|
DEDICATION
To the Almighty God
To my late father
To my dearest mother
To my appreciate Brothers
To my cousins
I dedicate this book.
KAYUMBA Fred
To the Almighty God
To my late family
To my appreciate family victims of genocide
To my adoptive families
I dedicate this book.
KAYUMBA Thierry
ACKNOWLEDGEMENTS
Grateful acknowledgement is made to the following persons and
organizations for their contribution to the success of this work.
Our sincere thanks go first and foremost to Mr. ASHRAPH
Sulaiman and Miss. Marie Paule for having accepted to supervise this
dissertation despite their enormous responsibilities. Without their guidance,
support and advice, the completion of this dissertation would be a burden.
Sincere big thanks go to the following families: KAYUMBA
Etienne, KAYUMBA Charles, family KAMANGO Théophile and family
MUCUMANKIKO Silas for their education and love we have presently achieved.
Profound thanks go to my aunt late Caritas, my aunt UMUHOZA
Epiphanie, MUREKEYISONI Zuena, HAKIZIMANA Louis, MUNYANEZA Achille, RWISUMBURA
Eric and MATABARO Albert. [K. Fred]
Special thanks go to COUPALA, my little brother NYAGATARE M.
Serge, my aunt MUKAKIREZI Joséphine, my cousin-sister TUNGA Claire,
GRAINDORGE Céline, SAPHIR Paula Hélène, SANGWA Sylvie and
African Evangelical
Enterprise Rwanda who have been there when we need them and
for their great affection. [K. Thierry]
We also thank our classmates and friends for their
encouragement and support, whose assistance has not been ignored. The
researchers also wish to pass special thanks to the Government of Rwanda, the
National University of Rwanda, especially the Department of Computer Science
that availed us skills for the accomplishment of this work.
KAYUMBA Fred & KAYUMBA Thierry
TABLE OF CONTENTS
LIST OF FIGURES
viii
LIST OF TABLES
ix
ABSTRACT
x
CHAPTER I: GENERAL INTRODUCTION
1
I.1 INTRODUCTION
1
I.2 STATEMENT OF THE PROBLEM
1
I.3 PROJET OBJECTIVES AND GOALS
2
I.4 HYPOTHESIS
2
I.5 INTEREST OF THE PROJECT
3
I.5.1 Personal Interest
3
I.5.2 Community Interest
3
I.6 PROJECT SCOPE
3
I.7 METHODOLOGY
4
I.8 ORGANIZATION OF THE STUDY
4
CHAPTER II: THEORETICAL CONCEPTS AND
TERMINOLOGY
5
II.1 INTRODUCTION
5
II.2 TERMINOLOGY
5
II.2.1 Internet
5
II.2.2 WWW
6
II.2.3 Types of Nodes
6
II.2.4 Techniques Used in the Transition
6
II.2.5 Protocols
7
II.3 INTERNET PROTOCOL (IP)
8
II.3.1 IP Versions
8
II.4 IP ADDRESS
10
II.4.1 IPv6 address
10
II.4.2 IPv6 addressing notation
10
II.4.3 IPv6 prefixes notation
12
II.4.4 IPv6 address in Uniform Resource Locator
(URL)
13
II.4.5 IPv6 types
13
II.4.6 Special addresses
14
II.4.7 IPv6 addresses with embedded IPv4
addresses
15
II.5 IP HEADER
17
II.5.1 IPv4 Header
17
II.5.2 IPv6 Header
18
II.5.3 Header Simplified
20
II.5.4 Comparison of IPv4 and IPv6 Headers
21
II.5.5 New Extension Headers
22
II.6 IPv6 CONNECTIVITY
23
II.7 ICMP
24
II.7.1 ICMPv6
24
II.8 UPPER-LAYER PROTOCOL
25
II.8.1 DHCPv6
25
II.8.2 IPv6 and the Domain Name System
25
II.9 IPv6 FEATURES
26
II.10 DIFFERENCE BETWEEN IPv4 AND IPv6
28
II.11 QUALITY OF SERVICE
29
CHAPTER III: METHODOLOGY
30
III.1 INTRODUCTION
30
III.2 MIGRATION METHODOLOGY
30
III.3 STEPS IN MIGRATION METHODOLOGY
30
III.3.1 Determining Requirements
30
III.3.2 Understanding the existing system
31
III.3.3 Decision making
31
III.3.4 Testing
33
III.3.5 Deploying
34
III.3.6 Management
34
III.4 TRAINING
34
III.5 ADVANTAGES AND DISADVANTAGES OF MIGRATION
METHODOLOGY
35
III.5.1 Advantages of migration methodology
35
III.5.2 Disadvantages of migration methodology
35
III.6 TOOLS
35
III.6.1 Software Tools
35
III.6.2 Hardware
36
CHAPTER IV: QUALITY OF SERVICES, TEST AND
ANALYSIS
37
IV.1 INTRODUCION
37
IV.2 NETWORK REQUIREMENTS
37
IV.2.1 Operating Systems
37
IV.2.2 Applications and Services
38
IV.3 ANALYSIS
38
IV.3.1 Bytes
39
IV.3.2 Bandwidth
39
IV.4 TECHNIQUES MECHANISM
40
IV.4.1 Dual Stack technique
40
IV.4.2 Tunneling technique
41
IV.5 TEST and ANALYSIS
42
IV.5.1 Ping Results of Network test lab
43
IV.5.2 Netwrok test lab Telnet results
45
IV.5.3 Network test lab Analysis
46
IV.5.4 Summary of Test
50
IV.6 TRAINING
51
IV.6.1 Install IPv6 on Windows XP
51
IV.6.2 Uninstall IPv6 on Windows XP
54
IV.6.3 Difference between an IPv4 and an IPv6
system with Windows XP
55
IV.6.4 IPv6 with Linux
57
IV.7 VERIFICATION OF HYPOTHESIS
58
CHAPTER V: CONCLUSION AND RECOMMENDATIONS
59
V.1 CONCLUSION
59
V.2 RECOMMENDATIONS
59
REFERENCES
61
APPENDIX
63
ACRONYMS AND EXPRESSIONS
AH Authentication Header
DHCP Dynamic Host Configuration Protocol
DHCPv6 Dynamic Host Configuration Protocol version 6
DNS Domain Name System
DOS Disk Operating System
DSCP Differentiated Services Code Point
EH Encryption Header
FEDORA Flexible Extensible Digital Object and Repository
Architecture
HTTP Hypertext Transfer Protocol
ICMP Internet Control Message Protocol
ICMPv6 Internet Control Message Protocol version 6
IETF Internet Engineering Task Force
IHL Internet Header Length
IOS Internetwork Operating System
IP Internet Protocol
IPng Internet Protocol next generation
IPsec Internet Protocol security
IPv4 Internet Protocol version 4
IPv5 Internet Protocol version 5
IPv6 Internet Protocol version 6
IPv9 Internet Protocol version 9
ISP Internet Service Provider
Kbps Kilobits per second
MAC Media Access Control
MB Mega Byte
PDA Personal Digital Assistant
PING Packet Internet Groper
PING6 Packet Internet Groper version 6
QoS Quality of Service
SDM Security Device Manager
TCP Transmission Control Protocol
ToS Type of Service
TTL Time to Live
UDP User Datagram Protocol
URL Uniform Resource Locator
WWW World Wide Web
LIST OF FIGURES
Figure 1: IPv4 Header
17
Figure 2: IPv6 Header
19
Figure 3: Dual Stack
32
Figure 4: Tunneling
33
Figure 5: QoS Status
39
Figure 6: QoS of bandwidth
40
Figure 7: Dual Stack diagram
41
Figure 8: Network test-lab diagram
42
Figure 9: Ping IPv4 address
43
Figure 10: Ping6 IPv6 site-local
44
Figure 11: Ping6 IPv6 link-local address
44
Figure 12: Ping6 IPv6 embedded IPv4 address
44
Figure 13: Telnet IPv6/IPv4
45
Figure 14: The packets list.
46
Figure 15: Sent Packets
49
Figure 16: Received Packets
49
Figure 17: Total Packets
50
Figure 18: IPv6 install
51
Figure 19: IPv6 install with NETSH
52
Figure 20: IPv4 node Local Area Connection
Status
53
Figure 21: Network Component / Protocol
53
Figure 22: IPv6 install
54
Figure 23: IPv4/IPv6 node Local Area Connection
Status
55
Figure 24: IPv6 uninstall
56
Figure 25: IPv4 address
56
Figure 26: IPv6 address
57
Figure 27: IPv6 installation in Linux
58
LIST OF TABLES
Table 1:IPv6 prefix notation
13
Table 2: Comparison of IPv4 header and IPv6
Header
22
Table 3: IPv4 versus IPv6
28
Table 4: IPv6 and IPv4 Header packet
47
Table 5: Internet Traffic per System and
Protocol
48
ABSTRACT
The purpose of this project is to analyze the evolution of
Internet Protocol, how we can migrate from the existing one running to its
successor.
The theoretical concepts needed to carry out this study have
been thoroughly studied and described in this book. The motivations behind the
adoption of the IP next generation have been focused on for a good
understanding.
The methodology used was «the migration methodology»
in order to aid the network migrator to analyze and simplify the migration
process. The steps in the migration methodology have been followed carefully to
achieve this study.
The feasibility study of migrating to IPv6 from IPv4 part that
was the crucial phase of this study has been critically considered. The first
activity was to determine devices that can support the IPv6. The second
activity carried out was to set up a network. The third activity was to use
Network Analyzer software to detect traffics in network. Finally, we analyze
the results obtained.
Recommendations have also been suggested for further research
to enhance, revise and more features to the related topic.
CHAPTER I: GENERAL
INTRODUCTION
I.1 INTRODUCTION
Internet Protocol (IP) is a technical standard that allows
computers of all sizes, from many vendors, running totally different operating
system, to communicate each other over networks.
Nowadays many organizations have started to depend on Internet
in their usual work, Internet is growing day by day, and the spread of Internet
is providing significant benefits to its users by enhancing good opportunities.
Internet has become a fundamental part of life.
Millions of users at ten of thousands of sites around the
world depending on the global as part of their daily work environment, it might
appear that Internet is a completely stable production facility.
The Internet world has passed the early stage of using the
IPv4 and has supported the Internet's phenomenal growth over the last decade,
and IPv4 is the first version of the Internet Protocol to be widely
deployed.
As the technology continues to evolve, the Internet
Engineering Task Force (IETF) discover new ways to use the technology and have
developed a newer version of IP, known as IPv6 (also known as IP next
generation) which will upgrade the IPv4, and it is designed to replace the
current version (IPv4)
I.2 STATEMENT OF THE PROBLEM
Due to the rapid growth of Internet, limitations in its design
and the imminent IP address space limitations, in a few years the Internet will
face several problems such as conflict between IP addresses in the network.
In the early 1990s, people became aware of the rapidly
diminishing address space of IPv4, due also to this lack of IPv4 addresses with
the current addressing scheme, and there is not enough IP addresses available
to the future demand of device connectivity as the current version (IPv4) that
is expected that will be supported until at least 2025, there will be a point
when there will be lack of free addresses available for connecting to new
hosts. At that point, no more users can sign up for account at ISPs, and no
more machines can be set up to access the web.
As new technologies emerge, the market dominating vendors such
as Microsoft, Cisco are start going to set the IPv6. Computers and networks
hardware continue to evolve; they come with Network Interface Card incorporated
into that requires an IP address. For example IP telephony, IP scanners, IP
printers, etc.
Due to all those problems, this study motivates us to study
the evolution of IP and examine the efforts of IETF to propose a revision of
IP.
I.3 PROJET OBJECTIVES AND GOALS
The main project objectives and goals of our work are:
· To study the change from IPv4 to IPv6.
· The feasibility study of migrating from IPv4 to IPv6.
· To set up a LAN network running IPv4/IPv6.
· To analyze the Quality of Services (QoS) and the
performance of the next generation of Internet.
The aim of this study is to consider the ongoing evolutionary
process and lead us to view the Quality of Service (QoS) and the performance of
the existing system relative to the future system.
I.4 HYPOTHESIS
This project aims at verifying the following hypothesis:
«It is possible to migrate to IPV6 from IPV4 which will
provide better quality of service and performance of network to end
users.»
I.5 INTEREST OF THE PROJECT
I.5.1 Personal Interest
· To put into practice concept learned as computer
science undergraduates in order to improve our knowledge in network
management.
· Understand how a new version (IPv6) will upgrade a
current version (IPv4).
