II.8.1 Payment cards systems
Payment cards are cards with payment of financial information
embedded in an electronic chip and which can be used for payment.
Three kinds of cars are currently used: (Turban et al., 2008,
p551)
? Credit card ? Debit
? Charge card
Card processing overview
Card payment processing consists on authorization of the
transaction and the settlement of the money.
Authorization is the phase during which verification is done to
check the validity of the card and the availability of the fund to be paid for
the transaction.
Settlement is the phase which consists on the transfer of money
from the buyer's card bank account to the seller's account.
Payment processing is a service offered by payment processing
service Provider (PSP).
Figure 8: Processing of a card transaction
Source: Gary
Schneider, 2011, p.501
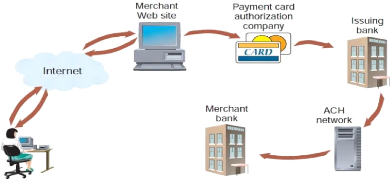
Page | 30
The most threat for payment card is «the
fraud»; and tools have been developed to combat it (Turban et
al., 2008, pp 553-554).
> Address verification system (AVS): seller compare the
shipping address entered on the e-commerce portal with the address contained in
file at the cardholder's bank.
> Manual review: staffs review manually suspicious
transactions orders to detect fraudulent transaction. This method can be used
on business with small amount of transactions.
> Fraud screens and automated decision models: Intelligent
systems which use automated rules to determine if the transaction can be
accepted rejected or suspended.
> Card verification number (CVN): this number is printed on
the back of the credit card; the verification will ensure that the buyer has
the card into his hands. This verification will not be useful in case of stolen
number.
> Card association payer authentication services. This
service is provided by card issuer and offers the possibility for the card
holder to register with the system to ensure the protection of the card.
Merchant web portal will interact with this service to validate the
authenticity of the card. Mastercard offers «Mastercard securecode»
and Visa the «verified by visa» to authenticate and certify their
cards.
> Negative file. Customer and information about the
connection such as IP address name, shipping or billing address, contact
numbers, etc are stored in a file. When the transaction takes place on the web
portal it is matched against the information contained in the file and flag in
case of problem.
II.8.2 Electronic cash
Electronic cash (e-cash or digital cash) is «a general
term that describes any value storage and exchange system created by a private
(non-governmental) entity that doesn't use paper documents or coins and that
can serve as a substitute for government issued physical currency» (G.
Schneider, 2011, p502).
Security issue of e-cash
As for the credit card payment, privacy and security
of the transaction is the most important issue for e-cash
implementation in the e-commerce business.
Fraud is a big concern for e-cash; therefore
security system must be in place to prevent double spending which can happen
while the electronic cash is submitted twice for the same cash amount to two
different merchants.
To prevent this situation, cryptographic algorithms are
creating tamperproof electronic cash that can trace back the transaction to its
origin.
Page | 31
The e-cash has a significant disadvantage because it doesn't
provide an audit trail and can be used as money-laundering (conversion of
illegal owned money to cash) system.
E-cash needs to be supported by a strong regulation to
define standards with the supported secured system and banking in order to be
widely accepted as an alternative to credit/debit card.
| 


