II.7.3. Overview of security of E-commerce network
In the previous sections, the research presents an overview of
threats that e-commerce and e-payment systems are likely to face.
Because of the diversity of threats and the way the networks are
attacked in today's internet era, organization or business cannot rely on a
single security technology; it must use security technologies at different
layers of the network.
Figure 7 below shows the three layers of the network which needs
to be protected.
Figure 6: layered security
Source: Turban et al. 2008, p 532
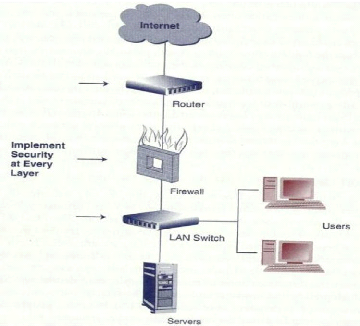
- Router level : perimeter security to internet
- Firewall: isolation of traffic communication between the
internet and the LAN - LAN switch: access security on local resources
Page | 27
II.7.3.1 Firewalls
Turban et al. (2008, p 533) defines firewall as a network
resource «consisting of both hardware and software that isolates a private
network from a public network».
Firewall examines all packets passing through it and allows or
denies the traffic according to the rules defined by the network
administrator.
Firewall can protect against many threats such as unauthorized
access, viruses, spams, harmful macro, applications backdoors, etc.
In e-commerce environment, firewall is used to block all
packets coming from un-trusted source or accessing to a specific resource on
the LAN.
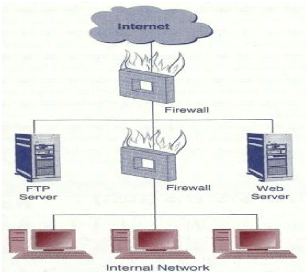
II.7.3.2 Demilitarized zone (DMZ)
Demilitarized zone is defined by Turban (Turban et al., 2008,
p534) as «a network area that sits between an organization's internal
network and the internet, providing physical isolation between the two networks
that is controlled by rules enforced by a firewall».
In e-commerce infrastructure web server will sit in the DMZ,
publicly accessible area and the database server will be installed in the
internal LAN protected by another firewall. In such deployment, network has two
firewalls to hardener the security.
Figure 7: DMZ deployment
Source: Turban et al.,2008, p535
Page | 28
II.7.3.3 Personal firewalls
Actually many home users have broadband connection to the
internet which allows them to get permanent connection to the Internet. This
permanent exposure to internet expose computer to attacks.
Personal firewall have been developed to protect desktop or
laptop by monitoring traffic flowing on the LAN interface card and taking
action according to the rule defined by the user.
II.7.3.4 Virtual Private Network (VPN)
G. Schneider (2011, p 86) defines a Virtual Private Network as
«an extranet that uses public networks and their protocols to send
sensitive data to partners, customers, suppliers, and employees using a system
called IP tunneling or encapsulation».
IP tunneling creates a private communication channels on the
internet in which information is encrypted to make it invisible to the other
internet users which are not involved in the communication transaction.
Protocol tunneling permits to encrypt data packets and
encapsulate them into packets to ensure confidentiality and integrity of data,
to be transmitted over the internet.
II.7.3.5 Overview of intrusion detection systems (IDS)
The necessity of monitoring the Information system for
unauthorized access permits the development of special systems and software
that can monitor activity on the network and detect illegal activities.
These appliances and software are called Intrusion prevention
system (IDS). II.8. Securing e-payment systems for B2C e-commerce
E-commerce needs a special payment system to enable online
payment of goods and services sold online.
According to the Laudon's (Kenneth C. Laudon and Jane P.
Laudon, 2006, p416), «electronic payment systems for the internet include
systems for digital credit card payments, digital wallets, accumulated balance
payment systems, store value payment systems, digital cash, peer-to-peer
payment systems, digital checking and electronic billing presentment
systems».
With the development of mobile telephony, another payment
system is available and consists of paying good and service using mobile phone.
This is known as m-payment system and will be developed shortly in e-commerce
transaction.
Page | 29
| 