· Understand better how IPv6 network works and be
familiar with the configuration of IPv4/IPv6.
I.5.2 Community Interest
· To ensure that the Internet
can support an exponential growing of Internet and the increasingly large
number of IP enabled devices.
· To solve the shortage problem of IPv4 address in the
future.
· To be up to date and be ready with new applications.
· Implemented efficiently the new version of Internet
without changes of the existing Internet which has more features and
performance than the current version.
· To bring huge benefits of national economy and increase
the country's competitiveness in science and technologies...
· To start considering switching to IPv6 before spending
money on IPv4.
· To introduce IPv6 into their existing networks.
I.6 PROJECT SCOPE
The project is focused on comparing the two main versions,
analyzing the new version, the IPv6 transition and interoperability mechanisms
that are designed to allow users to adopt and to provide direct
interoperability between IPv4 and IPv6 hosts.
Due to the lack of a company or organization that had already
IPv6 in their network or an Internet Service Provider (ISP) that provide IPv6
services; we were not able to test some IPv6 applications such as File Transfer
Protocol, HTTP (it requires to have a network running one of IPv6
mechanisms)1(*), etc... and
analyze these applications and other marvels of the Next Generation
Internet.
I.7 METHODOLOGY
With the aim of verifying the above stated hypothesis and achieve
the given objectives the following methodology has been used:
· The migration methodology has been used in order to aid
the migration of network in choosing migration mechanisms.
· Comparative methodology has
been also used of comparing the two versions with a view to discovering
something about one or more characters being compared. This methodology was
used to collect data to gather, and others information.
I.8 ORGANIZATION OF THE
STUDY
The roadmap for the rest of this study contains five chapters
arranged as follows:
· Chapter one: The first chapter is about the general
introduction.
· Chapter two: It deals with theoretical concept and
terminology of IP from different sources such as books, electronic, Internet,
and other relevant sources.
· Chapter three: It deals with the methodology used for this
study.
· Chapter four: It deals with QoS, test and analysis.
· Chapter five: The last chapter provides the conclusions
and recommendations.
CHAPTER II: THEORETICAL CONCEPTS
AND TERMINOLOGY
II.1
INTRODUCTION
This chapter provides terminology used and presents a brief
description of theoretical concepts related to IP. This chapter provides also
different versions of IP and an explanation of features, benefits of IPv6 and
comparison of versions of IP. The purpose of this chapter is to provide readers
of this book guidance on the evolution of IP.
II.2 TERMINOLOGY
II.2.1 Internet
The Internet, or simply the Net, is the publicly accessible
worldwide system of interconnected computer networks that transmit data by
packet switching using a standardized Internet Protocol (IP).2(*)
In other word the Internet is a massive network of networks, a
networking infrastructure. It connects millions of computers together globally,
forming a network in which any computer can communicate with any other computer
as long as they are both connected to the Internet. Information that travels
over the Internet does so via a variety of languages known as
protocols.3(*)
As of January 2006, over 1 billion people use the Internet
according to Internet World Stats4(*)
II.2.2
WWW
The World Wide Web ("WWW" or simply the
"'Web") is a global information space which people can read-from and
write-to via a large number of different Internet-connected devices.5(*)
The term WWW is often mistakenly used as a synonym for the
Internet itself, but the Web is actually something that is available over the
Internet, just like e-mail and many other Internet services.
II.2.3
Types of Nodes
The following terms are used in this study:
· Node: A device that implements IP. A node can be a
host, router, a Personal Digital Assistant (PDA) or a cell phone.
· Host: Any node that is not a router, it can be a
personal computer, a PDA or a cell phone.
· Router: A router is a node with two or more network
(physical or virtual) interfaces, capable of forwarding packets between the
interfaces.
· IPv4-only node: A host or router that implements only
IPv4. An IPv4-only node does not understand IPv6. The installed base of IPv4
hosts and routers existing before the transition begins are IPv4-only nodes.
Nodes that do not support IPv6.
· IPv6/IPv4 node: A host or router that implements both
IPv4 and IPv6.
· IPv6-only node: A host or router that implements IPv6,
and does not implement IPv4. A node that will replace IPv4-only
node.
II.2.4
Techniques Used in the Transition
· The term «dual-stack» refers to TCP/IP
capable devices providing support for both IPv4 and IPv6. It is important to
understand that having a device being able to communicate over both IPv4 or
IPv6 does not necessarily mean that all applications operating within this
device are capable of utilizing both IPv4 and IPv6. The term «Dual-stack
routing» refers to a network that is dual IP, that is to say all routers
must be able to route both IPv4 and IPv6.
· The term «tunneling» refers to a means to
encapsulate one version of IP in another so the packets can be sent over a
backbone that does not support the encapsulated IP version. For example, when
two isolated IPv6 networks need to communicate over an IPv4 network, dual-stack
routers at the network edges can be used to set up a tunnel which encapsulates
the IPv6 packets within IPv4, allowing the IPv6 systems to communicate without
having to upgrade the IPv4 network infrastructure that exists between the
networks.
These are not expected to be the only tools available for
transition mechanisms. Additional transition mechanism (such as Automatic
tunneling, Pv4 multicast tunneling, IPv4-compatible IPv6 addresses) are
available but this study is focused on these techniques mechanism of transition
stated above.
II.2.5
Protocols
A protocol is an agreed upon format for transmitting data
between two devices. So that packages of data can go of a computer source to a
computer of destination on a network, it is important that all the units of the
network communicate in the same language or protocol. A protocol consists of a
whole of rules which increase the effectiveness of the communications within a
network.
They are two types of protocol:
· CONNECTION ORIENTED PROTOCOL:
They are the protocols operating a control of transmission of
the data during a communication established between two machines in such a
diagram, the receiving machine sends acknowledgements of delivery at the time
of the communication, thus the transmitting machine is guarantor of the
validity of the data which she sends. The data are thus sent in the form of
flood. TCP is a protocol directed connection
· CONNECTIONLESS ORIENTED PROTOCOL
It acts of a mode of communication in which the transmitting
machine sends data without preventing the receiving machine, and the receiving
machine receives the data without sending notice of receipt to the first. The
data are thus sent in the form of blocks (datagram). UDP is a protocol not
directed connection
II.3
INTERNET PROTOCOL (IP)
Internet Protocol is the network layer for the TCP/IP protocol
suite by which data is sent from one computer to another. IP like all
network-layer protocols moves of information from the original source to the
ultimate destination. This service is sometimes referred to «end-to-end
packet delivery». This reliability of the service provided by IP is called
«best-effort» which means that IP will try very hard to deliver a
packet to destination, but IP makes guarantee that packet will arrive without
error.6(*)
II.3.1
IP Versions
There are currently two main versions of Internet Protocol
IPv4 and IPv6.
II.3.1.1 IP version 4
IPv4 is the first version of the Internet Protocol to be
widely deployed. IPv4 is the dominant network layer protocol on the Internet.
It is the most IP widely used today. 7(*)
The name was assigned as IPv4 because on any IP header, the
first 4 bits are reserved for protocol version. Thus the first version of IP
had been assigned as IPv4.
II.3.1.2 IP version 5
IPv5 was assigned to an experimental protocol called ST2
(Internet STream protocol, version 2).
IPv5 was not a successor to IPv4, but an experimental
flow-oriented streaming protocol intended to support video and audio. It was
discussed as a successor to IPv4, but it has never been introduced for public
usage.8(*)
II.3.1.3 IP version 6
IPv6 is short for "Internet Protocol Version 6". IPv6 is the
"next generation" IP protocol designed by the IETF to replace the version IPv4
(or IP only), the Internet protocol that is predominantly deployed and
extensively used throughout the world.9(*)
Invented by Steve Deering 10(*)and Craig Mudge at Xerox`s Palo Alto Research Center,
IPv6 was adopted by the Internet Engineering Task Force in 1994, when it was
called "IP next generation" (IPng).
The name IPv6 and not IPv5 as successor for IPv4 is because
the number 5: is reserved for the ST2. The next free number was 6. Hence IPv6
was born.11(*)
II.3.1.4 IP version 9
IPv9 is a relatively unheard-of version of
the Internet Protocol attributed to China. The IP version 9 numbers has not
been allocated for this protocol by the Internet Assigned Numbers Authority.
On June 25, 2004, an announcement was made at the New
Generation Internet Ten-Digit Network Industrialization & Development
Seminar at Zhejiang University, that the protocol had been «formally
adapted and popularized into the civil and commercial sectors of China».
The validity of any meaningful implementation of IPv9 is in
question. It has been described as a protocol similar to IPv6, but with a 256
bit addresses space instead of IPv6's 128 bit address space. Chinese experts
have suggested that the required edge router translation protocols would not be
worth the questionable benefit of expanding the address space further.12(*)
II.4 IP ADDRESS
An Internet Protocol address (IP address) is a unique number
that devices use in order to identify and communicate with each other on a
computer network utilizing the Internet Protocol standard (IP). IP address is
used in different ways to identify a particular network and a host on that
network.13(*)
II.4.1 IPv6 address
The most obvious distinguishing feature of IPv6 is its use of
much larger addresses. The size of an address in IPv6 is 128 bits, which is
four times larger than an address in IPv4. A 32-bit address space allows for
232 or 4,294,967,296 possible addresses. A 128-bit address space
allows for 2128 or (3.4 × 1038) possible
addresses.14(*)
II.4.1.1 IPv6 node has multiple addresses
Any IPv6 node should recognize the following addresses as
identifying itself:
· Link-local address for each interface.
· Site-local address for each interface.
· Assigned (manually or automatically) unicast/anycast
addresses
· Loop back address
· All-nodes multicast address
· Solicited-node multicast address for each of its
assigned unicast and anycast address
· Multicast address of all other groups to which the host
belongs
II.4.2
IPv6 addressing notation
Since IPv6 addresses are 128 bits long (compared to IPv4's 32
bits), a different representation is required.
The preferred way of writing an IPv6 address is:
The IPv6 128-bit address is divided along 16-bit boundaries.
Each 16-bit block is then converted to a 4-digit hexadecimal number [0-9, A-F],
separated by colons. The resulting representation is called colon-hexadecimal.
This is in contrast to the 32-bit IPv4 address represented in dotted-decimal
format, divided along 8-bit boundaries, and then converted to its decimal [0-9]
equivalent, separated by periods. 15(*)
The following example shows a 128-bit IPv6 address in binary
form [0-1]:
0010000111011010000000001101001100000000000000000010111100111011
0000001010101010000000001111111111111110001010001001110001011010
The following example shows this same address divided along
16-bit boundaries:
0010000111011010 0000000011010011 0000000000000000
0010111100111011
0000001010101010 0000000011111111 1111111000101000
1001110001011010
The following example shows each 16-bit block in the address
converted to hexadecimal [0-9, A-F] and delimited with colons.
21DA:00D3:0000:2F3B:02AA:00FF:FE28:9C5A
The IPv6 address is case insensitive; this example can be also
written like this:
21da:00D3:0000:2f3b:02AA:00ff:FE28:9C5A
IPv6 representation can be further simplified by removing the
leading zeros within each 16-bit block. However, each block must have at least
a single digit. The following example shows the address without the leading
zeros:
21DA:D3:0:2F3B:2AA:FF:FE28:9C5A
IPv6 representation can also contain long sequences of zeros.
In IPv6 addresses, a contiguous sequence of 16-bit blocks set to 0 in the
colon-hexadecimal format can be compressed to :: (known as double-colon), Zero
compression can be used only once in an address. The following example shows
the address of compressing zeros:
The link-local address
FE80:0:0:0:2AA:FF:FE9A:4CA2
Can be compressed to
FE80::2AA:FF:FE9A:4CA2.
The biggest reduction is seen by the IPv6 local host
address:
0000:0000:0000:0000:0000:0000:0000:0001 -> ::1
Zero compression enables to determine the number of 0 bits
represented by each instance of a double-colon (::). To determine how many 0
bits are represented by the ::, count the number of blocks in the compressed
address, subtract this number from 8, and then multiply the result by 16. The
following example shows how to determine zero compression:
FF02::2
There are two blocks (the FF02 block and the 2 block). The
number of bits expressed by the :: is 96 (96 = (8 - 2) × 16).
II.4.3
IPv6 prefixes notation
The prefix is the part of the address that indicates the bits
that have fixed values or are the bits of the network identifier.
