
Publier un mémoire
Consulter les autres mémoires

|
Publier un mémoire Consulter les autres mémoires |
|
|
University of the South
Higher school of Trade of SFAX

Master specialized New Technologies & Countable, Financial and Tax Management
Review of the module « accounts receivable » of software package JD EDWARDS of an oil company within the framework of a mission of financial audit
Worked out by :
Bacem Jarraya
Framed by :
Mr. Kamoun Moez
Mr. Khoufi Walid
Organization of reception : PriceWaterhouseCoopers Tunisia
SYNOPSIS
GENERAL INTRODUCTION 1
PART A: TO THAT INFORMATION SYSTEMS 2
1 CONTEXT OF WORK 3
1.1 TALLY OF DEVELOPMENT OF WORK 3
1.2 PRESENTATION OF THE CABINET 3
1.3 PRESENTATION OF THE COMPANY SUBJECT OF OUR STUDY 5
1.4 OBJECTIVE OF THE MISSION 5
2 TO THAT DATA PROCESSING 6
2.1 INTRODUCTION 6
2.2 PRESENTATION OF THE CONCEPT 7
2.2.1 Definition 7
2.2.2 Principles and rules of audit 8
2.2.3 Risks 9
2.2.4 Techniques of audit 12
2.3 COURSE OF THE DATA-PROCESSING AUDIT OF AN APPLICATION IN SUPPORT TO THE FINANCIAL AUDIT 13
2.3.1 Awareness 14
2.3.2 Control application 14
3 AUDIT OF THE ERP 19
3.1 PRESENTATION 19
3.1.1 History 19
3.1.2 Definition 22
3.1.3 Principle 35
3.1.4 Actors of the market 35
3.1.5 Needs for the ERP 36
3.1.6 Contributions of the ERP 39
3.1.7 Limits of the ERP 40
3.2 AUDIT OF THE ERP 41
3.2.1 Components of a ERP 41
3.2.2 Objectives of audit of a ERP 43
CONCLUSION LEFT A 46
PART B : DATA-PROCESSING MISSION OF AUDIT IN SUPPORT WITH THE FINANCIAL AUDIT (CASE OF AN OIL COMPANY) 46
1 PRESENTATION OF THE INFORMATION SYSTEM OF THE COMPANY 47
1.1 DEFINITION OF AN INFORMATION SYSTEM 47
1.2 CARTOGRAPHY OF THE SYSTEMS 48
1.3 APPLICATIVES CARDS 50
2 REVIEW OF THE PERMANENT DATA, THE CLIENTS' ACCOUNTS AND THE SAFETY OF J.D. EDWARDS 51
2.1 STEP 51
2.2 WORKING TOOL 52
2.3 DESCRIPTION OF CONTROLS 53
2.3.1 Controls and tests of the modules of software package J.D. Edwards 53
2.3.2 Safety of JDE 61
2.3.3 Documents to be consulted 63
CONCLUSION LEFT B 68
GENERAL CONCLUSION 69
APPENDIX 70
BIBLIOGRAPHY 72
GLOSSARY OF THE ACRONYMS 73
LIST FIGURES 74
The companies evolve/move in an increasingly complex and turbulent environment. The decisions which were in the past more or less easy to take in a simple and stable environment, present currently more difficulties in this risky environment. Any decision, which is internal or external, requires the taking into account of the various facets of this environment. Information thus takes an importance increased for a good decision-making. But the quality of this decision depends on the quality of information on which one bases oneself to take it.
Among this information necessary to the external people with company (investors, financial organizations, etc), countable and financial information occupies a dominating place. The guarantee of the quality of this information, depends on the opinion of an independent professional, in particular the auditor. It constitutes the best indication of the degree of confidence than one can grant to this information.
The opinion of the listener must be pressed on a very complete examination of the financial documents and corresponding supporting documents, and the purpose of it is to indicate if these documents reflect the real financial standing of the company.
The listener must also give his opinion on the internal system of audit of the company with the aim of bring a help to the customer and to allow a reduction of wide traditional work of audit.
In the missions of audit, the information processing systems take importance more and more. The listeners are from now on regularly confronted with countable or financial systems based on information processing systems in the exercise of their legal, contractual missions or interns. However, these information processing systems undergo an increasingly fast evolution. If they estimate, at the beginning, that it is necessary to treat data processing separately, the listeners are convinced, today, that data processing must be integrated in their professional step and each one of their concerns.
Thus, the approach of audit, usually adopted in the companies, must answer this new context and the new-born risks.
An action of levelling of the approach of audit is essential on the professional organizations in the world and the international cabinets. Thus these professional organizations were not long bringing and in updating the hot lines and the minimum of diligences for one to that in a computerized medium.
The international cabinets of audit develop suitable methodologies more and more and make large investments to adapt the approaches of audit to an increasingly complex and turbulent environment become.
In addition to these efforts, the legislation, jurisprudence and the doctrines on an international scale grew rich by new rules intended to regulate and control certain aspects of the computerized systems.
In this increasingly complex context, the listener is vis-a-vis new problems to which it must find solutions. He must acquire a sufficient knowledge as regards data processing to be able to plan, direct, supervise and re-examine his work.
Throughout his work, the listener evaluates the degree of the need for data-processing competences particular for the realization of the audit. If it is in this situation, it is obliged to request the assistance of a professional having sought competences, it can be a question of a collaborator or a specialist as regards audit in the external information systems to the entity.
The objective of this memory is to present the data-processing step of audit, to define its specificities when it is established within the framework of one financial audit and to study the case of a data-processing mission of audit of a module of a software package of management integrated in an operative company in the oil sector.
This memory, thus, will be structured in two parts :
· The first part will be devoted to the presentation of the audit of the information systems in support to the financial audit. It will treat, initially data-processing audit in a way General and in second place of the audit of the software packages of integrated management more particularly.
· The second part will be devoted to the study of a practical case. It is about the audit of a module of a software package of management integrated within the framework of a mission of financial audit of an operative company in the oil sector.
