
Publier un mémoire
Consulter les autres mémoires

|
Publier un mémoire Consulter les autres mémoires |
|
|
The data-processing audit must have rules and principles which frame its application. One to that data processing has a direction only if its finality is defined : checking of the application of the objectives of the direction, examination of the effectiveness or the safety of the system, of the reliability of an application, controls tax, legal, legal expertise, etc
Auditer in a rational way is the fact of clarifying the finalities of the audit, then to deduce from them the means of investigation considered to be necessary and sufficient.
The finality of the audit data-processing, whatever its standard (intern, external, contractual, legal, etc) is always to give an opinion on the information system and especially on the execution of its preset objectives.
Several rules govern the data-processing audit such as :
· The data-processing mission of audit is rather complex. It must be cut out to manage to reconstitute a plan with clear and significant stages.
· When the task of the listener is well defined, it should not overflow about it. The listener must always respect the limits of his mission. For example, if it is requested from a listener to check the safety of an application, and that it of it is satisfied, it is completely indifferent to know if the results are exact, because it is a question of reliability.
· The results of the data-processing audit must be evolutionary (opening of recommendations on the future and not simply acknowledgment of failure), coherent and exact (reliability of the conclusions).
· The safety of the audit applies to the working papers and the reports/ratios, i.e. their not-diffusion with recipients not - authorized.
By complying with these rules, the Listener can affirm to have made a study of the significant elements and to have to identify the zones of existing risks.
The evolution of communication and information technologies confronts the company at the many new risks. In addition to the usual risks met in any mission of audit, the data-processing risks contribute to the increase in the vulnerability of the systems.
Within the framework of the missions of data-processing audit, the listener must take into account the effect of synergy of the two types of risks : Risks of audit and risks data-processing.
In what follows, one will be interested to present the two types of risks :
The listener must resort to his professional judgment and to define procedures of audit aiming at reducing the risk to a low level.
The standards of the IFAC define the risk of audit as being «the risk which the listener expresses an incorrect opinion because of significant errors contained in the financial statements. It is subdivided in three components: the inherent risk, the risk related to control and the risk of not-detection.
· The inherent risk : is the possibility that the balance of an account or that a category of transactions comprises significant errors isolated or cumulated with errors in other balances or categories of transactions, because of insufficiency of internal audit.
· The risk related to control : is the risk that an error significant in a balance of account or a category of transactions, isolated or cumulated with errors in other balances or categories of transactions, nor is not prevented or is detected, and corrected at the appropriate time by the countable systems and of internal audit.
· The risk of not-detection : is the risk that the controls implemented by the listener do not manage to detect an error in a balance of account or a category of transactions which, insulated or cumulated with errors in other balances or categories of transactions, would be significant ».

Figure 1: Risks of audit
The data-processing risk is defined as being «any event which while affecting an information processing system is likely to involve damage and/or losses with the company » 2(*).
To face the evolution of these risks, the countable system envisaged the risk management like a principal component of the process of audit internal.
These risks must undergo actions of analysis and evaluation in order to encircle them and analyze them to be able to found the policy of adequate safety.
The sources of risks are :
· Technical problems : It is of deterioration of the software and the data, of breakdowns or destruction of material, etc
The technical problems find birth of the immense complexity of the information processing systems.
To be able to avoid reflected them direct these problems, the company does not have to limit itself to the specific actions of maintenance. It is necessary to analyze these problems (to formalize the history of the breakdowns) and to envisage effective policies to ensure the continuity of the exploitation.
· Error: The error can appear under various aspects of which the organisational insufficiency, bad protection, negligence, etc
Many faults of safety are created and exploited by the users. The latter are not sensitized with this type of problems.
The error relates to all the dangers to which an organization must face aiming at the safety and the reliability of its processes and its treatments.
· Disasters natural and accidents: They are the fires, the floods, the strikes, the storms, the explosions, the attacks, etc
The company must adopt and set up safety requirements appropriate (smoke detector, gas-detector, air-conditioners, etc) for stage to these risks.
In the event of supervening of accidents, the company must envisage plans of help or continuity of exploitation.
· Ill will and fraud : It is in particular of the basic diversions, the intrusions, the flights, the destruction, etc
The human component is the factor of the most important risk. Indeed, nearly 80% of the attacks are made by the employees of the companies. Being given the vulnerability of the information processing systems, the computerized environment represents the ideal medium for the development of the fraudulent actions.
These actions can be summarized in operations of sabotages, espionages, wastings and of handling of data at nonprofessional ends.
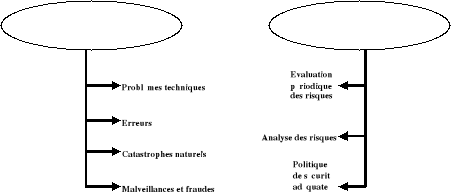
Figure 2 : Data-processing risks
* 2 www.sécurité-informatique.enligne-france COM