IPv6 prefix <1-128 bits> is very similar to the way IPv4
<1-32 bits> addresses are written in Classless Interdomain Routing (CIDR)
notation and it is also commonly used for subnetted IPv4 addresses <IPv4
address / subnet mask>.
An IPv6 prefix is written in notation appends the prefix
length, written as a number of bits with a slash, which leads to the following
format:
<IPv6address/prefix length>
The prefix length specifies how many left-most bits of the
address specify the prefix. This is another way of noting a subnet mask.
In IPv4 a subnet mask specifies the bits of the IPv4 address
that belong to the network ID. The prefix is used to identify the subnet that
an interface belongs to and is used by routers for forwarding.
The following explains how the prefix is interpreted as shown
in the table below:
IPv6 prefix notation 2E78:DA53:12::/4016(*)
|
Hexadecimal notation
|
Binary notation
|
Bits of prefix
|
|
2E78
|
0010 1110 0111 1000
|
16 bits
|
|
DA53
|
1101 1010 0101 0011
|
16 bits
|
|
12
|
0001 0010
|
8 bits
|
|
Total =16+16+8= 40
|
Table 1:IPv6 prefix
notation
Source: IPv6 essentials, O'REILLY, ISBN: 0-596-00125-8,
page 28
II.4.4
IPv6 address in Uniform Resource Locator (URL)
In a URL, IPv6 address is enclosed in squared brackets []
The following examples show the IPv6 address in URL:
http://[2001:1:4F3A::206:AE14]:8080/index.html
http://::192.168.2.35 can be represented as
http://[::192.168.2.35]/ipng/
Accessing IPv6 only web-sites
assumes that you have connectivity to the 6bone (the word 6bone stands for
"IPv6 backbone").
II.4.5 IPv6 types
IPv6 address is 128 bits identify for interface and can be
categorized into the following types:
· Unicast: An IPv6 unicast is an identifier for a single
interface. A packet sent to a unicast address is delivered to the interfaces
identified by that address (An address for a single interface).
The IPv6 unicast examples are: Loopback, unsigned, scope
address (link local, site local)
· Anycast: An IPv6 anycast address is an
address that is assigned to more than one interface (typically belonging to
different nodes), with the property that a packet sent to an anycast address is
routed to the "nearest" interface having that address, according to the routing
protocols measure of distance.
· Multicast: An IPv6 multicast address is an identifier
for a group of interfaces (typically on different nodes). A packet sent to a
multicast address is delivered to all interfaces identified by that address.
No broadcast in IPv6. Multicast is used instead, mostly on
local links.17(*)
II.4.6
Special addresses
There are a number of addresses with special meaning in
IPv6:
· ::1/128 The loopback address is a local host address.
If an application in a host sends packets to this address, the IPv6 stack will
loop these packets back to the same host (corresponding to 127.0.0.1 in IPv4).
This is a special address for the loopback interface, similar to IPv4 with its
"127.0.0.1".
· ::/128 The address with all zeroes is an unspecified
address, and is only to be used in software. This is a special address like
"any" or "0.0.0.0" in IPv4.
· fe80::/10 The link-local prefix specifies that the
address only is valid in the local physical link. The link local can only be
used between nodes of the same link, it can not be routed. The link local is
automatically configured on each interface.
· fec0::/10 The site-local prefix specifies that the
address is only valid inside the local organization. The site local can only be
used between nodes of the same site, it cannot be routed outside the site (it
means Internet).
It is very similar to IPv4 private addresses.
· ::/96 (0:0:0:0:0:0:a.b.c.d/96 or in compressed format
::a.b.c.d/96)- the zero prefix was used for IPv4-compatible addresses (Used for
automatic tunneling in transition mechanism).
· ::ffff:0:0/96 (0:0:0:0:0:ffff:a.b.c.d/96 or in
compressed format ::ffff:a.b.c.d/96) - this prefix is used for IPv4 mapped
addresses (in transition mechanism).
· ff00::/8 - The multicast prefix is used for multicast
addresses.
There are no address ranges reserved for broadcast in IPv6.
Applications are supposed to use multicast to the all-hosts group
instead.18(*)
II.4.7
IPv6 addresses with embedded IPv4 addresses
In environments where IPv4 and IPv6 nodes are mixed, another
convenient form of IPv6 address notation is to put the values of an IPv4
address into the four low-order byte pieces of the address.
Because the transition to IPv6 will be gradual, two special
types of addresses have been defined for backward compatibility with
IPv4.19(*)
II.4.7.1 IPv4-mapped IPv6 address
IPv4 mapped IPv6 addresses constitute a special class of IPv6
addresses. It allows a host that support both IPv4 and IPv6 to communicate with
a host that supports only IPv4. The IPv6 address is based completely on the
IPv4 address. This is an IPv6 that is used to represent an IPv4 address.
II.4.7.1.1 Notation
As a special exception to IPv6 addresses notation, IPv4 mapped
addresses are commonly represented with their last 32 bits noted as an IPv4
address.
An IPv6 address has its first 80 bits set to zero, followed by
16 bits set to one, while its last 32 bits represents an IPv4 address.20(*)

An example of IPv4-mapped IPv6 address
· 0:0:0:0:0:0.192.168.30.1 = ::192.168.30.1 is the same
address as C0A8:1E01
II.4.7.2 IPv4-compatible IPv6 address
An IPv4 compatible address allows a host supporting IPv6 to
talk IPv6 even if the local router(s) don't talk IPv6. IPv4 compatible address
is used to tunnel IPv6 packets dynamically over an IPv4 routing infrastructure.
It tells endpoint software to create a tunnel by encapsulating the IPv6 packet
in an IPv4 packet.
II.4.7.2.1 Notation
80 bits of 0s followed by 16 bits of 0s, followed by a 32 bit
IPv4 Address:

II.5 IP HEADER
II.5.1 IPv4 Header
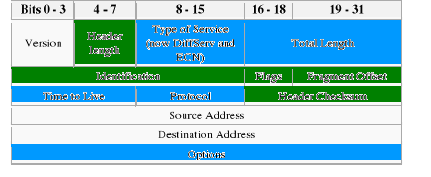
Legend:
REMOVED
REMOVED and RENAMED
Figure 1: IPv4 Header
Source:
http://en.wikipedia.org/wiki/IPv4
(August 13, 2066)
The IPv4 header fields are discussed below:21(*)
· Version: The first field in the IP header is the
version field. This is used to identify which version of IP was used to create
the header. It always set to the value 0100 (4 -bit). For IPv4, this has a
value of 4 (hence the name IPv4).
· Internet Header Length (IHL): The second field is a
4-bit Internet Header Length (IHL) telling the number of 32-bit words in the
header. It provides the length of the header itself.
· Type of Service (ToS): Now known as Differentiated
Services Code Point (DSCP) (usually set to 0, but may indicate particular
Quality of Service needs from the network, the DSCP defines the way routers
should queue packets while they are waiting to be forwarded). This filed has 8
bits were allocated to a Type of Service (ToS) field.
· Total Length: This field defines the
entire datagram size, including header and data, in bytes.
· Identification: This field is an identification field
and is primarily used for uniquely identifying fragments of an original IP
datagram.
· Flags: This filed is used to control
whether routers are allowed to fragment a packet, and to indicate the parts of
a packet to the receiver.
· Fragment Offset: a byte count from the
start of the original sent packet, set by any router which performs IP router
fragmentation
· Time to Live (TTL): An 8-bit time to live (TTL) field
helps prevent number of hops /links which the packet may be routed over.
· Protocol: This filed indicates the
type of transport packet being carried.
· Header Checksum: This field is a hop
counter. The 16-bit checksum field is used for error-checking of the header.
Each time the data unit traverses through a router, the router decrements this
field by 1. When the time-to-live field reaches a value of zero, the data unit
is discarded.
· Source Address: The field of IP address of the original
sender of the packet.
· Destination Address: The filed of the IP address of the
final destination of the packet.
· Options: Additional header fields
(called options) may follow the destination address field, but these are not
often used, but when used the IP header length will be greater than five 32-bit
words to indicate the size of the options field
II.5.2
IPv6 Header
The general header structure of IPv6 has a fixed-length of 40
bytes:
· 16 bytes for source address
· 16 bytes for destination address
· 8 bytes for general header information (Version 4-bits,
Traffic Class 1-byte, Flow label 20-bits, Payload Length 2-byte, Next Header
1-byte, Hop limit 1-byte)
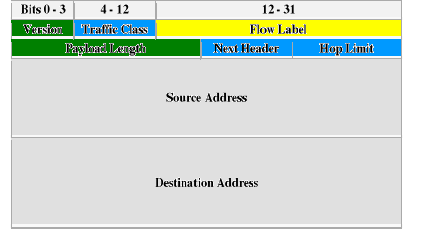
RENAMED
MODIFIEDD
ADDED
Legend:
Figure 2: IPv6 Header
Source:
http://en.wikipedia.org/wiki/Image:IPv6_header_rv1.png
(September 02, 2006)
The IPv6 header fields are discussed below:22(*)
· Version: Internet Protocol Version number (IPv6 is 6).
This has a value of 0110 (6-bits), it identifies its version.
· Traffic Class (also known as priority field): Enables a
source to identify the desired delivery priority of the packets. Priority
values are divided into ranges: traffic where the source provides congestion
control and non-congestion control traffic.
· Flow label: Used by a source to label those products
for which it requests special handling by the IPv6 router. The flow is uniquely
identified by the combination of a source address and a non-zero flow label.
· Payload length: Length of payload (in octets).
· Next header: Identifies the type of
header immediately following the IPv6 header.
· Hop limit: 8-bit integer that is decremented by one by
each node that forwards the packet. The packet is discarded if the Hop Limit is
decremented to zero.
· Source address: 128-bit address of the
originator of the packet.
· Destination address: 128-bit address of the intended
recipient of the packet.
II.5.3
Header Simplified
The IP header in IPv6 has been streamlined and defined to be
of a fixed length (40 bytes). In designing the IPv6 Header, fields from the
IPv4 Header have been removed, renamed (but still providing the same type of
functionality) or moved to the new optional IPv6 Extension Headers.
II.5.3.1 Changes in the general header structure:
Five fields have been removed from the IPv4 header:
1. Header Length (fixed length header doesn't need it)
2. Identification
3. Flags
4. Fragment Offset
5. Header Checksum (checked at the transport layer)
Three fields have been renamed and modified from the IPv4
header:
1. Traffic Class (type of service in IPv4)
2. Next Header (protocol type in IPv4)
3. Hop Limit (Time to live in IPv4)
One field has been added:
1. Flow Label.23(*)
As shown above in the IPv4 Header (Figure 1) and the IPv6
Header format (Figure 2), here are changes in the general headers:
· The «IHL» or header length field is no longer
needed since the IPv6 Header is now a fixed length.
· The IPv4 «Type of Service» is equivalent to
the IPv6 «Traffic class» field.
· The «Total Length» field has been replaced
with the «Payload Length» field.
· Since IPv6 only allows for fragmentation to be
performed by the IPv6 source and destination nodes, and not individual routers,
the IPv4 segment control fields (Identification, Flags, and Fragment Offset
fields) have been moved to similar fields within the Fragment Extension Header.
· The functionality provided by the «Time to
Live» field has been replaced with the «Hop Limit» field.
· The «Protocol» field has been replaced with
the «Next Header Type» field.
· The «Header Checksum» field was removed,
which has the main advantage of not having each relay spend time processing the
checksum. This, however, also introduces the risk of undetected errors, which
is seen as minimal due to checksums being used in most of the encapsulating
procedures.
· The «Options» field is no longer part of the
header as it was in IPv4. Options are specified in the optional IPv6 Extension
Headers. The removal of the options field from the header provides for more
efficient routing; only the information that is needed by a router needs to be
processed.