PART A: TO THAT INFORMATION SYSTEMS
This work fits within the framework of a report of end of New studies of Mastère Spécialisé «Technology and Management Countable, Financière and Tax».
The achievement of this work required efforts of study as well as the participation with the team of risk management (GRMS) of PwC in missions of audit of information systems (re-examined data-processing system checks, re-examined modules of a ERP, etc).
Operating in the field of the audit and the council, the world firm PricewaterhouseCoopers is present in 150 countries of the world through its 881 offices. It employs approximately 125.000 people and carries out an annual sales turnover of 17 billion dollars. This firm is present in 22 country of French-speaking Africa of which Tunisia.
In Tunisia, the group of the companies of council and founded audit m.t. B.F/CIF/CIF International in 1983, member (Full Member) of the international firm PricewaterhouseCoopers, employs more than 80 people having various profiles :
· Engineers ;
· Countable Experts ;
· The Financial ones ;
· Lawyers ;
· Data processing specialists.
The statute of Full Member allows PwC Bureau of Tunis :
· To use the new techniques audit council ;
· To reach data bases of «Best Practices » conveying a know-how constantly updated ;
· To profit from a continuous training scheme and this, on all the levels of the hierarchy ;
· To undergo a systematic and rigorous quality control.
The office includes/understands four departments :
Ø To that & Audit Office (Insurance):
The department TO THAT undertakes missions of conventional and legal audit in accordance with the generally allowed standards by the profession in Tunisia. Its formal opinion on the financial statements gives the insurance that those do not contain any error or omission which could significantly affect the financial standing or the result of the operations of the company.
Ø Management consultant, Management & Data processing (LOW) :
The department the COUNCIL generally undertakes actions of organization and reorganization of one or several functions of the company with an aim of helping the customers with the decision-making and with a greater control of management.
The assistance that the consultants bring to the organizations private or public aims to allow a better use of their resources, to establish the structures best adapted and to employ the most powerful methods and tools.
To meet these needs, the cabinet developed its expertise in the fields of consultant management and management (Strategy of development, Organization and administrative management, financial Gestion, countable Organization, Contrôle of management, Production control, commercial Gestion), of data processing consultant (strategy and information policy, Audit of the information processing systems) and of evaluation of companies
Ø Financial services (CF) :
This department carries out various types of missions such as the evaluation of the companies for their privatization or at the time of a fusion, the viability studies, the reorganization of the companies, the development of the Plane Business, etc
Ø The Legal & Tax Council (TLS) :
The success of a company depends for a considerable share on its choices vis-a-vis a fiscal, legal rule and economic complex and changing.
The services of the cabinet primarily aim to optimize these choices, i.e. to allow the companies which it advises to avoid constantly the obstacles resulting from these regulations and to seize opportunities that they present.
The council and the assistance touch the following fields :
· Taxation ;
· Company law ;
· Social right ;
· National and international contracts.
The policy of the cabinet is to ensure its customers a personalized service, i.e., answering completely and in a practical way each one of their problem. The presence of specialists having thorough knowledge in the various fields in the regulation in Tunisia and abroad makes it possible to bring to each problem an adapted answer.
The coordination of these specialists is ensured by a single person in charge, privileged interlocutor of the customer, with whom this one remains in contact and which thus has a total knowledge of its file.
During my training course I belonged to team GRMS (Total Risk Management Solutions) of the department council which carries out inter alia missions of audit of the information systems.
N.B : For reasons of confidentiality, the prone name of the company of our study will not be mentioned. One will limit oneself throughout the presentation to allot the name of «studied Company ».
The installation of a Software package of Management integrated (PGI) in a company cannot pass unperceived and this, because of the radical changes which accompany its installation like with emergence by new techniques on the level of the treatments of the data.
It is in this logic that the team of financial audit of PwC entrusted in-house, within the framework of its work of certification of the accounts of an oil company, with team GRMS the task to proceed to the review of the permanent data «Master Dated », of the module accounts receivable «A/R : Accounts Receivables » and of the standard reports/ratios of integrity of the PGI « J.D. Edwards ».
This mission aims at providing to the team of financial audit an insurance as for the integrity and the credibility of the data processing such as they are carried out by the software package. The results of this work will be the base of choice of the approach of audit of the team of financial audit.
It is in this context that I was integrated in the data-processing team of audit of PricewaterhouseCoopers in order to evaluate the data-processing controls conceived around the modules of J.D. Edwards, to test them and thus define the level of suitable risk which will constitute the base of choice of the strategy of audit.
Communication and information technologies are defined as being «the whole of data-processing technologies and telecommunication which allow the treatment and the exchange of information and the communication built around the computer and telephone »1(*).
Many information systems based on new communication and information technologies (NTIC) arrive in response to several problems encountered by the companies. These last evolve/move with the constraints imposed by modern management and those of information technologies following constant efforts of development of their information system.
These technologies touch more and more the companies throughout the world. Indeed, these last become increasingly computerized and much of them converge towards the solutions integrated by adopting the approach software package.
In addition, each day, several companies turn to the new technology of the Internet with the intention to increase their customers and to prospect unexplored markets.
This technology becomes one of the major concerns of the Tunisian companies and this, taking into account the phenomena of globalisation and liberalization as well as emergence of the new economy.
This spectacular evolution of data processing on all the levels and its penetration in all the fields of the company allows an update and a division of the data in real time, an integration of the financial and operational information systems and especially of the interactive economic exchanges of the company with its customers like with its suppliers (E-trade, E-business, etc)
This metamorphosis causes a considerable amplification of the dependence of the companies towards their information processing systems and affects their countable systems and of internal audit.
The introduction of the information processing systems and new communication and information technologies into the treatments of the company generates a total dematerialization (zero paper) of the transactions. This dematerialization causes an absence of tangible evidence (Absence of documents of entry, absence of visible frames of reference, absence of visible documents of exit).
