Figure 4.9. Flowchart of the proposed system
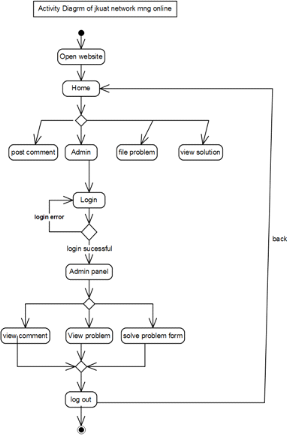
Figure 4.10. Activity diagram of the proposed
system
4.4.6.5 Analysis of
network traffic
This stage involve the verification of set of application
protocol used in the network and determination the application traffic pattern.
For our network I used the Wireshark Network Analyzerv.1.106
to capture and analyses the traffic. The figure below shows the network traffic
associated with protocol.
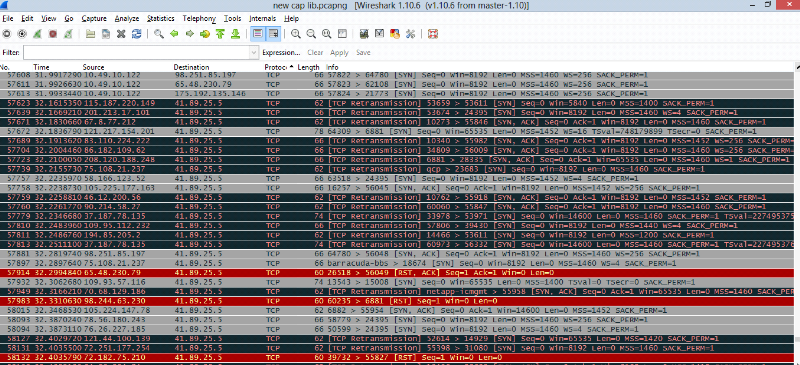
Figure 4.11: network traffic and protocols
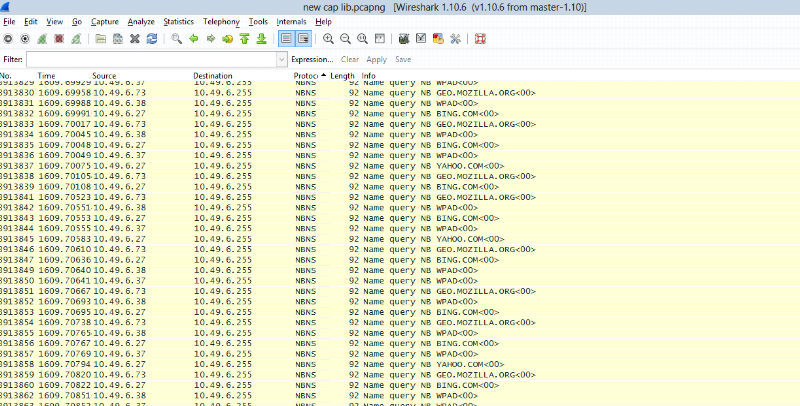
Figure4.12: Jkuat karen network traffic and
protocols
Fig 10 and 11 show the traffic within the network by providing
source and destination IP address during the transmission of package and
protocols which have been used.
4.4.6.6 Strength of
the current network:
· Good quality wiring.
· Reusability of existing equipment e.g. switches.
etc.
· Physical security to access critical location.
· Adequate space for data center.
4.4.6.7 Weakness of
the current network:
The current network has the following weakness:
· No redundancy whereby we have large failure domain,
link failure and device failure.
· No state full firewall the existing firewall can
perform filtering
· Poor maintenance of network infrastructures.
· Manageability of network, in case of problem the
technician or network administration need to be physical to the campus, which
is losses of time and resources.
· Switch synchronization issue , in case there is a
problem with electricity the network take time synchronize so that the use can
access
· Limited scalability: the network users grow rapidly
than expected, which affect the network users and required to upgrade to
support future users.
· There is only one VLAN in the current network, we need
to create more VLANs.
· Manage end point to protect network by verify id.
| 