II.5.4 Comparison of IPv4 and IPv6
Headers
|
Fields of the IPv4 Header
|
Fields of the IPv6 Header
|
Comparison of IPv4 and IPv6 Headers
|
|
Version (4-bit)
|
Version (4-bit)
|
Same function but the IPv6 header contains a new value.
|
|
Header length (4-bit)
|
--
|
Removed in IPv6. The basic IPv6 header always has 40 octets.
|
|
Type of service (8-bit)
|
Traffic class (8-bit)
|
Same function for both headers.
|
|
--
|
Flow label (20-bit)
|
New field added to tag a flow for IPv6 packets.
|
|
Total length (16-bit)
|
Payload length (16-bit)
|
Same function for both headers.
|
|
Identification (16-bit)
|
--
|
Removed in IPv6 because fragmentation is handled differently in
IPv6.
|
|
Flags (3-bit)
|
--
|
Removed in IPv6 because fragmentation is handled differently in
IPv6.
|
|
Fragment offset (13-bit)
|
--
|
Removed in IPv6 because fragmentation is handled differently in
IPv6.
|
|
Time to live (8-bit)
|
Hop limit (8-bit)
|
Same function for both headers.
|
|
Protocol number (8-bit)
|
Next header (8-bit)
|
Same function for both headers.
|
|
Header checksum (16-bit)
|
--
|
Removed in IPv6. Link-layer technologies and upper-layer
protocols handle checksum and error control.
|
|
Source address (32-bit)
|
Source address (128-bit)
|
Source address is expanded in IPv6.
|
|
Destination address (32-bit)
|
Destination address (128-bit)
|
Destination address is expanded in IPv6.
|
|
Options (variable)
|
--
|
Removed in IPv6. The way to handle this option is different in
IPv4.
|
|
--
|
Extension headers
|
New way in IPv6 to handle Options fields, fragmentation,
security, mobility, Loose Source Routing, Record Route.24(*)
|
Table 2: Comparison of IPv4
header and IPv6 Header
Source:
http://www.ciscopress.com/articles/article.asp?p=31948&seqNum=1&rl=1,
(August 23, 2006)
II.5.5
New Extension Headers
The IPv6 specification currently defines 6 Extension
Headers:
· Routing Header - Similar to the source routing options
in IPv4. Used to mandate a specific routing.
· Authentication Header (AH) - A security header which
provides authentication and integrity.
· Encapsulating Security Payload (ESP) Header - A
security header which provides authentication and encryption.
· Fragmentation Header - The Fragmentation Header is
similar to the fragmentation options in IPv4.
· Destination Options Header - This header contains a set
of options to be processed only by the final destination node. Mobile IPv6 is
an example of a destination Options Header.
· Hop-by-Hop Options Header - A set of options needed by
routers to perform certain management or debugging functions.
II.6 IPv6 CONNECTIVITY
The ping (Packet Internet Groper) command:
The command is used with the IP address of the destination device. The
command can be utilized as shown in Figure using the IP address of the
destination device. In these examples, the ping command issues four echo
requests and receives four echo replies, confirming IP connectivity between the
two devices.25(*)
The following command of ping6 is shown below:
· To ping the global address of another node:
ping6 Address
where Address is the global address of the other node.
If the ping6 command fails, verify the global address of the
other node.
· To ping another node by name:
ping6 Name
where Name is a name that can be resolved to an IPv6
address through entries in the local hosts file, or through AAAA resource
records that are present in your Domain Name System (DNS) infrastructure.
If the ping6 command fails, verify that the name can be
resolved to an IPv6 address.
· To ping the IPv4-compatible address of another node:
ping6 ::IPv4Address
where IPv4Address is the IPv4 address of the other node.
If the ping6 command fails, verify the IPv4 address of the
other node.
· ping the loopback address by typing ping6 ::1.
If the ping6 command fails, verify that the ::1 address is
assigned to the interface named Loopback Pseudo-Interface.26(*)
II.7 ICMP
The Internet Control Message Protocol (ICMP) is an integral
part of the TCP/IP protocol suite. It is known as a best effort delivery
mechanism. In fact, all IP implementations must include ICMP support. The
reasons for this are simple. First, since IP does not guarantee delivery, it
has no inherent method to inform hosts when errors occur. Also, IP has no
built-in method to provide informational or control messages to hosts. ICMP
performs these functions for IP.27(*)
ICMP is an error reporting protocol for IP. When datagram
delivery errors occur, ICMP is used to report these errors back to the source
of the datagram.
ICMP reports on the status of the delivered packet only to the
source device. It does not propagate information about network changes to
routers. The ICMP protocol can be used to test the availability of a particular
destination.
II.7.1 ICMPv6
The ICMP for IPv6 (Internet Control Message Protocol Version
6) is an integral part of the IPv6 and must be completely supported by all IPv6
implementations. ICMPv6 works with IPv6. It reports errors if packets cannot be
processed properly and sends informational messages about the status of the
network.
ICMPv6 is much more powerful than ICMPv4 and contains new
functionality, It combines functions previously subdivided among different
protocols, such as ICMP (Internet Control Message Protocol version 4), IGMP
(Internet Group Membership Protocol)4, and ARP (Address Resolution Protocol),
and it introduces some simplifications by eliminating obsolete types of
messages no longer in use.
It is used by IPv6 nodes to report errors encountered in
processing packets, and to perform other Internet-layer functions, such as
diagnostics (ICMPv6 "ping"). ICMPv6 is an integral part of IPv6 and must be
fully implemented.28(*)
II.8
UPPER-LAYER PROTOCOL
A protocol layer that is immediately above IPv6. The impact of
IPv6 on upper-layer protocols is minimal because the datagram service has not
changed substantially. This section discusses UDP and TCP over IPv6 and
describes changes for upper-layer protocols, such as DNS, DHCP when used over
IPv6.
II.8.1
DHCPv6
The Dynamic Host Configuration Protocol (DHCP) is a set of
rules used by a communications device (such as a computer, or router) to allow
the device to request and obtain an IP address from a server which has a list
of addresses available for assignment, without requiring a manager to configure
information about the computer in a server database.29(*)
The DHCPv6 enables DHCP servers to pass configuration
parameters such as IPv6 network addresses to IPv6 nodes.
II.8.2
IPv6 and the Domain Name System
This section defines the changes that need to be made to the
Domain Name System (DNS) to support hosts running IPv6. The DNS is the most
important applications that have to run on IPv6 before anyone can use. The
changes include a resource record type to store an IPv6 address, and a domain
to support lookups based on an IPv6 address.30(*)
Current support for the storage of Internet addresses in the
Domain Name System (DNS) can not easily be extended to support IPv6 addresses
since applications assume that address queries return 32-bit IPv4 addresses
only.
To support the storage of IPv6 addresses in the DNS, Two new
DNS record types have been defined for IPv6 hosts to map a domain name to an
IPv6 address.
· New Resource Record Type (AAAA)
«A record type» is used for storing an IP address
(specifically, an IPv4 32-bit address) associated with a domain name. So a new
one was created to allow a domain name to be associated with IPv6 128-bit
address, this new one is called «AAAA record type (also called quad-A
records)». This new AAAA has been added to support IPv6 address.
The four «A»s («AAAA») are used to
indicate that the IPv6 address is four times the size of the IPv4 address. It
is the equivalent of IPv4 A record.
A host that has more than one IPv6 address has an AAAA record
for each address.
· A6 type record 31(*)
This new record types support renumerable and aggregatable
IPv6 addressing.
A6 is defined to map a domain name to an IPv6 address, with a
provision for indirection for leading "prefix" bits.
II.9
IPv6 FEATURES
IPv6 was designed to build on the existing features of IPv4
and provide new services and capabilities. Listed below is an overview of
several features and benefits IPv6 is intended to provide.
· Extend the IP address space enough to offer a unique IP
address to any device.
Larger address space: IPv6 increases the IP address size from 32
bits to 128 bits. Increasing the size of the address field increases number of
unique IP addresses from approximately 4.3×109 to
3.4 × 1038.
· Coexistence with IPv4 network
IPv6 will be an important and major upgrade to all our
networks and to the Internet. With all the transition mechanisms defined
though, it will gradually grow into our networks. There will not be a flag day
like there was with IPv4 in 1983, where the Internet was switched directly to
TCP.
IPv6 can and will coexist with IPv4 for a long time and the
transition mechanisms are so flexible, that there is no specific upgrade order
required. This means, as a home user you can use IPv6 even if your ISP does not
offer it yet. And within a corporate network you can for instance roll out IPv6
at the edge of the network, while your backbone is till IPv4 only.
· Auto-configuration
Clients using IPv4 addresses use the Dynamic Host
Configuration Protocol (DHCP) server to establish an address each time they log
into a network. This address assignment process is called stateful
auto-configuration. IPv6 supports a revised DHCPv6 protocol that supports
stateful auto-configuration, and supports stateless auto-configuration of
nodes. Stateless auto-configuration does not require a DHCP server to obtain
addresses. Stateless auto-configuration uses router advertisements to create a
unique address. This creates a «plug-and-play» environment,
simplifying address management and administration. IPv6 also allows automatic
address configuration and reconfiguration. This capability allows
administrators to re-number network addresses without accessing all clients.
· More header compression
Some fields from the IPv4 Header have been removed, renamed or
modified and a new field has been added.32(*)
II.10
DIFFERENCE BETWEEN IPv4 AND IPv6
IPv6 is based on IPv4; it is an evolution of IPv4. So many
things that we find with IPv6 are familiar to us. The main differences are
illustrated in the table below:
|
IPv4
|
IPv6
|
|
The size of an address in IPv4 is 32 bits
|
The size of an address in IPv6 is 128 bits
|
|
Address Shortages:
IPv4 supports 4.3×109 (4.3 billion) addresses,
which is inadequate to give one (or more if they possess more than one device)
to every living person.
|
Larger address space:
IPv6 supports 3.4×1038 addresses, or
5×1028(50 octillion) for each of the roughly 6.5 billion people
alive today.33(*)
|
|
IPv4 header has 20 bytes
IPv4 header has many fields (13 fields)
|
IPv6 header is the double, it has 40 bytes
IPv6 header has fewer fields, it has 8 fields.
|
|
IPv4 is subdivided into classes <A-E>.
|
IPv6 is classless.
IPv6 uses a prefix and an Identifier ID known as IPv4
network
|
|
IPv4 address uses a subnet mask.
|
IPv6 uses a prefix length.
|
|
IPv4 has lack of security.
IPv4 was never designed to be secure
- Originally designed for an isolated military network
- Then adapted for a public educational & research
network
|
IPv6 has a built-in strong security
- Encryption
- Authentication
|
|
ISP have IPv4 connectivity or have both IPv4 and IPv6
|
Many ISP don't have IPv6 connectivity
|
|
Non equal geographical distribution (>50% USA)
|
No geographic limitation
|
Table 3: IPv4 versus
IPv6
Source:
http://www.go6.net, Internetworking with
TCP/IP principle, protocols and Architectures, Fourth Edition, Douglas E.
Comer, ISBN 81-7808-444-9, page 612.
II.11 QUALITY OF SERVICE
QoS refers to a broad collection of networking technologies
and techniques. The goal of QoS is to provide guarantees on the ability of a
network to deliver predictable results. Elements of network performance within
the scope of QoS often include availability (uptime), bandwidth (throughput),
latency (delay), and error rate.
QoS involves prioritization of network traffic. QoS can be
targeted at a network interface, toward a given server or router's performance,
or in terms of specific applications. A network monitoring system must
typically be deployed as part of QoS, to insure that networks are performing at
the desired level.34(*)
CHAPTER III: METHODOLOGY
III.1
INTRODUCTION
This third chapter describes the process for setting up an
Netowrk test lab. The study will involved the use of networking concepts. In
this study, the migration methodology will be used with well-defined steps.
This chapter also presents the software tools and hardware
needed to achieve these purposes.
III.2
MIGRATION METHODOLOGY
The migration methodology has been developed by IETF in order
to aid the network migrator to analyze and simplify the migration process. The
migration methods the IETF recommends are dual stacks and tunneling.
III.3
STEPS IN MIGRATION METHODOLOGY
The ideal migration methodology project plan should be broken
down into steps, which mirror the overall project development phases. These
steps consist of:35(*)
1. Determining Requirement
2. Understanding the existing System
3. Decision making
4. Testing
5. Deploying
6. Management
Each of these phases will be defined in further detail in the
following sections. These steps will significantly impact the outcome of this
project.
III.3.1 Determining Requirements
The first step is to determine what equipments have to be used
and software that are required to accommodate the new technologies that can
support IPv6.
III.3.2 Understanding the existing
system
The second step in any new implementation is to understand
what is currently on existing network. Current benchmarks of the IPv4 protocol
traffic must be obtained so they may be compared with benchmarks for the new
IPv6 traffic.
III.3.3 Decision making
The next step in the migration process is to decide among
transitions strategies mechanisms which one can be used. This step focuses on
finding the best migration method. The migration methods the IETF recommends
are dual stacks and tunneling. The dual stacks method refers to IP nodes that
support IPv4 and IPv6 protocols. The tunneling approach advocates running IPv6
packets over existing IPv4 infrastructures.