The development of the information processing systems affects the level of safety of the systems while making them more vulnerable and causes new risks for the company. These risks touch as well the data-processing function as the automated treatments.
· The multitude of the incipient risks (physical, data-processing, legal and tax) obliges the companies has to become more conscious of the gravity of the situation. These last must adopt effective strategies as regards information system security.
· To face these risks, the companies must be based on standards and specific models of safety.
· In addition to the application of the standards, the companies feel more and more the importance and the contribution of the missions of data-processing audit.
In its work «Practice of the data-processing audit », Jose Plans defines the data-processing audit as being : « A methodological examination of the results or data-processing structures by an independent and qualified person with an aim of expressing an opinion on their conformity to the generally allowed standards ».
Thus, the data-processing audit is a detailed review of the information system of company (Hardware, software, process, controls, etc) by a person specialist, on behalf of the direction or in support with the team of financial audit.
This review includes/understands :
· The diagnosis ;
· Identification of key controls ;
· The test of key controls ;
· The evaluation of controls ;
· Recommendations.
The data-processing mission of audit can take two forms :
· Special mission of data-processing audit ;
· Data-processing mission of audit in support with the financial audit.
The data-processing audit must have rules and principles which frame its application. One to that data processing has a direction only if its finality is defined : checking of the application of the objectives of the direction, examination of the effectiveness or the safety of the system, of the reliability of an application, controls tax, legal, legal expertise, etc
Auditer in a rational way is the fact of clarifying the finalities of the audit, then to deduce from them the means of investigation considered to be necessary and sufficient.
The finality of the audit data-processing, whatever its standard (intern, external, contractual, legal, etc) is always to give an opinion on the information system and especially on the execution of its preset objectives.
Several rules govern the data-processing audit such as :
· The data-processing mission of audit is rather complex. It must be cut out to manage to reconstitute a plan with clear and significant stages.
· When the task of the listener is well defined, it should not overflow about it. The listener must always respect the limits of his mission. For example, if it is requested from a listener to check the safety of an application, and that it of it is satisfied, it is completely indifferent to know if the results are exact, because it is a question of reliability.
· The results of the data-processing audit must be evolutionary (opening of recommendations on the future and not simply acknowledgment of failure), coherent and exact (reliability of the conclusions).
· The safety of the audit applies to the working papers and the reports/ratios, i.e. their not-diffusion with recipients not - authorized.
By complying with these rules, the Listener can affirm to have made a study of the significant elements and to have to identify the zones of existing risks.
The evolution of communication and information technologies confronts the company at the many new risks. In addition to the usual risks met in any mission of audit, the data-processing risks contribute to the increase in the vulnerability of the systems.
Within the framework of the missions of data-processing audit, the listener must take into account the effect of synergy of the two types of risks : Risks of audit and risks data-processing.
In what follows, one will be interested to present the two types of risks :
The listener must resort to his professional judgment and to define procedures of audit aiming at reducing the risk to a low level.
The standards of the IFAC define the risk of audit as being «the risk which the listener expresses an incorrect opinion because of significant errors contained in the financial statements. It is subdivided in three components: the inherent risk, the risk related to control and the risk of not-detection.
· The inherent risk : is the possibility that the balance of an account or that a category of transactions comprises significant errors isolated or cumulated with errors in other balances or categories of transactions, because of insufficiency of internal audit.
· The risk related to control : is the risk that an error significant in a balance of account or a category of transactions, isolated or cumulated with errors in other balances or categories of transactions, nor is not prevented or is detected, and corrected at the appropriate time by the countable systems and of internal audit.
· The risk of not-detection : is the risk that the controls implemented by the listener do not manage to detect an error in a balance of account or a category of transactions which, insulated or cumulated with errors in other balances or categories of transactions, would be significant ».

Figure 1: Risks of audit
The data-processing risk is defined as being «any event which while affecting an information processing system is likely to involve damage and/or losses with the company » 2(*).
To face the evolution of these risks, the countable system envisaged the risk management like a principal component of the process of audit internal.
These risks must undergo actions of analysis and evaluation in order to encircle them and analyze them to be able to found the policy of adequate safety.
The sources of risks are :
· Technical problems : It is of deterioration of the software and the data, of breakdowns or destruction of material, etc
The technical problems find birth of the immense complexity of the information processing systems.
To be able to avoid reflected them direct these problems, the company does not have to limit itself to the specific actions of maintenance. It is necessary to analyze these problems (to formalize the history of the breakdowns) and to envisage effective policies to ensure the continuity of the exploitation.
· Error: The error can appear under various aspects of which the organisational insufficiency, bad protection, negligence, etc
Many faults of safety are created and exploited by the users. The latter are not sensitized with this type of problems.
The error relates to all the dangers to which an organization must face aiming at the safety and the reliability of its processes and its treatments.
· Disasters natural and accidents: They are the fires, the floods, the strikes, the storms, the explosions, the attacks, etc
The company must adopt and set up safety requirements appropriate (smoke detector, gas-detector, air-conditioners, etc) for stage to these risks.
In the event of supervening of accidents, the company must envisage plans of help or continuity of exploitation.
· Ill will and fraud : It is in particular of the basic diversions, the intrusions, the flights, the destruction, etc
The human component is the factor of the most important risk. Indeed, nearly 80% of the attacks are made by the employees of the companies. Being given the vulnerability of the information processing systems, the computerized environment represents the ideal medium for the development of the fraudulent actions.
These actions can be summarized in operations of sabotages, espionages, wastings and of handling of data at nonprofessional ends.
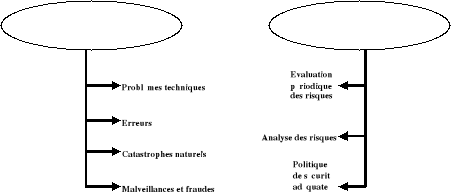
Figure 2 : Data-processing risks
During unfolding of the mission and during the phase of planning and the production run, the listener must accumulate a detailed knowledge of the data-processing environment and carry out an evaluation of the system of internal audit of the processes of the company.
