclusion and recommendations of this study are to be
considered within the specific limitations and conditions under which the
research has been conducted such as sample of informants, data collection
method and the data analysis.
The seizing of the sample took into account only commercial
banks and mobile operator companies offering e-payment services in Kinshasa,
capital city of the DRC. The low response rate for this research is to be
considered also among the limitations from the conclusion drowned for this
study.
The responses received are related to the data collection
method used and the kind of questions used for the assessment. This study used
closed-end questions built from the check list provided by ISO 27001
frameworks. Not all the check lists have been used for this research but only
few of them considered as more relevant for the CIA security concept used in
this study.
The study uses the quantitative analysis method based on the
likert scale data collected through the questionnaire. According to the
research question, the research uses two mains statistical analysis tools such
as means and mode to assess the security capabilities observed. The limitations
of this method with such kind of assessment based on checklist are that
correlation or regression analysis can't be done because conclusions are
directly linked to scores corresponding to likert scales.
Page | 54
6: References and bibliography
Abhay N. Mishra and Ritu Agarwal (2010). Technological Frames
organizational capabilities, and IT use: An empirical investigation of
electronic procurement. Information System Research, Vol 21 No 2, pp
249-270
Anthony Tarantino (2008). Governance, risk, and Compliance
Handbook: Technology, Finance, environmental and international guidance and
best practices. Wiley & sons, New Jersey (USA)
Aurelio Raverini (2010). «Information technology capability
within small-medium enterprises». PhD Thesis. School of Computer and
security science of computing, health and science. Edith Cowan University,
Petth, Australia
Candance Deans P. (2005). E-commerce and M-commerce
Technologies. IRM Press. Hershey (USA)
Collis, D.J., Beath, C.M.; and Goodhue, D. (1996). Develop
long-term competitiveness through IT assets. Sloam management review, 38,
1 pp 31-45
Collis, D.J. (1994) research Note: How valuable are
organizational capabilities? Strategic management Journal, 15, 8 pp
143-152
Council of Europe (2011). Summary of the main messages and
outcomes of the conference prepared by the Council of Europe Secretariat.
«Our internet - our rights, our freedoms». Toward the Council of
Europe Strategy on Internet governance 20122015 [Online]. Available from
http://www.coe.int/informationsociety/conf2011/viennaconferencesummaryen.pdf
[Accessed 12/06/2013]
David A. Montagne (2010). Essentials of Online payment
security and fraud prevention In: Essentials series. 1st
Edition. Wiley & Sons, New Jersey (USA)
Donald O'Mahony and Michael A. Pierce (2001). Electronic
payment systems for e-commerce, Artech House Print on demand, 2 Sub
editions. ISBN-10 1580532686 (UK)
Efraim Turban and D. King (2011). Electronic Commerce 2012: A
managerial and social network perspectives, 7th Edition. Pearson-Prentice
Hall:USA
Prof Gabriel Jacobs (2012). A brief outline of research
expectations and processes. Robert Kennedy College, Unpublished.
Page | 55
Ganesh D, Bahatt and Varun Grover (2005). Type of information
technology capabilities and their role in competitive advantage: An empiric
study. Journal of Management Information systems Vol 22, No 2, pp
253-277
Gary P. Schneider (2011). Electronic Commerce,
9th edition. Cengage Learning, Boston
Graham Curtis and David Cobham (2005). Business
Information Systems. Analysis, Design an Practice. Fifth Edition. Prentice
Hall (Financial Time), Harlow (UK)
IT Governance Institute (2003). Board Briefing on IT
Governance. 2nd edition. It Governance Institute. Rolling
Meadows, IL USA.
IT Governance Institute (2006). Information security
governance: Guidance for Boards of Directors and Executive Management.
2nd edition. It Governance Institute. Rolling Meadows, IL
USA.
Jeffrey A. Ogden, Paul Benjamin Lowry, Kenneth J. Petersen,
and Phillip L. Carter (2008). «Explaining the Key Elements of Information
Systems-Based Supply-Chain Strategy That Are Necessary for Business-to-Business
Electronic Marketplace Survival,» Supply Chain Forum: An International
Journal, vol. 9(1), pp. 92-110.
Available from
http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1464522.
[accessed
28/04/2013]
Jeffrey Scott Ray (2011). «Using Effective E-Commerce
Strategies to Improve Organizational Performance». Social science Network
[Online]. November, 20 2011. Available from
http://papers.ssrn.com/sol3/papers.cfm?abstractid=2115064
[Accessed 21/04/2013]
Kenneth C. Laudon and C. Guercio (2011). E-Commerce
2012, 8th Edition. Pearson-Prentice Hall. New Jersey (USA)
Kenneth C. Laudon and Jane P. Laudon (2006). Management
information systems, Managing the digital firm, 10th edition. Pearson
education inc, New Jersey, USA
Kevin Zhu (2004). The complementarity of Information
technology infrastructure and e-commerce capability: A resource-based
assessment of their business value. Journal of management of Information
system. Summer 2004, Vol 21, No 1 pp 167 -202
Lior Fink (2011). How do IT capabilities create strategic
value? Toward greater integration of insights from reductionistic and holistic
approaches. European Journal of Information systems (2011) 20, pp16-33
Page | 56
Mirza K. Baig, Hussein Raza, Umer Farooq (2011).