III.3.3.1 Dual Stack Transition Mechanism (DSTM)
Dual stack implies providing complete implementations of both
versions of the IP (IPv4 and IPv6).
The most straightforward way for IPv6 nodes to remain
compatible with IPv4-only nodes is by providing a complete IPv4
implementation.
IPv6 nodes that provide complete IPv4 and IPv6 implementations
are called "IPv6/IPv4 nodes". IPv6/IPv4 nodes have the ability to send and
receive both IPv4 and IPv6 packets. They can directly interoperate with IPv4
nodes using IPv4 packets, and also directly interoperate with IPv6 nodes using
IPv6 packets.
Even though a node may be equipped to support both protocols,
one or the other stack may be disabled for operational reasons. Here we use a
rather loose notion of "stack". A stack being enabled has IP addresses
assigned, but whether or not any particular application is available on the
stacks is explicitly not defined.
Thus, IPv6/IPv4 nodes may be operated in one of three
modes:
· With their IPv4 stack enabled and their IPv6 stack
disabled.
· With their IPv6 stack enabled and their IPv4 stack
disabled.
· With both stacks enabled.
IPv6/IPv4 nodes with their IPv6 stack disabled will operate
like IPv4-only nodes. Similarly, IPv6/IPv4 nodes with their IPv4 stacks
disabled will operate like IPv6-only nodes. IPv6/IPv4 nodes may provide a
configuration switch to disable either their IPv4 or IPv6 stack.
The figure below show dual-stack mechanism

Figure 3: Dual
Stack
Source: Own drawing
III.3.3.1.1 Address Configuration
Because the nodes support both protocols, IPv6/IPv4 nodes may
be configured with both IPv4 and IPv6 addresses. IPv6/IPv4 nodes use IPv4
mechanisms (e.g., DHCP) to acquire their IPv4 addresses, and IPv6 protocol
mechanisms (e.g., stateless address autoconfiguration [RFC 2462] and/or DHCPv6)
to acquire their IPv6 addresses.36(*)
III.3.3.2 Tunneling Transition Mechanism
Configured tunneling provides a means to carry IPv6 packets
over unmodified IPv4 routing infrastructures.
Tunneling can be used to deploy an IPv6 forwarding
infrastructure while the overall IPv4 infrastructure is still the basis.
Tunneling can be also used to carry IPv6 traffic by
encapsulating it in IPv4 packets and tunneling it over the IPv4 routing
infrastructure.
For instance, if an ISP still has an IPv4-only infrastructure,
tunneling allows you to have a corporate IPv6 network and tunnel through your
ISP's IPv4 network to reach other IPv6 hosts or networks.
Tunneling techniques is used to avoid order dependencies when
upgrading hosts, or routers.37(*)
The figure below shows how tunneling works.

Figure 4:
Tunneling
Source: IPv6 essentials, O'REILLY, ISBN: 0-596-00125-8,
page 170
IPv6 node 1 on an IPv6 network wants to send an IPv6 packet to
another IPv6 node 2 on another IPv6 network. The network between the two IPv6
nodes is an IPv4 network only.
1. IPv6 node 1 sends an IPv6 packet to Router1.
2. When router 1 receives the packet address, it encapsulates
the IPv6 packet in an IPv4 header and forwards it to router 2.
3. Router 2 decapsulates the packet and forwards it to its
final destination (the IPv6 node 2)
III.3.4 Testing
After the steps stated above, the migration to IPv6 is ready
to be tested. Comprehensive testing is required for application performance,
router/access device capacity and interoperability. It is recommended that all
testing be performed in an offline lab. This minimizes the impact on the
network during testing. Testing will provide also the documentation about test
results and will help us to analyze the QoS and performance of IPv6.
III.3.5 Deploying
In this study, we have not dealt with deploy step because it
requires to enable IPv6 applications and protocols and modification of the
entire network. Deploying network cannot realistically be done for several
reasons:
· Several types of router require a flash upgrade to
support larger IPv6 images or a memory upgrade to support the two concurrent
routing tables.
· Lack of IPv6 support from manufacturers for some
equipment. Some older equipment will never support IPv6.
III.3.6 Management
The final yet often forgotten step in the process is the
management. This step consists of any change in network. Change can be based on
some factors such as to add new equipment.
III.4 TRAINING
Training gives a thorough understanding of how best to put
IPv6 to work in their environment. As with any new technology, IPv6 requires a
learning curve for network managers and operations personnel.
For end users, the protocol is transparent, and there should
be no learning curve unless their application requires typing in explicit
addresses. Probably end users will not see much difference if their Internet
service providers run IPv6; all Internet applications should run transparently
on both IPv4 and IPv6. However, as new applications and devices running
IPv6 become available, end users will be able to expand the amount of
applications and devices they use over the Internet.
To assist network migrator, network managers and users in
becoming comfortable with IPv6, Cisco Systems has developed an IPv6 education
program that includes:
· Cisco IOS Software IPv6 e-learning class available from
Cisco.com
· IPv6 book available from Cisco
Press
III.5 ADVANTAGES AND
DISADVANTAGES OF MIGRATION METHODOLOGY
III.5.1 Advantages of migration
methodology
It is easy to interpret the results, compare and analyze the
Quality of Service and the Performance of this purpose.
The presented research aims to provide also a structured
migration methodology to aid the network migrator in choosing and implementing
optimal migration mechanisms as well as understanding and subsequently
optimizing the impact of the migration on the network.
III.5.2 Disadvantages of
migration methodology
Disadvantages include the fact that managing the process may
be more difficult because the IPv6 is a work in progress.
III.6
TOOLS
III.6.1 Software Tools
The following software utilities are used in this study:
· Microsoft Windows XP Professional. Operating
System for hosts to be used and installed.
· Cisco IOS used on the vast majority of Cisco Systems
routers and Cisco network switches.38(*)
· Cisco Router and Security Device Manager (SDM) is a
Web-based device-management tool for Cisco routers that can improve the
productivity of network managers, simplify router deployments, and help
troubleshoot complex network and VPN connectivity issues.39(*)
· Fedora Core: the platform on which IPv6 can be
installed. It is explained in the next chapter.
· The MaaTec Network Analyzer: a tool that allows to
capture, save, and analyze network traffic on a LAN Internet
connection.40(*)
III.6.2 Hardware
In our study, we used the following various hardware to set up
an Network test lab network.
· Three personal computers acting as clients.
System: Microsoft Windows XP.
Version: 2002
Service: Pack 2
Pentium IV
Central Processor Unit 2.53 Giga Hertz.
Hard disk 80 Giga Bytes.
Random Access memory 256 Mega Byte (MB).
· Two Routers:
Model type Cisco 2811.
Total memory 256 MB.
Total flash capacity 61 MB.
Cisco IOS 12.4T
· Two Switches:
Model type Catalyst 3560.
Total flash memory 32 Mega Bytes.
· Cross-over cable.
· Rollover cable.
· Straight cable.
CHAPTER IV: QUALITY OF SERVICES,
TEST AND ANALYSIS
IV.1 INTRODUCION
The purpose of this chapter that is the main part of this book
is to give a look on this new technology. The transition mechanisms have been
tested, a network analyzer has been used to analyze the traffics that are
passing through our test Lab. Another major reason of this chapter is to train
readers of this book to be familiar with the evolution of network
technology.
IV.2
NETWORK REQUIREMENTS
This section sets out to outline the requirements of IPv6
network. The IPv6 network involves different components:
IV.2.1
Operating Systems
Most of the modern operating systems now have two distinct IP
stacks to support both IPv4 and IPv6 at the same time. The list below shows the
list of platforms that supports IPv6 applications.
· Windows XP: Windows XP has IPv6 built in
· Windows 2000: Microsoft that release IPv6 runs on
Windows 2000. It does not work on Windows 95/98.
· Windows VISTA: IPv6 has been fully incorporated into
the operating system, it is installed by default.41(*)
· Linux: The All the Linux distribution are based on
Kernel (Kernel is the base operating system, which interacting directly with
the hardware and services of user programs) identified by its version. The
Linux kernel has supported IPv6 since version 2.2.x.
· Sun Solaris: IPv6 support is available from Solaris
version 8.
IV.2.2
Applications and Services
Networked applications and services must be modified, or
ported, to support IPv6.
Cisco routers and switches running one of the following
Cisco IOS Software releases are IPv6-capable: Cisco IOS Software releases
12.2T, 12.3M, 12.3T, 12.4M, 12.4T, 12.2S (and derivatives), 12.0S .Cisco 12000
Series routers and Cisco 10720 Router. Cisco IOS-XR Software (Cisco Carrier
Routing System-CRS-1, Cisco XR 12000 Series Router).42(*)
IV.3 ANALYSIS
The main objective of this step; it is to understand the
traffic characteristics of the network before applying new applications in the
existing one to ensure successful implementation. This step has also helped to
compare and analyze the result of our Network test lab.
Cisco
SDM tool has helped us to understand IP protocol traffics that are passing on
the network. With this tool we saw QoS Status of bandwidth and bytes which are
used by traffics which were passing through the network.
IV.3.1 Bytes
The figure below displays the bytes utilization statistics
defined by different traffics types.
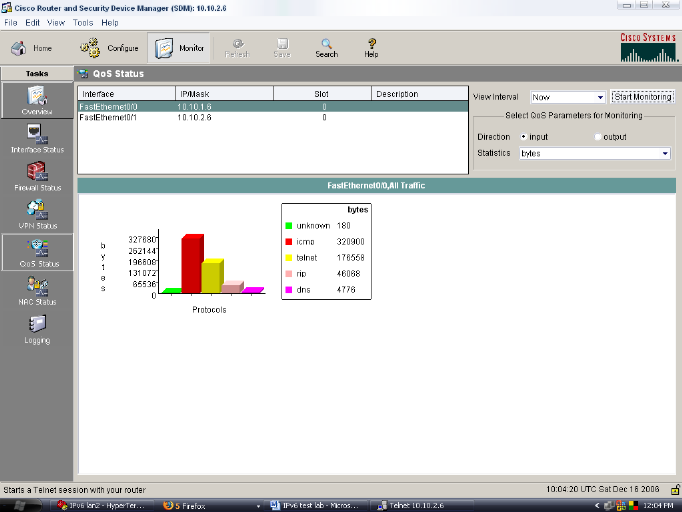
Figure 5: QoS
Status
Source: Cisco SDM
As shown in the figure above. The traffics bytes per protocol
that are passing in our Network test lab before configuring the IPv6 in the
network there are ICMP packet used to test the connectivity, Telnet packet used
to remote the computer connect to, Routing Internet Protocol (RIP) packet used
to route the packets through the network, DNS packet for resolving the domain
name, they are also other traffics that are not defined [unknown].
IV.3.2 Bandwidth
The figure below illustrates the bandwidth utilization for
protocols under different traffics that are sent on our test lab. The
bandwidths per protocols that are passing are ICMP packet, telnet packet. As
shown in the figure below the bandwidth consummation is very low regarding the
bandwidth available.
Bandwidth utilization is shown in Kilobits Per second (Kbps).
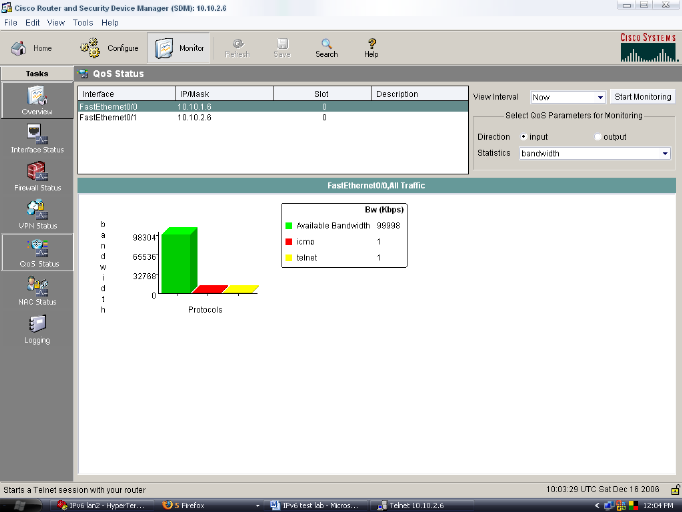
Figure 6: QoS of
bandwidth
Source: Cisco SDM
IV.4 TECHNIQUES MECHANISM
The objective of this section is to identify the different
transition mechanisms options available to a network while migrating from the
IPv4 to IPv6. These mechanisms are intended to ensure interoperability between
IPv4 and IPv6.