For that, the Listener bases himself on suitable techniques of audit and evaluation.
The listener proceeds by stage. It is interested in the review of documentation of the company, then it organizes talks targeted with the personnel of the company and finally he carries out the tests necessary while basing himself on sampling.
· With regard to documentation, the listener asks the data-processing direction to provide him :
- Internal procedures of controls;
- The directing diagram and data-processing budget : a description of the information policy (current and future) of the company ;
- Flow charts and descriptions of the functions of the personnel (Job descriptions) ;
- Contracts of acquisition of services and computer equipement ;
- Maintenance contracts of the acquired applications ;
- The document laying down the policy of safety company;
- The procedures which define the processes of exploitation of the company.
· The data-processing listener is then interested to organize meetings with the personnel of the company.
He focuses his talks, in the first time, on the data-processing management staff. The listener accumulates the maximum of information on which it will rest for the comprehension of the information system and especially for the identification of the faults and the weaknesses of the system.
The talks are established, after, with the general management staff, other directions until arriving to the simple users of the system.
The listener brings closer the information extracted the documents with those resulting from the discussions with the personnel from the company.
Any information whatever its origin can be useful for the listener during his mission of audit and evaluation.
· The third technique of audit is that of sampling or test. The listener chooses the sample starting from a homogeneous series of data while supposing that the sample is representative of the population. From the study of the characteristics of the sample, a generalization can be made about qualities of the whole population.
The fields to be tested are the seized data, the rejected data, the data-processing treatments and the access security to the system.
For example, to evaluate the access security of the users, the listener must ask for the list of the user profiles and check the respect of the rights of access which theirs is granted.
The team of financial audit definite the nature of the intervention of the data-processing team of audit. The missions of data-processing audit, in support with the financial audit, can take two forms: review of the system checks data-processing or re-examined one or more applications.
Even if they are a mission review of one or several applications, the listener must start his mission by the summary awareness of the general environment of control of the data-processing function of the company.
Main goal of the summary review of the data-processing system checks is to evaluate the adequacy of controls within the data-processing department. This evaluation makes it possible to bring an opinion on the internal level of audit within the information system.
During this mission, the data-processing listener will have to re-examine the segregation of the tasks within the data-processing organization, the operations of exploitation around the environment of the operating system, work of development and maintenance of the applications, the data-processing security management, the management of the safeguards and the plan of continuity of exploitation.
Data-processing controls of applications are controls conceived to prevent or detect the errors and the irregularities being able to have an impact on the financial statements.
Controls of applications are exerted on the level of a cycle or a transaction. They have the aims of controls directly:
. The exhaustiveness of the recordings ;
. The exactitude of the recordings ;
. Validity of the recordings ;
. The access restricted in the active and the recordings.
During this review, the listener concentrates his work on the review of controls of the direction, the accesses, the entries, the rejections and the treatments.
In what follows, one will present the stages of the process of audit of a data-processing application, in support with the financial audit, in an integrated environment.
The process comprises three stages : Planning, Execution and Finalization.
At the time of this phase of the mission, the listener must take note of the data-processing environment of the company.
This awareness is limited to the systems which contribute to the establishment of the Financial statements.
Principal work of the listener at the time of this phase consists with a census of average data processing.
The awareness includes the collection of a specific further information relating to for example the following elements:
· The application or the systems which contribute to the establishment of the financial statements ;
· Computer equipement ;
· Controls of the direction exerted on the data-processing function;
· The complexity of the computerized treatments (volume of the operations, calculations complex, data exchanges, etc) ;
· The architecture of the existing information system;
· The general description of the applications ;
· Significant changes in terms of systems and data-processing environments ;
· Problems former identified to the level of the systems ;
· Data-processing projects in progress and to come.
The phase of collection of information is more important the first year or the year of the change because it helps to fix the strategy of audit (High, Some or No).
On the other hand, the following years, taking into account accumulated knowledge of audit, the process must be faster since the listener is interested only in the changes of the exercise.
At the end of this phase, the listener must normally have a clear idea on the information system of the company. The listener is brought to prepare a cartography of the systems (presentation of the information system : applications, interfaces) and a applicative card (information specific to the applications : names, nature, waiter, place)
Execution
After having taken a sufficient knowledge of the data-processing environment of the company, the data-processing listener passes to the production run.
During this phase, the objective of the listener is to appreciate the internal level of audit of the processes of management of the company and its impact on the certification of the accounts.
The listener aims at evaluating the adequacy and the quality of controls around the data-processing applications in order to ensure itself of the reliability of produced information.
The listener proceeds to the review and analyzes controls of the direction, access controls, entries, data rejected and treatments.
· Controls of the direction :
These controls are applied to the final information produced by the treated data. They are carried out a posteriori by people distinct from those in load of the treatment. Their goal is to detect errors or irregularities likely to occur upstream.
The information processing system offers to the direction several information useful for the piloting of the entity and the supervision of the activity.
Controls of direction can consist of the review and the follow-up of the logs of audit, the detection of the operations and the abnormal balances, etc
The objective of the listener is to make sure that the controls set up by the direction guarantee at the end of the treatments the reliability of produced information.
· The access :
In the organization of any company, one can find several departments. Each department exploits data-processing applications specific to its tasks. For example, the personnel of the sales department must limit itself to the use of the applications of this same service without having access to the applications of the financial service or of production. In practice, one frequently identifies people having access to data-processing applications which are not in relation to their operational tasks.
The listener must ensure himself of the respect of the rights of access granted to the users.
· Entries :
The entries can be defined as being all the data used in the treatments. They are the permanent data (name, first name, code article, price, code customer, bank account number, the wording, etc) and the transactions (Invoices, Purchase orders, etc).
The listener must make sure that the data are introduced and seized in the system in an exact way, exhaustive and single.
