II.7.2.3 Security Policy
Why security policy is important in the context of security of
e-payment systems?
As described above in this research, security of Information
system is defined within a framework of guidance and requirements developed by
ISO/IEC under the ISO 27001/2 framework for the development of an Information
Security System Management (ISMS).
Figure 5: Level of acceptable security for
e-commerce
Source: Gary Schneider, 2011, p443
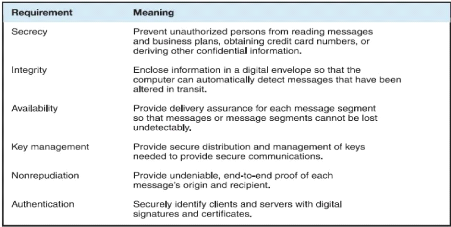
Page | 20
Page | 21
The most important for the security policy development is to
make sure that answers can be provided to the following questions:
V' Who is accessing the site? => Authentication of
the user
V' Who is allowed to connect and access to the site?
=> Access control V' Who is granted access to information? =>
Confidentiality or security V' Who is allowed to modify information?
=> Integrity
V' Who or what causes a specific event to occur on
the system and when it happens? => Audit
These fundamental questions will be the drivers for en
effective security policy implementation for an e-commerce information
system.
II.7.2.4 Computer security overview
This research considers computer security in the context of
all kinds of threats that an information system can face that is able to
destroy abuse or corrupt the information: unauthorized access, use,
modification or deletion of information.
To protect against threat, countermeasure; «physical or
logical procedure that recognizes, reduces, or eliminates a threat», must
be taken to ensure that the risk associated to the so called threat is
mitigated. (Gary Schneider, 2011, p440).
In today's computer use, the big threat is called hackers or
crackers who are able to break security of information system and gain
unauthorized access to computers or servers to steal information or damage the
system.
II.7.2.5 Overview of the client computer security
Client computers (laptop and desktop) or wireless devices are
used to connect to the internet in order to participate to the e-commerce.
These client machines or devices must be protected against threats or harmful
programs contained in web sites.
In this section an overview of web sites contents which
represent a threat to the client computers such as cookies, web bugs, active
contents, java applets, java script, active control, and graphics or plug in,
viruses and worms will be discussed.
Cookies
In the context of security, the definition that describes well
cookie is provided by Turban (Turban et al., 2006, p.165) who defines a cookie
as «a data file that is placed on a user's hard drive by a remote web
server, frequently without disclosure or the user's consent that collects
information about the user's activities at the site».
This definition states clearly that a cookie is like a spy who
observes user's online activity, therefore susceptible to illegal activity on a
client machine.
Page | 22
For e-commerce, web server's cookies store useful information
about user activity such as shopping card information which will be required by
the payment processing system.
Web bugs
Turban et al. (2006) and G. Schneider (2011) identify web bugs
as «tiny graphics» which can be embedded in web pages or emails to
store cookies on a user's computer in order to monitor his activity on the
web.
Active content, java applets, active
control
G. Schneider (2011, p446) defines active content as
«program that are embedded transparently in web pages and cause action to
occurs», to extend the functionality of html.
In the context of e-commerce, active content permits for
example to place items in a shopping cart, calculate the total amount of the
invoice and deduct the tax, add shipping cost and any other fees automatically
when a user shop online.
Active content can be java applets, JavaScript, Vbscript and
active controls which are used on the web site to implement automation or
execution of some actions.
Activex control is to be associated to object on the web page
in which programs and properties have been embedded.
Active content, java applets, active control can implement
malicious instructions which can break security of the client computers.
Viruses, worms, antivirus
Virus is program that attaches itself to another program in
the computer to cause damage in the host computer every time when this
application program will be executed.
A worm is a «type of virus that replicates itself on the
host machine» to spread out the infection. (G. Schneider, 2011).
The countermeasure against virus and worm is antivirus
software installed on all computers and servers in the network.
Page | 23
Digital certificate, digital
signature
Like for the epistolary communication with signed letters or
documents to identify the sender by its signature, electronic communication
uses digital signature in place of the personal signature.
Digital signature uses the encryption technology to ensure
that only authenticated users can access to the resource.
Digital certificate or digital ID is defined by G. Schneider
(2011, p455) as «an attachment to an email message or a program embedded
in a web page that verifies that the sender or web site is who or what it
claims to be».
Digital signature and digital certificate are used to ensure
confidentiality of the transaction on the web site; they can help to ensure
secured online transaction for e-commerce.
| 