IV.4.1 Dual Stack technique
The objective of dual stack step is to guarantee a smooth
transition. In our study we decided to test dual stack. This technique performs
a full network software upgrade to run the two separate protocol stacks. It is
the simplest approach to introduce IPv6 without changing applications. It
supports IPv4 and IPv6 simultaneously, maintaining old IPv4 applications and
adding new ones to communicate with IPv6 nodes. The dual stack is for end
system.

Figure 7: Dual Stack
diagram
Source: Own drawing
IV.4.1.1 Dual-stack
configuration
Dual-stack configuration is simple. We first enabled both
routers to act as IPv6 router. We then configured with IPv6 and IPv4 addresses.
IPv6 configuration is different to IPv4 configuration; it has plenty option.
IPv6 does not use the subnet mask, it use a slash followed by prefix this
replace the big notation in IPv4 that use subnet mask; IPv6 can also be
configured automatically using stateless autoconfiguration on an interface. We
finally save the configuration. Appendix A gives a dual-stack configuration.
The dual stack configuration helped us to set up a Local Area
Network to test our Network test lab.
IV.4.1.2 Dual-stack Ping
results
Our dual-stack ping is test connectivity between two routers
that acting as IPv6/IPv4 node that obtains the IPv4 and IPv6 Round Trip Time
delays for a set of target nodes by running ping and ping6. From the dual-stack
ping results, we identified the percentage of dual-stack nodes reachable. The
result of this test shows that we success configuring a dual-stack
configuration, we have localized IP connectivity.
IV.4.2 Tunneling technique
Due to the lack of IPv6 ISP; during this study the tunneling
mechanism was not been tested because it required network integration and we
were not running on the ISP that support IPv6.
IV.5 TEST and ANALYSIS
The purpose of this step is to provide information about how
to make a network; configure and test IPv6 protocol functionality and its
features.
During the testing, we tested with minimum number of
computers. Individual computers have been used to clearly show the QoS and the
performance. The configuration, including IP addresses and all other
configuration parameters. This network test lab has been tested on a separate
network and services provided on the network to avoid the impact of the test on
the network.
The following illustration shows the configuration of the
Network test lab.

Figure 8: Network test-lab
diagram
Source: Own drawing
We made this Network test lab by configuring two routers with
both version of IP in order to forward and route packets across clients in this
network. The configuration procedure is given in the Appendix.
We installed IPv6 on the side of clients and assigned
statically the IPv4 addresses arranged in the appropriate network. The
installation is shown in the next section IV.6.
IV.5.1 Ping Results of Network
test lab
Our Network test lab ping results were to test the
connectivity between work-stations that are in the network. Testing the
connectivity between work-stations by using IPv4 addresses were different from
using IPv6 addresses.
Testing the connectivity between work-stations that are
assigned with IPv4 address can only be tested by using only one address but
with IPv6 address the connectivity can be tested with many addresses for
example pinging with IPv6 link local address, IPv6 site-local address, IPv6
addresses with embedded IPv4 addresses.
This is one of option that was upgrade to the IPv4, which is
one of QoS the devices that support IPv6 can have multiple addresses.
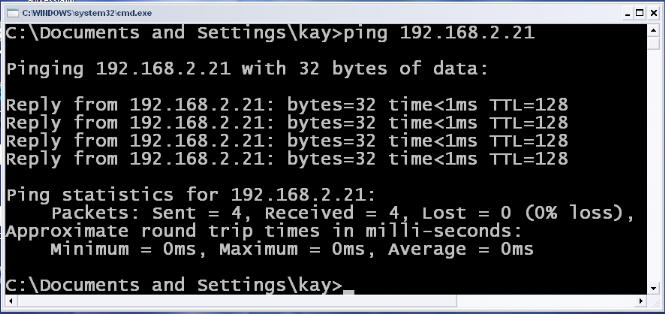
Figure 9: Ping IPv4
address
Source: Output Print Screen of ping IPv4
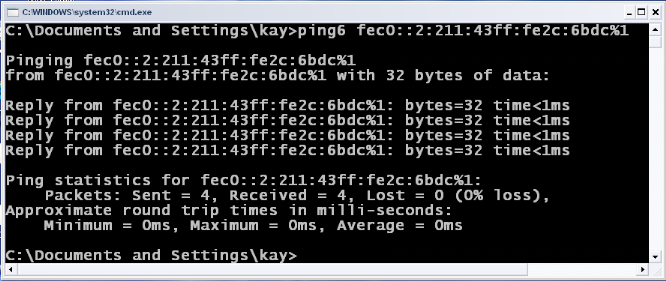
Figure 10: Ping6 IPv6
site-local
Source: Output Print Screen of Ping6
site-local
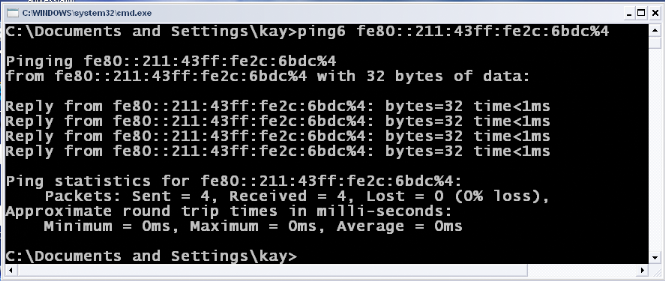
Figure 11: Ping6 IPv6
link-local address
Source: Output Print Screen of Ping6
link-local
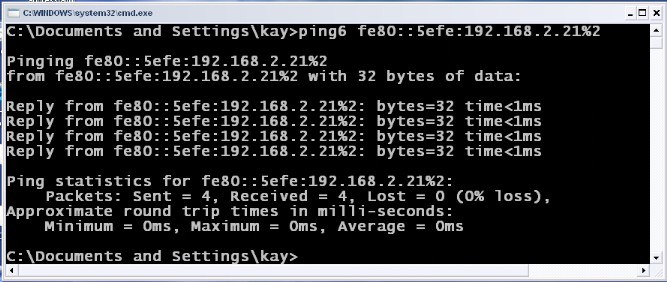
Figure 12: Ping6 IPv6
embedded IPv4 address
Source: Output Print Screen result of IPv6 embedded IPv4
address
As show in the figures below (figure 10, 11, 12); the TTL has
been removed in ICMP packets which can allow ICMPv6 packets to pass quickly
trough the network, and it can also allow ICMPV6 packets to test the
connectivity without dying until it reach its destination.
IV.5.2 Netwrok test lab Telnet
results
As we set a network that include both IP (a dual-stack); we
tested with telnet by specifying the IPv4 or IPv6 address of the remote
computer to connect to. From the telnet results, we were able to reach the
nodes of router or computer connects to. 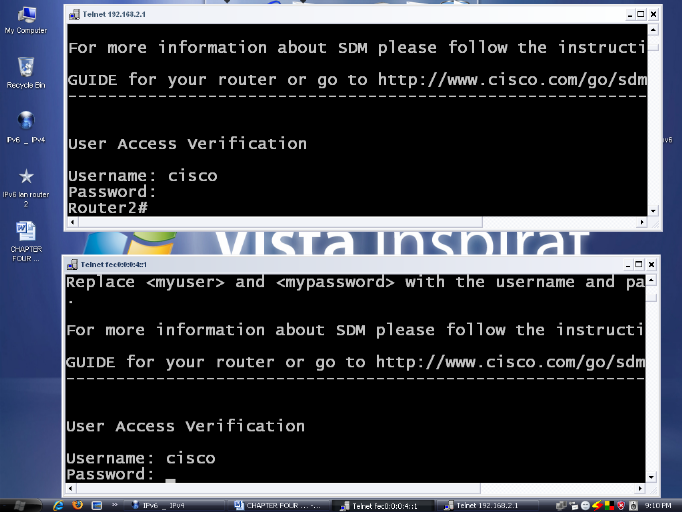
Figure 13: Telnet
IPv6/IPv4
Source: Output of Print Screen of Telnet
IV.5.3 Network test lab
Analysis
The Maa Tec Network analyzer has been used during testing the
Network test lab
IV.5.3.1 IP packets test
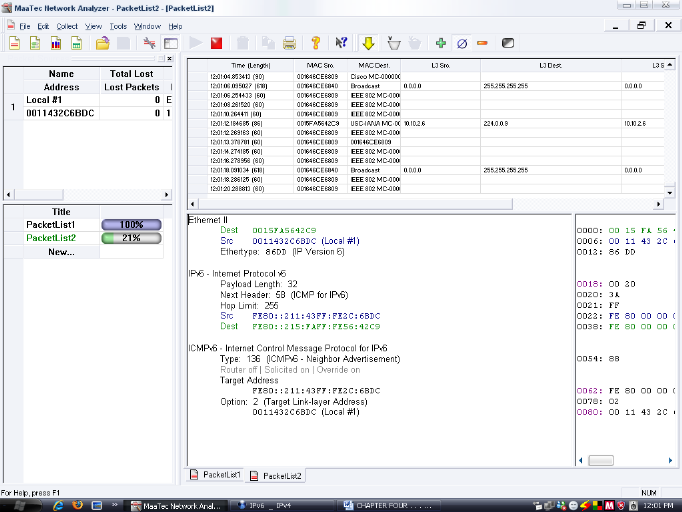
Figure 14: The packets
list.
Source: MaaTec Network analyzer/ Packet list
The figure above displays detailed information about the
packets. In the packets list, there columns that display information about time
and length of the collected packet, the network devices, Media Access Control
(MAC) address of the sender or receiver of the packet, the OSI layer of source
or destination source of the packet, type of service.
We selected among the packets captured in the layer column
where IP laid. The layer 3 (network layer) of OSI model provided the
information about the IP header of the system that sent or receive a packet and
we compared both IP headers format.
|
IPv6 Packet
|
IPv4 Packets
|
|
IPv6 - Internet Protocol v6
Ver|DS|Flow: 60000000
Version: 6
Traffic Class: 0
Flow Label: 0
Payload Length: 40
Next Header: 58 (ICMP for IPv6)
Hop Limit: 64
Src FE80::211:43FF:FE2C:BF3C
Dest FE80::211:43FF:FE2C:6BDC
|
IPv4 - Internet Protocol v4
Ver/IHL: 45
Ver: 4 Header Length: 5 (20 bytes)
Type of Service: 00
Precedence: 0 (Routine)
normal delay | normal throughput | normal reliability
Total Length: 60
Identification: 341
Fragmentation: 0000
may fragment | last fragment
Fragment Offset: 0
Time to Live: 128
Protocol: 1 (Internet Control Message)
Checksum: 45819
Src 192.168.2.21
Dest 192.168.3.11
|
Table 4: IPv6 and IPv4 Header
packet
Source: Maa Tec Network Analyzer
As shown in the table above the packets format is passing on
the same port and the way IPv6 packets are forwarded by paths are different
from those for IPv4.
This way IPv6 packets passes allow packets to pass quickly
trough routers.
As there is change in design of IP, the new one carries a
number of QoS. In IP header there is a good example of the features of QoS. The
header of IPv6 is simplified; it does not have many fields to be checked.
This QoS can provide to a network to be fast when packets are
traveling through the network.
IV.5.3.2 Network Test Lab Report
The table below displays the information about the Internet
Traffic per System and Protocol that are traveling through the network while we
were testing our Network Test lab.