· Rejections :
In the companies which have a reliable and optimized information processing system, reports/ratios of rejection must be published regularly. These reports/ratios are re-examined by a person entitled in order to identify the rejected data, to analyze them and finally go up information for its assumption of responsibility by the operational directions having initiated the operation. The listener must check the edition of these reports/ratios and the correction of the errors.
· Treatments :
The listener must evaluate the quality of the controls applied to the treatments. These controls aim at providing a reasonable insurance that the transactions generated by the system are correctly treated by the computer over the good accounting period.
The results of the evaluation of controls of the direction, the entries, the access, the rejections and the treatments form for the data-processing listener the base of appreciation of the internal level of audit of the processes.
After the evaluation of the internal level of audit of the processes, the data-processing listener reports of his work at the team of financial audit. This conclusion will be retained as bases for the choice of an adequate strategy of audit on the level of the countable component concerned with the treatment of the application.
According to the approach of PricewaterhouseCoopers, three strategies of audit are possible :
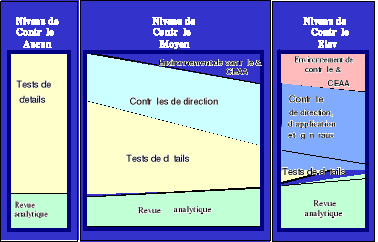
Figure 3 : Strategies of audit
This situation supposes that none controls applied is reliable : Controls of pilotings, data-processing system checks and controls of applications.
If the strategy of audit followed is NO, the financial listener must :
· To be unaware of the tests on key controls (controls of piloting and controls of applications) and on general data-processing controls ;
· To focus its work on the tests of detail like some analytical procedures.
The adoption of this strategy supposes the reliability of controls of piloting.
The financial listener is based on controls of the direction which ensure that there no were major failures. The confidence which the listener grants to these controls is decisive at the time of the determination of extended from the tests of detail.
The step of the listener consists with:
· To document controls of direction ;
· To test key controls of direction (of piloting and application) ;
· To be unaware of the tests on general data-processing controls ;
· To complete work of audit made up essentially of tests of detail as well as analytical procedures.
In this case of key controls (of direction and application) exist, are documented and powerful. The listener carries out tests on these controls to make sure of their effective operation and their permanence.
Thus, this step consists with:
· To document controls of direction, the system checks data-processing and controls of application;
· To test the data-processing system checks ;
· To select and test key controls of direction and application ;
· To carry out analytical reviews.
· The tests of detail are excluded at the time of the choice of this strategy.
The integrated software packages of management became impossible to circumvent for certain Tunisian companies and they monopolize an increasingly significant part of market.
The ERP east defines as being a tool for reorganization of the company. Its goal is to make it possible the companies to more easily achieve their goals, namely to improve to a significant degree their productivity and their competitiveness.
This tool makes it possible a company to make migrate, partly or entirely, its current data-processing applications towards an integrated software package.
In an economic context in perpetual evolution, where the increasing complexity of the information systems and the permanent evolution of technologies accelerate the cycles of life of the company, the great groups must face major data-processing stakes, pledge of their future leadership.
The growth of the environment of businesses of the companies imposes the following requests to them:
· Aggressive initiatives of control of the costs ;
· A need to analyze the ratio costs/reconsidered a base produced or customer ;
· A flexibility to fulfill the requirements changeantes of the businesses ;
· More well informed managerial decision-makings ;
· Changes in the ways of making deals.
However the principal obstacles with the growth of any company are the difficulty in obtaining precise data and information at convenient time. It is thus allowed that the productivity of a company passes by the installation of a coherent information system guaranteeing the unicity of information and the access to this one starting from all the functions of the company.
Certain applications or planning systems were introduced into the business world before the integrated systems of type ERP.
They are the managerial systems of information (Management Systems Information), of the integrated systems of information (Integrated Information Systems), of (Material Resource Planning) or the material manufacturing resource requirements planning resource requirements planning (Manufacturing Resource Planning).
However, more generally, one can say that the Business data processing knew great upheavals since, of monolithic and static in the Sixties, 70 and 80, it became modular and evolutionary today.
The Fifties to 70 often called the thirty glorious ones for their growth rate and the profits of productivity, saw developing methods and industrial management tools. These methods and these tools gave rise to first generations of software packages (accountancy, production control, book-keeping industrial, stock management) which are often at the origin of the ERP of the years 1990.
The Sixties were the time of the «Mainframe». It is a question of treating the data. The business data processing has a role of super calculator which enmagasine of gigantic volumes of data, sorts them, the draft and restores them in more condensed form and more understandable. The only role of the user in this diagram is to collect the data and to make them seize.
The Eighties were the period of the «Minis» with the access to the data. Each department or division of the company can have an autonomous processing capability. The minicomputers in the companies make it possible to have applications which meet the needs in a more specific way. A greater number of users can then reach the data.
In the Nineties, the customer-server one makes its appearance, making it possible to share information. The micro-computers in the company make it possible the personal computing to exist, creating of this fact three levels: company, department, individual. The architecture of the information system is at this horizontal period, which makes it possible to integrate and federate the whole of the existing components. To share information becomes a need. The user of this diagram is in the middle of the information system and data processing is with the service of the strategy of the company and not the reverse.

Figure 4 : Customer-server architecture
Years 2000 are remembered by the integration of the components. Indeed, the basic applications which are installed in the various departments do not make it possible their users to share a common language. If the interfaces between these various fields of the company were installation, they are seldom in real time, and one can easily attend examples of double or seized triple of the same data.
These situations are unacceptable. The induced costs are priceless : waste of time, misses effectiveness, bad visibility, bad decision-making process, duplication of effort, error rate raised, etc
All these dysfunctions have a bad influence on the customer service and a loss of competitiveness of the company. Therefore, one felt the need for a total data processing integrating all the components which will make the success of the company : for this reason the Integrated Software packages of Management begin.
Today, one sees the appearance of the integrated software packages. They make it possible data processing to evolve to a division of information, a more close integration and more flexibility.