«E-commerce adoption. A comparative study of Sweden and Pakistan».
Master Thesis. Linkopings University, Stockholm
Monideepa Tarafdar&Steven R. Gordon (2013). «How
information technology capabilities influence organizational innovation:
Exploratory findings from two case studies». Available from
http://is2.lse.ac.uk/asp/aspecis/20050014.pdf.
[accessed 28/04/2013]
Neil F. Doherty (2009). «The role of IS capabilities
in delivering sustainable improvements to competitive positioning».
Journal of Strategic Information Systems 19 (2009) 100-116.
Nikhilesh Dholakia and Nir Kshetri (2005). «World
Trade Point Federation: Bringing E-Commerce Capabilities to Developing
Nations» Social science research network.[Online] International Journal of
Cases on Electronic Commerce (IJCEC), Vol. 1, No. 1, pp. 39-53. Available
from
http://papers.ssrn.com/sol3/papers.cfm?abstractid=846464
[accessed 28/04/2013]
Nikhilesh Dholakia and Nir Kshetri (2005). «Social
science research network. Mobile Commerce as a Solution to the Global Digital
Divide: Selected Cases of e-Development.» November, 13 2005 [Online]
Available from
http://papers.ssrn.com/sol3/papers.cfm?abstractid=847184
[accessed 28/04/2013]
Paul Beynon-Davies (2002). Information systems. An
introduction to informatics in organisations. Palgrave MacMillan, New
York
Ravichandran T. and Chalermsak Lertwongsatien (2005).
Effect of IS resources and capabilities on firm perspective: a
resource-based perspective. Journal of Management Information system, Vol
21 no 24, pp 237-276
Rosli Mohamad and Noor Azizi Ismail (2009). «Social science
research network. Electronic Commerce Adoption in SME: The Trend of Prior
Studies, published in Journal of Internet Banking and Commerce, August 2009,
vol. 14, no.2. Available from
http://papers.ssrn.com/sol3/papers.cfm?abstract
id=1521290## [accessed 28/04/2013]
Sheril L. Jackson (2010). Research Methods. A modular
approach, 2d edition. Cengage Learning, Boston
Ting-Peng Liang and Jun-Jer You (2011). Resource-based
view in IS research: A meta-analysis. Pacifi Asia conference on
Information system, Pacis 2009 proceedings
Timothy P. Layton (2007). Information security: Design,
implementation, measure, and compliance. Auerbach publications, Floride
(USA)
Turban E., King D., Lee J., Viehland D. (2008). Electronic
Commerce: A Managerial Perspective. Prentice Hall: New Jersey, USA
Page | 57
7: Appendix
VII.1 List of abbreviation
ACH Automatic clearing house
ATM Automated teller machine
AVS Address verification system
B2B Business-to-business e-commerce
B2C Business-to-consumer e-commerce
C Consumer-to-consumer e-commerce
CEO Chief executive officer
CIA Confidentiality, integrity, availability
COO Chief operation officer
CVN Card verification number
DBMS Database management system
DMZ Demilitarized zone
DOS Denial-of-service
DRC Democratic republic of Congo
E-CASH Electronic cash
E-CHECK Electronic check
E-COMMERCE Electronic commerce
ICT information and communication technologies
IDS Intrusion detection system
IEC International electro technical commission
IS Information systems
ISMS International security management system
ISO International standards organization
ISP Internet service provider
IT Information technology
LAN Local area network
M-payment Mobile payment
PDA Personal device assistant
PSP Processing service provider
VPN Virtual private network
Page | 58
VII.2. List of figures
Figure 1: From of e-commerce
Figure 2: E-commerce framework
Figure 3: Initial structure of IT capabilities
Figure 4: IT infrastructure components
Figure 5: Level of acceptable security for e-commerce
Figure 6: Layered security
Figure 7: DMZ deployment
Figure 8: Processing of card transaction
Figure 9: E-checking processing using Authorize..net
VII.3. List of tables
Table 1: Qualitative vs quantitative research methodologies
Table 2: Types of central tendency measures
Table 3: Repartition of respondents per working experience
Table 4: Repartition of respondents per position
Table 5: E-payment methods reported
Table 6: List of issues faced by e-payment systems
Table 7: Confidentiality elements
Table 8: Score of Integrity check of the firewall
configuration
Table 9: Frequency table of integrity check of firewall
configuration
Table 10: System integrity result
Table 11: Report of unauthorized attempts to sensitive data
Table 12: Additional physical access control score
Table 13: Frequency distribution of physical access control
Table 14: Availability capabilities
Table 15: Summary of the security capabilities
P a g e | 59
VII.4. Data Collection questionnaire
Brief Overview
The aim of this questionnaire is to assess the security of the
e-payment systems in Democratic republic of Congo in accordance to the
confidentiality, integrity and availability concepts of the security of an
information system. Because it's for an academic dissertation, only a sample of
relevant questions has been selected for quantitative analysis purpose.