Sunday, January 21, 2007, 5:45:00 PM - 5:50:00 PM
Internet Traffic per System and Protocol
|
Address (User)
|
Protocol
|
Sent packets
|
Rec. Packets
|
Total Packets
|
|
192.168.2.21
|
ICMP
|
20
|
0
|
20
|
|
192.168.3.11
|
ICMP
|
0
|
12
|
12
|
|
FEC0::2:211:43FF:FE2C:BF3C
|
ICMPv6
|
41
|
0
|
41
|
|
FEC0::2:211:43FF:FE2C:6BDC
|
ICMPv6
|
0
|
18
|
18
|
|
FE80::211:43FF:FE2C:BF3C
|
ICMPv6
|
4
|
0
|
4
|
|
FE80::211:43FF:FE2C:6BDC
|
ICMPv6
|
0
|
2
|
2
|
|
192.168.2.213
|
ICMP
|
0
|
8
|
8
|
|
192.168.2.21
|
Server Message Blocker
|
1
|
0
|
1
|
|
192.168.2.255
|
Server Message Blocker
|
0
|
1
|
1
|
|
FF02::1:FF2C:664D
|
ICMPv6
|
0
|
12
|
12
|
|
FEC0::3:211:43FF:FE2C:664B
|
ICMPv6
|
0
|
8
|
8
|
|
FE80::215:FAFF:FE56:42C9
|
ICMPv6
|
0
|
5
|
5
|
|
192.168.2.21
|
Telnet
|
38
|
0
|
38
|
|
192.168.3.1
|
Telnet
|
0
|
23
|
23
|
|
192.168.2.21
|
NETBIOS -Name Server
|
24
|
0
|
24
|
|
192.168.2.255
|
NETBIOS -Name Server
|
0
|
24
|
24
|
|
FEC0::2:211:43FF:FE2C:BF3C
|
Telnet
|
42
|
0
|
42
|
|
FEC0::4:0:0:0:1
|
Telnet
|
0
|
42
|
42
|
|
192.168.2.1
|
Telnet
|
0
|
15
|
15
|
|
Total
|
|
170
|
170
|
340
|
Table 5: Internet Traffic per
System and Protocol
Source: MaaTec Network analyzer/Report
These two 3D Bar (large) charts below show the packets sent
and the packets received every 5 minutes during we were doing the test. As
shown in those figures there are packets for IPv4 and packets for IPv6 because
in the network we configured the dual-stack one of the strategies mechanism of
migration from IPv4 to IPv6.
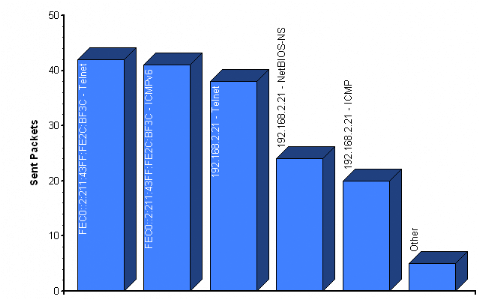
Figure 15: Sent
Packets
Source: MaaTec Network Analyzer/Sent Packets
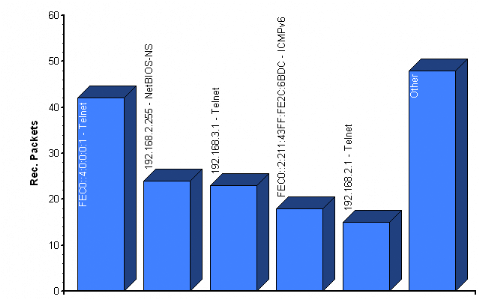
Figure 16: Received
Packets
Source: MaaTec Network Analyzer/Received
Packets
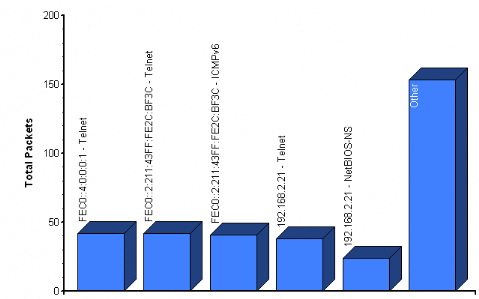
Figure 17: Total
Packets
Source: MaaTec Network Analyzer/Total Packets
The figure above shows the total packets of sent and received
of the activities done in the network Test Lab, it displays on the Y axis the
amount of packets sent (outbound) and received (inbound) per every 5 minutes on
the X axis.
IV.5.4 Summary of Test
The step of dual stack, one way of strategies mechanism
transition that we tested has been implemented efficiently into the existing
(IPv4 network) without changes, it can be interoperable and provide more
features such as rich connectivity between node with IPv6 (example IPv6 over
Ethernet: the link local can not be overlapped) no conflict can occur on
network which perform good performance on network. And a node with IPv6 that
gain multiple addresses that provide good QoS compared to a node with IPv4.
An organization or company that depends on the Internet to
migrate to IPv6 from IPv4 does not need to buy new equipment for IPv6; because
IPv6 is already a part of equipment and can be installed as a software upgrade.
It depends on the equipment of network capable of supporting IPv6, a network or
an ISP that has already migrated to IPv6.
IPv6 is a work in progress; it will take several years to be
deployed around the whole world. To replace completely IPv4 requires
uninstalling dual-stack, tunneling and other mechanisms that will permit to
jump on the IPv6.
IV.6 TRAINING
The purpose of this part is to
provide readers and end users of this book a brief description of concepts that
must be clear for installing and configuring IPv6 on their system. IPv6 can be
installed as a normal software upgrade in most Internet devices. Mastering
technology is not done by reading about it, so the followings platforms have
been shown in this book with plenty options. It is very easy, it took not even
five minute to configure it or install it.
IV.6.1
Install IPv6 on Windows XP
There are several ways to install IPv6 under Windows XP.
Win XP has an IPv6.exe tool used to configure IPv6 protocol.
1. The figure below shows the installation on Windows XP, in
command DOS/WINDOWS
To install IPv6 on Windows XP, simply go to.
Start Menu run shortcut [window key +R] open (command-line)
typing the command ipv6 install.
Or pass at Start Menu All programs Accessories Command
prompt typing the command ipv6 install.
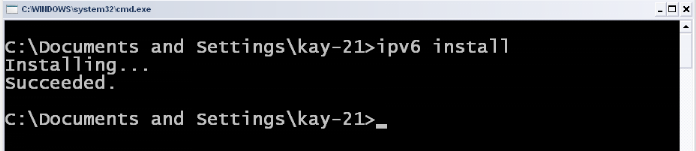
Figure 18: IPv6
install
Source: Win XP/DOS
2. Or install IPv6 protocol with the new tool for XP the netsh
(the ipv6 command will eventually be phased out in future releases of the IPv6
stack and completely replaced by netsh.), which is a command-line utility that
you can use to display or modify the network configuration and display all
sorts of statistics.
Simply go to start netsh from the command-line prompt to start
the utility and change to the context interface, then change to the context ip,
and finally to the context IPv6 where contains IPv6 configuration.
Go to Start Menu run open (netsh) interface ipv6 install
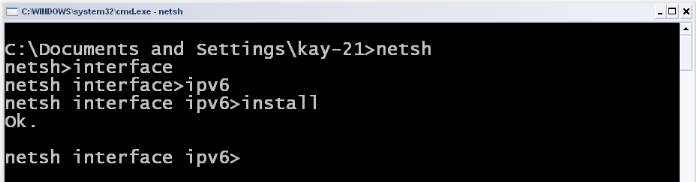
Figure 19: IPv6 install
with NETSH
Source: Windows XP/DOS
3. Install IPv6 passing through the Control Panel.
Go to StartControl PanelNetwork Connections
Right click on Local Area Connection and select Properties
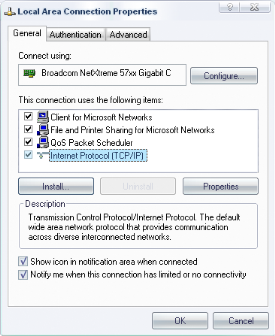
Figure 20: IPv4 node Local
Area Connection Status
Source: Windows XP/ Local Area Connection
Properties
Click on the Install button in the resulting Properties dialog
box
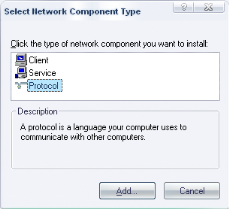
Figure 21: Network
Component / Protocol
Source: Windows XP/ Network Component
In the Select Network Component Type, select Protocol, then click
Add.
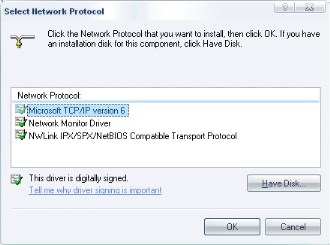
Figure 22: IPv6
install
Source: Windows XP/ Network Protocol
From the displayed list, choose Microsoft TCP/IP version 6.
Once this has finished installing, dismiss all those windows
dialog boxes.
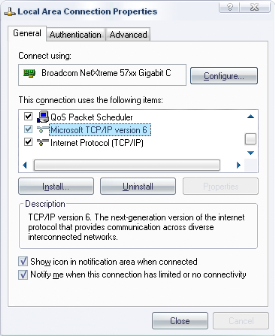
Figure 23: IPv4/IPv6 node
Local Area Connection Status
Source: Windows XP/ Local Area Connection
Properties
IPv6 does not appear in the list of components in the
properties of a LAN connection in Network Connections. To verify that IPv6 is
installed on Microsoft Windows XP host, type «ipv6 if», «netsh
interface ipv6>show interface» or «ipconfig» at the command
line. The command displays interface information. This description can be found
into the help and support under the system Win XP.
IV.6.2 Uninstall IPv6 on
Windows XP
After install IPv6 on the network adapters, it is not an
irreversible action; IPv6 protocol can be removed by uninstalling it using the
following as shown in the figure below and go back continue using happily IPv4
host.
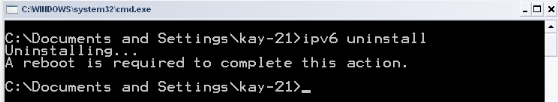
Figure 24: IPv6
uninstall
Source: Windows XP/DOS
After uninstall the IPv6, a reboot is required to remove
completely the IPv6 protocols on the interfaces.
IV.6.3 Difference between an
IPv4 and an IPv6 system with Windows XP
The following figure shows an example of an IPv4 only node
before installing IPv6; as shown in this figure the node that using the IPv4
has only one IP address.
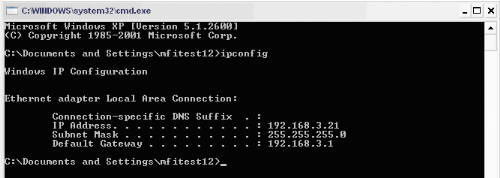
Figure 25: IPv4
address
Source: Windows XP/DOS
As shown in the figure below after installing IPv6, the node
that is installed with IPv6 has multiple IP addresses, it gains new features.
It has a complete support for both protocol versions. This type of node is
referred as IPv6/IPv4 node, capable of sending and receiving both IPv4 and IPv6
packets.
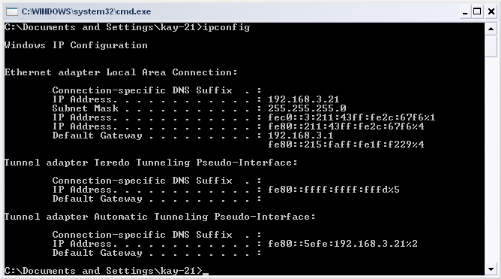
Figure 26: IPv6
address
Source: Windows XP/DOS
· The IPv4 address: the address that was assigned statically
(192.168.3.21).
· The link-local address: it is the combination of the
prefix fe80::/64 and 64 bit-interface identifier (the MAC address) that is
being transformed into the link-local address. Therefore the link local of the
example node is fe80::/64 and the Media Access Control address
00-11-43-2C-67-F6 is [ fe80::211:43ff:fe2c:67f6%4 ]
· The site-local address: it the address that is being
configured automatically by the router. It generates the address to the host
using its built-in configuration. [ fec0::3:211:43ff:fe2c:67f6%1
]
· The IPv6 embedded IPv4 address: it is the address that
is assigned by the Intra-Site Automatic Tunnel Addressing Protocol designed to
provide IPv6 connectivity between IPv6 nodes within a mainly IPv4-based
intra-network that does not have an IPv6 router in the site. It is the
combination of prefix (64-bit), the interface identifier (00005E) which follows
the prefix, following by byte FE that indicates that the address contains an
embedded IPv4 address, and the last four bytes that contain IPv4 address
written in dotted decimal notation. Therefore the address of the node shown
below is [ fe80::5efe:192.168.2.21%2 ]43(*)
IV.6.4 IPv6 with Linux
In this study, we used the Flexible Extensible Digital Object
and Repository Architecture (FEDORA) Core distribution of Linux. We used Fedora
Core release 3; it is based on Linux Kernel version 2.6.8.44(*)
To install the IPv6 on Fedora Core perform the following
steps:
Go to applications System Settings Network Edit Enable
IPv6 for the interface Activate (activating network device).
Figure 27: IPv6
installation in Linux
Source: Fedora Core
From the displayed list, enable the IPv6 interface, save the
configuration change [ctrl +s] and Restart the network services, at the prompt
shell, type the command below:
[root@FS-CS-CA ~]# service network restart
see if all
interface is [OK]
Or reboot the computer.