Figure 5: Evolution of the information systems of company
The ERP which can be translated by «Resource requirements planning of L 'Undertaken » is theoretically art to manage, in an optimized way, the means and resources available to a company thanks to an integrated software package of management.
The term of Software package is a neologism creates in 1962 by J.E.Forges, starting from the produced words and software.
Several authors covered the subject such as Casino which according to him the ERP «Is an integrated software whose various modules make it possible to treat the whole of functions (finance, production, sales, accountancy, human resources, etc) of the company » like Jean-Louis Lequeux, in his work «Manager ERP », which defines ERP as «A subset of the information system in charge of the integral management of the company ».
The ERP is an integrated software package constituted of functional modules and opened tools of modeling, structured around a system of relational data bases ensuring a single, coherent, made safe and opened management data of the company while allowing the modeling of the whole of the processes of the company, which they are operational or process of support.
These modules cover :
· Production control ;
· The management of the purchases and stocks ;
· Administration of the sales;
· Countable and financial management ;
· The control of management.
It is a software package skeletal allowing to reconcile standardization and adaptation to the company. It is opposed to the software owner developed for the specific needs for the company. It is a solution of international size able to manage in a way integrated of the contexts of multi-legislations and multi-languages.
Management in mode ERP aims to manage and plan the whole of flows and the functions of a company, including logistic flows. The field of application extends from the chain supplier to the final customers. One can thus speak about WIDE COMPANY.
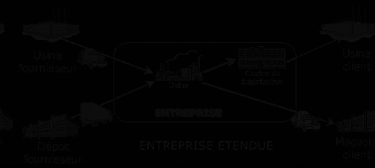
Figure 6 : The wide company
On the market of the ERP, one finds several editors of software package, but most known whose SAP, JDEdwards, Oracle, Peoplesoft control more than 65% of the market. The graph below presents as an indication the Share of market of the editors of ERP in France during the year 2002.
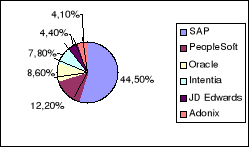
Figure 7 : Actors of the market (source CAP)
During a press conference held in New York on September 5, 2003, Craig Conway, president of the executive committee of Peoplesoft, announces fusion between J.D. Edwards and Peoplesoft. The product carrying mark J.D. Edwards is not marketed any more.
Each company has various reasons to establish a software package of management integrated in its organization. However, these reasons can be indexed according to two large axes: external constraints and internal stresses.
The external constraints are simple releases of the establishment and not of the reasons related to the specific activities of the company. The principal external constraints are the passage to the year 2000, the passage to the Euro and the globalisation.
Figure 8 : Reasons of establishment of a ERP
These three reasons involve, indeed, an important cost of adaptation of the existing data-processing software in the companies. These last benefit from this occasion to establish a more complex information system.
The technological projection and competition also represent external constraints for the companies, since they imply that the company must be held up to date last evolutions in the data-processing field so that its information system is not exceeded.
The internal stresses involve as for them a need for tools which imply a great flexibility of evolution, a hyper reactivity with the change and a capacity of almost unbounded adaptation, and this at a tiny cost.
The two great types of internal stresses of an organization are on the one hand the strategic changes of the company and on the other hand competitiveness and the productivity.
The strategic changes of an organization get along on several levels :
· The international level : the company aims at a management by process and activities and either by functions and costs. The company must moreover gain in speed and flexibility. The solution of the integrated software package makes it possible to the leaders to have a homogeneous vision of all their operations throughout the world.
· The level of the reorganization and the reorganization of the company : the information systems must be an engine in the permanent structural changes which the company knows. The integrated software packages of management make it possible to harmonize the way of working of the various sites of the company.
· The level cost: The integrated software packages of management are often more economic than the internal developments. It is one of the imperative reasons of their strong current growth.
The second type of internal stress relates to the competitiveness and the productivity of the company.
The competitiveness of a company lies in its capacity to revise, reinvent and automate the whole of its processes and in its capacity to reduce its cycles. The key words are thus quality, flexibility, speed, cost, service, traceability and reactivity. The result is immediately a better customer service.
The companies thus need flexible, evolutionary data-processing solutions to meet the needs changing for the market but also for a complete integration of the functions of management to react to the market.
However, various problems exist. For example, traditional data processing is unable to answer in an adequate way the requirement of growth imposed by the market.
The solution is thus to create processes which cross the activities of the company and which this one adopts a horizontal structure.
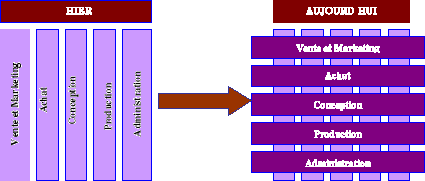
Figure 9 : Evolution of the structure of activity of the company
The integrated software packages of management take into account the new needs for the companies, i.e. their request of more than information, more division, more integration and more flexibility.
The installation of the integrated solution will certainly have reflected positive on the level technological, strategic, productive and competitive of the company.
On the level of technology, the integrated software package proposes a solution achieved with methodology, the tools and technologies of tomorrow: it represents the best hope in front of the need for new data-processing solutions more opened, more integrated and more standardized.
On the strategic level, the integrated software package has a side structuring with respect to the company: it makes it possible to federate and homogenize the large variety of the processes and disparities of the company like the data-processing networks, the software and the tools, computer equipement, the management tools, measurement and analysis. It can also harmonize the way of working of the various sites of the company.
Synergy between the various actors created by the project of establishment of an integrated software package results in a better organization of work.
Thanks to the integrated software package, the company can benefit from the experiment of the others, rather than to begin again of zero and to recreate its company.
The integrated software packages propose processes for the various activities without imposing them.
The integrated software packages contribute today to a less progression of the data-processing budgets: the return on investment (KING) is very fast.
The integrated software packages facilitate maintenance and reduce the costs of the developments.