Select only one response unless otherwise stated A.
Generality
Question 1
Are you interested by the result of this assessment?
1: No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 2: Personal information
Position in the company:
Sex :
Years of experience:
Company name:
Question 3
Are you familiar with electronic payment systems?
1 : No 2 : Not sure 3 : Not applicable 4 : yes 5 : Most
familiar
Question 4
Does your organization used or commercialize an e-payment
system?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 5 (select all which applied)
Which product are you offering to your clients?
1 : None 2: Not sure 3 : Visa card 4: Mastercard 5 : electronic
check
6 : electronic cash 7 : Online banking (e-banking) 8: Mobile
payment (M-payment)
9 : Other : (cite)
----------------------------------------------------------------------------------------------------------
Question 6
During the last past twelve months, have you faced some issues
related to the use of one of the e-products you are offering to your
clients?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 7 (select all which applied)
Please select which issue have you encountered
1 : Fraud 2 : Not sure 3:Theft 4 : service unavailability
5 : disclosure of confidential information 6 : misuse of
information 7 : falsification
8 : Other (cite)
------------------------------------------------------------------------------------------------------
Page | 60
Question 8
Does any written security policy exist related to electronic
transaction?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 9
Is the written security policy shared to your clients?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
B. Confidentiality
Question 10
Are all connections between the organization's networks and
external third party or public wide area IP networks made via a formally
authorized firewall (or have equivalent approved controls over the data and
protocols which are allowed through)?
1 : No 2 : Not sure 3:No firewall used 4 : Not applicable 5 : No
external connection
6 : yes
Question 11
Does your main internet connection use a router?
1 : No 2 : Not sure 3 : Not applicable 4 : No internet connection
5 : yes
Question 12
Is remote access to the management port of the router or firewall
strictly restricted?
1: No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 13
How often is the router or firewall configuration checked for
integrity?
1 : Never 2: Not sure 3 : monthly 4 : weekly 5 : Not applicable 6
: Daily
Question 14
Are the firewalls configured to default to reject everything,
only accepting those protocols that are explicitly required, to those IP
addresses which specifically require them?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 15
Is the logical access to firewalls (admin user logons, etc)
subject to tight restrictions and authentication... and is this regularly
reviewed?
1 : No 2 : not sure 3 : No opinion 4 : partially 5 : Yes
Page | 61
Question 16
How is encryption being applied on your network
infrastructure?
1 : No encryption 2 : Not sure 3 : LAN and PC resident program
4 : Hardware Cryptographic Device 5 : hardware cryptographic
device and software resident
program
C. Integrity
Question 17
Is there any digital certificate system in the Network
infrastructure?
1 : No 2 : Not sure 3 : distribution only 4 : Not applicable 5 :
Yes
Question 18
Is access to data files and programs restricted or controlled in
any way?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 19
Is there a facility to detect and report unauthorized attempts to
access ALL sensitive data?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 20
In addition to logical access controls, are there any physical
access controls for computers holding very sensitive data (e.g. PC key/lock,
stored in locked cabinet, etc.)?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 21
Are laptops computers carrying sensitive data used offsite (home,
public network,...)?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 22
Is there a mechanism in place to detect and prevent virus
infection?
1: No 2: Not sure 3: Planned 4: Not applicable 5: Yes
Question 23
Are all virus incidents managed in a secure manner, in that they
are cleaned up, investigated, reported to management, and properly
documented?
1: No 2: Not sure 3: Only reported 4: investigated
5: reported
and documented 6: investigated, reported and documented
Page | 62
D. Availability
Question 25
Do critical network and e-payment system hardware components
operate from an uninterruptable power supply system?
1 : No 2 : Not sure 3 : No opinion 4 : Some of them 5 : Yes
Question 26
Is the recovery of the e-payment system included in a formal
contingency/business resumption plan? (Business continuity plan)?
1 : No 2 : Not sure 3 : No opinion 4 : plan in development 5 :
Yes
Question 27
Are any back-up facilities, features or practices in place for
the DATA and SOFTWARE held on the system being reviewed?
1 : No 2 : Not sure 3 : No opinion 4 : Not applicable 5 : Yes
Question 28
What type of backup is performed?
1: Incremental 2 : Not sure 3 : No opinion 4 : periodic full and
incremental
5: always full backup
Question 29
How many copies of backup are taken?
1: one copy 2 : not sure 3 : not applicable 4 : two copies 5 :
more than two copies
| 


