2.2.2: The system development life cycle
methodology (the waterfall method)
The systems development life cycle is sometimes called the
waterfall method because the model visually suggests work cascading from step
to step like a series of waterfalls with sometimes a considerable feedback
between the various steps or phases [24]. A set of steps for solving
information system problems: the basis for most systems analysis and design
methodologies.
The first step is problem definition. The intent is to
identify the problem, determine its cause, and outline a strategy for solving
it [24].
Given a clear problem definition, analysis begins. The
objective of analysis is to determine exactly what must be done to
solve the problem. Typically, the system's logical elements (its
boundaries, processes, and data) are defined during analysis.
The objective of design is to determine how the
problem will be solved. During design the analyst's focus shifts from the
logical to the physical. Processes are converted to manual procedures
or computer programs. Data elements are grouped to form physical data
structures, screens, reports, files, and databases. The hardware components
that support the programs and the data are defined.
The system is created during development. (Note:
Because the entire process is called the system development life
cycle, some experts prefer to use other labels, such as system creation, for
this stage.) Programs are coded, debugged, documented, and tested. New hardware
is selected and ordered. Procedures are written and tested. End-user
documentation is prepared. Databases and files are initialized. Users are
trained.
Once the system is developed, it is tested to ensure that it
does what it was designed to do. After the system passes its final test and any
remaining problems are corrected, the system is implemented and released to the
user. After the system is released, maintenance begins. The objective of
maintenance is to keep the system functioning at an acceptable level
The figure below depicts the various steps to be followed when
applying the waterfall method
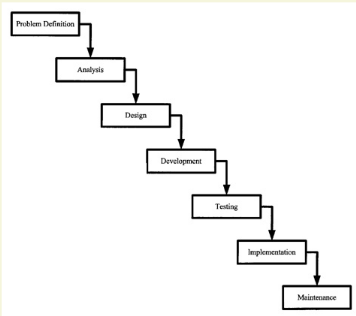
Figure 14; The system
development life cycle is sometimes called the waterfall method
[24]
2.3: Information systems
project implementation
Implementation is the process of completing the system and
turning it over to the user [24]. In the case of an information system, it
includes all the processes involved in site preparation; documentation
preparation; personnel training; system cutover and system release.
Implementation occurs after the system has been analyzed, designed,
constructed, and tested [24].
1. Site preparation: It involves preparing
the work environment, installing the hardware, and configuring any new
equipment to work with existing computers and peripherals. The work environment
includes sufficient space to hold the computer, its peripherals, desks, storage
cabinets, printer stands, and other furniture, and to store such supplies as
paper, ribbons, disks, backup media, forms, cleaning supplies, documentation,
and procedure manuals. Wiring, communication lines, and other physical
connections must be installed. A raised floor might be needed. Security
features might be required [24]. A dependable power supply is essential. Large
computer systems often require custom-designed power supplies. Although most
small computer systems run on standard household current, the equipment can
easily tax the limits of existing wiring (particularly in older buildings), so
rewiring might be necessary. Surge protectors and an uninterruptable power
source (UPS) are recommended for most systems. Air conditioning is another
factor. Computers are heat sensitive, and heat-related problems are difficult
to trace. The computer itself generates heat, and that can add to the air
conditioning load. The cost of inadequate air conditioning is often measured in
excessive downtime and high maintenance costs. Ergonomic requirements are
intended to provide the users with a comfortable working environment. Key
parameters include lighting, glare, airflow, noise, temperature, humidity,
workspace, and the design of the furniture. Many organizations have implemented
ergonomic standards.
2. Documentation preparation and design:
Documentation consists of the specifications, instructions, tutorials,
reference guides, and similar materials that accompany and explain a piece of
software or a hardware component [24]. A complete set of user documentation,
systems documentation, software documentation, and operations documentation
must be available to support the implementation process. In addition to
procedures for performing system tasks, preparing paperwork, entering data, and
distributing output, documentation for backup, recovery, auditing, and security
procedures is also needed. Documentation tells the users how to operate the
system, helps to resolve problems and errors, and supports the training
process.
3. Training: Before the system is released,
the users, system maintenance personnel, system operators, and other people
affected by the system must be trained [24]. The user manual and the written
procedures form the core of the training plan. Initially, the analysts and
other technical experts should show the users how to perform the various tasks.
Gradually, the experts should do less and the users more until the users
clearly understand the system. Following the initial intensive training period,
the users should begin to work on their own, but the experts should be
available to provide quick, accurate technical support. Over time the level of
technical support should decline, but facilities for answering user questions
(e.g., a help facility) should be maintained for the life of the system. In
addition to the primary users and system support people, back-up personnel must
also be trained. Often the primary person trains his or her backup. People
retire, resign, suffer injuries and illnesses, and earn promotions, so there
will be turnover. Training does not end when the system is released; it is an
ongoing activity. In-house training is suitable when the system is developed
internally. The training can be tailored to the system and the organization's
environment, touching on the relationship between the new system and existing
systems and stressing user interests and needs. Unfortunately, users sometimes
undervalue in-house training because they believe the in-house experts will
always be available to provide assistance on request. Third party training
includes vendor-supplied training, developer-supplied training, and training
from independent outside services. Such training is common when a company lacks
in-house information system support or has no on-going training program, or
when a third party develops the system. Some training is done in a traditional
classroom environment. In other cases, the trainer goes to the trainee, perhaps
providing one-on-one or small group training on specific equipment or in the
user's environment. Videoconferencing is an economical training medium for a
relatively brief time (hours, days, or weeks). Distance learning (via satellite
or other communication media) is effective for longer periods (weeks, months,
years). Interactive training software (on tape or CD) is both popular and cost
effective. Computer-based training (CBT) utilizes the computer as a training
tool; for example, an instruction system is a type of expert system that
implements computer-based training.
4. Cutover strategies: System cutover is the
process of turning the system over (or releasing the system) to the user. Some
experts believe that a system should be released any weekday before Thursday,
giving the users at least one day (Friday) to experiment and giving the
installers the weekend to fix any last-minute problems. Other experts believe
that a system should be released on Friday, thus giving the installers three
full days to complete the installation before the users begin working with it
[24].
5. System release: After the system is
installed and stable, it is released, or turned over, to the user. In most
cases, the system release or system turnover process includes a formal user
sign off that implies user acceptance of the system [24]. If the system was
developed in-house, system release marks the end of the developer team's
responsibility. If the system was developed by outside contractors or
consultants, system release implies successful completion of the contract.
6. Post-implementation review: A
post-implementation (or post-release) review should be scheduled some time
after the system is released [24]. During the post-implementation review the
developers should investigate any remaining problems and compare the project's
objectives, cost estimates, and schedules to the actual outcomes. The idea is
not simply to find discrepancies, but to explain them. Knowing why mistakes
were made is the key to improving the organization's analysis, design,
scheduling, and cost estimating procedures. During the post-implementation
review, such general concepts as the design philosophy and the design strategy
should be discussed. The hardware platform, the inputs, the outputs, the
interfaces, the dialogues, the processes, the files and databases, and the
documentation should all be carefully studied to ensure that the system
performs as designed.
|
|