To face the keen competition, the ERP can be regarded as a key factor of competitiveness. It presents a global vision of the activity in real time and ensures :
· The implementation of the concept of - just in time;
· The optimization of the costs of all the blocks of management ;
· The reduction of the duration of the processes ;
· Increase in the quality of the products ;
· Improvement of work and collaboration in team ;
· The levelling with the state of the market ;
· Fast evolution towards new functionalities to allow a better reactivity compared to the request for the market.
The very strong human implication that the establishment of an integrated software package requires translates by a strong adaptation of the users to their new solution.
As in any system, one notes defects with the ERP, which come paradoxically from their qualities.
These integrated software packages of management cover practically the whole of the processes. They take difficult and a long time to put in work and by definition are very integrated and thus relatively rigid and delicate to modify. Their installation requires the conjugation of technical skills and functional. The company must set up pre-necessary them (definition of the work-flow, rules of management, etc) necessary to their durable and successful implementation.
The ERP is by very rich definition, it is a consumer in data-processing power (waiters, networks, etc).
It does not include all the rules and principles of management what obliges the purchaser has to adapt the company to the product and especially to make the dead end on a certain number of functionalities.
A ERP includes/understands today tens of modules applicatifs which can be gathered in three categories : sectoral modules, intersector modules and wide modules :
· The sectoral modules back the trades activities of the company (production, maintenance...). They are specific to the sphere of activity of company (car Manufacturer, Assurance, oil service, etc);
· The intersector modules computerize the activities of support of the company. They are subdivided in three categories : activities of support (accountancy, Human management Resources...), the system direction (strategic and operational planning) and the gate of company towards outside (access via Web to information of the company) ;
· The wide modules manage the transactions between firms or between a company and its customers such as the modules of the type SCM, CRM...
The standard model of the ERP always includes the following activities of the company :
· Production planning ;
· Management of the purchases and stocks ;
· Administration of the sales ;
· Human stock management ;
· Logistics ;
· Countable and financial management.

Figure 10 : Modules of a ERP
These modules, are completely or partially interfaced what will generate the creation of important flows of information. These flows are schematized as follows :

Figure 11 : Flows of information covered by a ERP
Comments :
The diagram, above, illustrates flows of information generated starting from the integration which exists between the modules of a ERP (management of the purchases, management of the sales, accounts payable, accounts receivable, general ledger, immobilization, stock) and the permanent data of the company (information customers, suppliers and articles).
The module general ledger is integrated with the other modules. It automatically receives information of the module purchase (engagements), of the accounts receivable (invoices and payments) and from the accounts payable.
The modules of the integrated software package use instantaneously information (customers, suppliers, rate of exchange...) starting from the permanent data bases (Master Dated).
Before starting the mission, the listener must set a clear purpose in order to be able to follow the most effective step which will make it possible to achieve the preset goals.
In the case of a mission of audit of an integrated software package, the principal objective is to evaluate the relevance of existing controls on the level of the various modules to ensure itself of the quality of the information produced by the software package.

Disponibilité
Intégrité
Confidentialité
Auditeur


Figure 12: Objectives of audit of a ERP
To guarantee this insurance, the specialists must deliver their opinions on:
· The Availability:
It is the aptitude of the systems to fulfill a function within preset conditions of schedules, time and performances. It is a question of guaranteeing the continuity of the service, of ensuring the objectives of performance (response time) and of respecting the dates and limiting hours of the treatments.
To ensure itself of the availability of information, of the suitable procedures of cover against the incidents as of controls of safety must exist in order to protect itself from the inattentive or intentional suppressions from the files.
The availability of flows of information is the fact of guaranteeing the continuity of the exchanges of information, i.e. of being able to have, each time the need exists, the possibilities of reception or transfer.
For the treatments, the availability is intended to guarantee the continuity of service of the treatments, i.e. to be able to have the software and hardware resources necessary to the whole of the services, the agencies and with the external customers.
The availability of the data is the fact of being able to have the access to the data each time the need exists.
· Integrity:
It is the quality which ensures that information is identical in two points, in time as in space.
According to ISO'S 13-335-1, the integrity it is the property of not-deterioration or nondestruction of whole or part of the information system and/or the data in a way not - authorized. It is a question of guaranteeing exhaustiveness, the exactitude and the validity of information like avoiding the modification of information.
The Integrity of the data consists in establishing controls on the entries and the treatments of the transactions. It consists in, also, making safe the files of the cumulated data of any modification not - authorized.
The Integrity of the operations and the electronic documents is likely to be blamed. This deterioration of the Integrity can cause for the company of the litigations with its customers about the conditions of transaction and payment.
The Integrity of flows of information is intended to guarantee the reliability and the exhaustiveness of the exchanges of information. I.e. to make so that the data are received as they were emitted and to have the means of checking it.
For the treatments, it is intended to ensure the exactitude and the conformity of the algorithm of the treatments automated or not compared to the specifications. I.e. to be able to obtain complete and reliable results.
The Integrity of the data is intended to guarantee the exactitude and the exhaustiveness of the data with respect to errors of handling or uses not - authorized. I.e. to be able to have data of which exactitude, freshness and exhaustiveness are recognized and attested.
· Confidentiality:
It is the quality which ensures the secret behavior of information with access to the only authorized entities. The protection of the confidentiality of information against any intrusion not - authorized is of an important requirement which requires a minimum level of safety measures.
It is about:
- to only reserve the access to the data of a system to the users entitled (authentification) according to the classification of the data and the level of enabling of each one of them ;
- to guarantee the secrecy of the data exchanged by two correspondents in the form of message or of files.
This last shutter constitutes the most significant point in the electronic exchanges and interests as well the company as the consumers. Indeed, the latter worry for protection about their personal and financial data by fear which this information is revealed or used in order to harm their interests. It is thus normal that the people who plan to have recourse to the electronic trade seek to obtain the insurance that the company set up effective controls on the protection of information and that it takes care of the confidentiality of the personal information of its customers.
The confidentiality of flows of information is intended to guarantee the protection of the exchanges of which the disclosure or the access by thirds not - authorized damage would carry.