[root@FS-CS-CA ~]# reboot
IV.7 VERIFICATION OF
HYPOTHESIS
By verifying the hypothesis stated above, we can say that we
have succeeded. We managed to set a network which is running under one of the
transitions mechanisms; the dual-stack transition mechanism which is the first
step to migrate to IPv6.
Regarding the results of the test lab, we can also say that in
the network running IPv6 protocols there are better performance because there
are some fields that have been removed in IPv4 header which can provide high
speed in the network. And at the end users (clients) there is better
connectivity between clients because of the infinite life of IPv6 address which
provide more QoS.
CHAPTER V: CONCLUSION AND RECOMMENDATIONS
V.1 CONCLUSION
The main objective of this study was to prepare readers of our
book for the next step of networking technology evolution regarding the current
exponential growth of the Internet.
The objectives and goals of the study have been achieved
successfully:
1. A practical setting up LAN network for migration step was
done.
2. Comparison of two version of IP has been given.
3. Analysis of network with network application called MaaTec
Network Analyzer has been used to analyze network traffic.
We conclude by saying that the IPv6 is inevitable, will come
and will impact on all companies that maintain, implement or use IP networks.
So any organization that wants to evolve with the new technology, and upgrade
their network, it is right time to begin moving toward IPv6 in order to be in
touch with applications that will come with this new technology.
V.2 RECOMMENDATIONS
Basing on the findings of this study; we suggest that
organizations which depend on the Internet based on the IPv4 infrastructure to
start migrating to the IPv6 and require IPv6 addresses space from their ISP.
We also recommend future researchers of this project to
integrate the use of IPSec, the protocol for IP network-layer encryption and
authentication, which is built-in in IPv6 and the Mobile IPv645(*) which is IETF standard
communications protocol that is designed to allow mobile device users to move
from one network to another while maintaining their permanent IPv6 address;
this research requires an IPv6 network.
Another aspect of network management that we recommend to be
integrated in this project is to upgrade the devices that touch IP such as
routers in order to support IPv6 applications and to upgrade their backbone and
switching hardware anyway, and can use that as an opportunity to turn on IPv6
at the same time. This aspect is especially true for network manager who must
assure the quality of service expected by the users.
We do also recommend instructions and most of the disciplines
represented in their IT department to integrate IPv6 in institutions.
REFERENCES
BOOKS
The following lists of books provide references, which can be
read to learn more about IPv6.
· Silvia Hagen: IPv6 Essentials. First edition ;
ISBN: 0-596-00125-8; 2002
· Marc Blanchet: Migrating to IPv6: A
Practical Guide for Mobile and Fixed Networks. ISBN 0-471-49892-0;
2005.
· Douglas E. Corner: Internetworking with TCP/IP
principle, protocols and Architectures. Fourth Edition, ISBN
81-7808-444-9; 2000
WEBOGRAPHY
The following websites provide a list of e-references, for
easy reference.
http://www.ipv6.org
http://www.go6.net
http://compnetworking.about.com/od/networkdesign/g/bldef_qos.htm
http://compnetworking.about.com/od/networkdesign/g/bldef_qos.htm
http://en.wikipedia.org/wiki/Cisco_IOS
http://en.wikipedia.org/wiki/DHCPv6
http://en.wikipedia.org/wiki/IPv6
http://en.wikipedia.org/wiki/ICMPv6
http://en.wikipedia.org/wiki/Internet
http://en.wikipedia.org/wiki/IP_address
http://en.wikipedia.org/wiki/IPv4_mapped_address
http://en.wikipedia.org/wiki/IPv5
http://en.wikipedia.org/wiki/Ipv6#Special_addresses
http://en.wikipedia.org/wiki/IPv9
http://en.wikipedia.org/wiki/Steve_Deering
http://en.wikipedia.org/wiki/Www
http://mirrors.bieringer.de/Linux+IPv6-HOWTO/x459.html
http://searchnetworking.techtarget.com/original.html
http://www.cisco.com/en/US/products/ps6553/products_white_paper09186a00802219bc.shtml
http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
http://www.ciscopress.com/articles/article.asp?p=31948&seqNum=1&rl=1
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/ip-packet.html
http://www.faqs.org/rfcs/rfc2373.html
http://www.faqs.org/rfcs/rfc2874.html
http://www.faqs.org/rfcs/rfc3596.html
http://www.faqs.org/rfcs/rfc3775.html
http://www.Internetworldstats.com/stats.htm
http://www.ipv6.nectec.or.th/rfc2893.html
http://www.maatec.com/mtna/index.html
http://www.microsoft.com/technet/prodtechnol/winxppro/maintain/xpmanaged/15_xpip6.mspx
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/wcecomm5/html/wce50conipv6addresses.asp
http://www.protocols.com/pbook/tcpip2.htm
http://www.soi.wide.ad.jp/class/20020032/slides/09/7.html
http://www.usipv6.com/6sense/2006/may/article03.htm
http://www.webopedia.com/TERM/W/World_Wide_Web.html
APPENDIX
APPENDIX.
This appendix provides an overview of most commands that have
been used to configure the Network Test Lab (chapter IV):
Router1 (Cisco 2811)
Router1#configure terminal
Router1(config)#ipv6 unicast-routing
Router1(config)#interface FastEthernet 0/1
Router2(config-if)#ip address 192.168.3.1 255.255.255.0
Router1(config-if)#ipv6 enable
Router1(config-if)#ipv6 address fec0:0:0:3::1/64
Router1(config-if)#ipv6 rip cisco
Router1(config-if)#no shutdown
Router1(config-if)#end
Router1#write memory
Router1#configure terminal
Router1(config)#interface serial 0/2/1
Router2(config-if)#ip address 192.168.4.1 255.255.255.0
Router1(config-if)#ipv6 enable
Router1(config-if)#ipv6 address fec0:0:0:4::1/64
Router1(config-if)#ipv6 rip cisco
Router1(config-if)#no shutdown
Router1(config-if)#end
Router1#copy running-config startup-config
Router1#configure terminal
Router(config)#ip route 192.168.2.0 255.255.255.0 serial 0/2/1
permanent
Router1(config)#ipv6 route fec0:0:0:2::/64 serial 0/2/0
Router1(config)#ipv6 route FEC0:0:0:2::/64 fec0:0:0:4::2
Router1(config)#end
Router1#write memory
Router1#configure terminal
Router1(config)#router rip
Router1(config-router)#version 2
Router1(config-router)#network 192.168.3.0
Router1(config-router)#network 192.168.4.0
Router1(config-router)#network 192.168.2.0
Router2 (Cisco 2811)
Router2#configure terminal
Router2(config)#interface FastEthernet 0/1
Router2(config-if)#ip address 192.168.2.1 255.255.255.0
Router2(config-if)#ipv6 enable
Router2(config-if)#ipv6 address fec0:0:0:2::1/64
Router2(config-if)#ipv6 rip cisco
Router2(config-if)#no shutdown
Router2(config-if)#end
Router2#write memory
Router2#configure terminal
Router2(config)#interface serial 0/2/0
Router2(config-if)#ip address 192.168.4.2 255.255.255.0
Router2(config-if)#ipv6 enable
Router2(config-if)#ipv6 address fec0:0:0:4::2/64
Router2(config-if)#ipv6 rip cisco
Router2(config-if)#no shutdown
Router2(config-if)#end
Router2#copy running-config startup-config
Router2#configure terminal
Router2(config)#ip route 192.168.3.0 255.255.255.0 serial
0/2/0 permanent
Router2(config)#ipv6 route fec0:0:0:3::/64 serial 0/2/0
Router2(config)#ipv6 route fec0:0:0:3::/64 serial 0/2/0
Router2(config)#ipv6 route FEC0:0:0:3::/64 fec0:0:0:4::1
Router2(config)#end
Router2(config)#router rip
Router2(config-router)#version 2
Router2(config-router)#network 192.168.3.0
Router2(config-router)#network 192.168.4.0
Router2(config-router)#network 192.168.2.0
The full list of IPv6 command can be downloaded at
http://www.cisco.com/application/pdf/en/us/guest/products/ps5317/c2001/ccmigration_09186a008064eed2.pdf
* 1
www.usipv6.com/6sense/2006/may/article03.htm
(January 21, 2007)
* 2
http://en.wikipedia.org/wiki/Internet
(April 04, 2006)
* 3
http://www.webopedia.com/TERM/W/World_Wide_Web.html
(April 04, 2006)
* 4
http://www.Internetworldstats.com/stats.htm
(April 05, 2006)
* 5
http://en.wikipedia.org/wiki/Www
(April 05, 2006)
* 6
http://en.wikipedia.org/wiki/Internet_protocols
(May 02, 2006)
* 7
http://en.wikipedia.org/wiki/IPv4
(May 12, 2006)
* 8
http://en.wikipedia.org/wiki/IPv5
(May 12, 2006)
* 9
http://www.ipv6.org/ (May
12, 2006)
* 10
http://en.wikipedia.org/wiki/Steve_Deering
(October 01, 2006)
* 11
http://mirrors.bieringer.de/Linux+IPv6-HOWTO/x459.html
(June 09, 2006)
* 12
http://en.wikipedia.org/wiki/IPv9
(May 12, 2006)
* 13
http://en.wikipedia.org/wiki/IP_address
(May 30, 2006)
* 14
http://www.microsoft.com/technet/prodtechnol/winxppro/maintain/xpmanaged/15_xpip6.mspx
(May 12, 2006)
* 15
http://msdn.microsoft.com/library/default.asp?url=/library/en-us/wcecomm5/html/wce50conipv6addresses.asp
(June 02, 2006)
* 16 IPv6 essentials, O'REILLY,
ISBN: 0-596-00125-8, page 26.
* 17
http://www.faqs.org/rfcs/rfc2373.html
(August 13, 2006)
* 18
http://en.wikipedia.org/wiki/Ipv6#Special_addresses
(August 13, 2006)
* 19 IPv6 essentials, O'REILLY,
ISBN: 0-596-00125-8, page 31
* 20
http://en.wikipedia.org/wiki/IPv4_mapped_address
(May 13, 2006)
* 21
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/ip-packet.html
(September 15, 2006 )
* 22
http://www.protocols.com/pbook/tcpip2.htm
(October 08, 2006)
* 23
http://searchnetworking.techtarget.com/originalContent/0,289142,sid7_gci870277,00.html
(October 08, 2006)
* 24
http://www.ciscopress.com/articles/article.asp?p=31948&seqNum=1&rl=1,
(August 22, 2006)
* 25 Reference: Cisco
Networking Academy Program 2
* 26
http://technet2.microsoft.com/WindowsServer/en/library/c3541ba8-bf24-4298-93b8-7193ba8413b01033.mspx?mfr=true
(October 02, 2006)
* 27 Reference: Cisco
Networking Academy Program 2, Module 8
* 28
http://en.wikipedia.org/wiki/ICMPv6
(May 22, 2006)
* 29
http://en.wikipedia.org/wiki/DHCPv6
(May 22, 2006)
* 30
http://www.faqs.org/rfcs/rfc3596.html
(May 23, 2006)
* 31
http://www.faqs.org/rfcs/rfc2874.html
(October 21, 2006)
* 32
http://www.soi.wide.ad.jp/class/20020032/slides/09/7.html
(October 21, 2006)
* 33
http://www.ipv6.org/ (May
12, 2006)
* 34
http://compnetworking.about.com/od/networkdesign/g/bldef_qos.htm
(December 12, 2006)
* 35
http://www.usipv6.com/6sense/2005/oct/06.htm
(October 19, 2006)
* 36
http://www.ipv6.nectec.or.th/rfc2893.html
(October 31, 2006)
* 37 IPv6 essentials, O'REILLY,
ISBN: 0-596-00125-8, page 170
* 38
http://en.wikipedia.org/wiki/Cisco_IOS
(September 20, 2006)
* 39
http://www.cisco.com/en/US/products/sw/secursw/ps5318/index.html
(September 21, 2006)
* 40
http://
http://www.maatec.com/mtna/index.html (December 16, 2006)
* 41
http://en.wikipedia.org/wiki/Windows_vista
(November 08, 2006)
* 42
http://www.cisco.com/en/US/products/ps6553/products_white_paper09186a00802219bc.shtml
(September 21, 2006)
* 43 IPv6 essentials, O'REILLY,
ISBN: 0-596-00125-8, page 179.
* 44 Fedora Core is a Red Hat
Package Manager based Linux distribution, developed by the community-supported
Fedora Project and sponsored by Red Hat.
* 45
http://www.faqs.org/rfcs/rfc3775.html
(November 18, 2006)
| 