For the treatments, it is intended to ensure the protection of the algorithms describing the rules of management and the results of which the disclosure with thirds not - authorized would be harmful.
The data confidentiality is intended to protect the data of which the access or the use by thirds not - authorized damage would carry. It is a question of giving the access that to the competent people all while being based on formal procedures.
Throughout part A, our work limited themselves to a theoretical exposure of the data-processing audit. In the same part, one tried to present the concept of ERP and to define the objectives of audit of an integrated software package of management.
In order to clarify these concepts as well as possible, the part B will present the course of a mission of review of the module «Accounts receivable» of software package J.D. Edwards in an oil company in support at the financial audit. This review consists in testing data-processing controls which apply to the permanent data of the company and with the level of the module «accounts receivable».
PART B : DATA-PROCESSING MISSION OF AUDIT IN SUPPORT WITH THE FINANCIAL AUDIT (CASE OF AN OIL COMPANY)
As the expression indicates it, it is initially a system, i.e., a whole of components which constantly have interactions between them with an aim of achieving the same precise objective and solicitor.
It is then a system based on information, i.e. the communication or the use of the data in order to make this information useful for the final recipients.
An information system of management is a man-machine system integrated with an aim of making available information necessary to management from the operations just as for the analysis and the decision-making in the company.
It is a whole of data which makes it possible to describe, to explain, predict and act on the phenomena according to the degree of formalization and aims in view's.
The information system supports the development of a common language between the members of the same discipline or speakers of various professions in order to support the exchanges and to come to a complementarity of the objectives and steps which will be continued.
So that one can say that a company has a good information system, it is necessary necessarily that all the information which is at its disposal is structured in order to be easily accessible to all the interested parties so that they can improve the effectiveness of management in the company. This structuring can take several forms while preserving the same objective: to improve the effectiveness of the whole of the company.
During the preliminary phase of comprehension of the information system of the company, the listener is brought to schematize the structure of this system in the form of cartography.
This cartography allows :
· To determine the relation between the financial statements and the systems which generate them ;
· To identify the data-processing environments and applications to approach during the general review of the data-processing system checks ;
· To determine which functions and which information processing systems must be re-examined for each cycle (returned and clients' accounts, purchases and accounts suppliers, stocks, fixed assets, pay, treasury).
This work, generally, is undertaken in a joint way between the financial listener and the data-processing listener.
The collection of information is done while discussing with the operational persons in charge, the financial persons in charge and the data-processing persons in charge like by examining existing documentation.
The cartography makes it possible to identify the principal cycles from which the data result mainly from the data-processing treatments, the principal activities within each cycle, the control of these activities, the subjacent systems of each activity within the cycles, the data-processing environments on which the systems function and other systems to be taken into account in the planning of the audit.
It is generally appeared as a diagram or a table (less complex system).
The following diagram is a presentation of the cartography of the information system of the studied company:

Figure 13 : The cartography of the systems of the studied company
According to the cartography above, the food of the general ledger by the data relating to the operations of invoicing, of management of the fixed assets, management of the distribution, management of and the management gas coupons of the pay of the personnel is done in an automated way.
Indeed, the countable applications of the sales and management of the pay of the personnel all were developed on the same platform (filing system under ACE/4003(*)). The acquisition data, previously mentioned, is done on the level of the modules of J.D. Edwards4(*) (accounts receivable, accounts payable, management of the fixed assets) and of the business application of the pay of the personnel.
They, thereafter, will be automatically charged in the general ledger to the level of the module of the general ledger of J.D. Edwards. The business application of the gas coupons is interfaced with J.D. Edwards.
The information processing system of the studied company comprises also other applications which were developed by the head office for technical needs.
For a better comprehension of the information processing system of the audited company, the listeners specialists must describe the various data-processing applications, is this, by specifying the information illustrated in the following table :
|
Nature |
Waiter |
Operating system |
Direction user |
|
Modules :
|
|
|
|
|
Transport Notes5 Lotus(*) |
Windows NT |
Windows NT |
All directions |
|
Management of the pay |
AS/400 |
Windows NT |
Direction Human Resources |
|
Management of the gas coupons |
SQL |
Windows NT |
Agencies |
|
Management of the deposits |
Windows NT |
Windows NT |
Agencies |
|
Management of the mixtures of oils |
Windows NT |
Windows NT |
Agencies |
|
Management of the careers |
Windows NT |
Windows NT |
Human direction Resources |
|
Management of the sales |
AS/400 |
Windows NT |
All directions |
|
Application of laboratory |
Windows 95 |
Laboratory |
Figure 14 : The applicative card of the studied company
· Reviews of the modules of J.D. Edwards :
Throughout this phase, the data-processing team of audit is brought to re-examine the parameters of each module of J.D. Edwards. The listeners evaluate the relevance of controls around the modules of J.D. Edwards exerted on :
- Procedures concerning the permanent data (see the 2.3.3 documents to be consulted);
- Accesses : to check that the people who reach the system respect the rights which are granted to them ;
- Seizures, treatments and rejections;
- Reports/ratios of standard controls of J.D. Edwards: to publish, re-examine and analyze these reports/ratios ;
- The process of accounting : to check the relevance of the controls applied to these processes ;
- Instructions of automatic accounting (see the 2.3.3 documents to be consulted) ;
- Reports/ratios of integrity (see the 2.3.3 documents to be consulted);
- Etc
· The information system security :
For the review of the safety of J.D. Edwards, the data-processing team of audit must :
- To re-examine and check the data-processing organization of the company : the separation of the tasks, accesses, the policy and procedures of safety ;
- To check and re-examine the safety and the network architecture ;
- To validate the existence of a plan of continuity of exploitation
- To re-examine the safety measures applied to the orders of fast access (Fast Path) and to the shortcut keys (Function Key) ;
For the advance of her work in the company, the data-processing team of audit employs several techniques : talks, tests and the review of documentation.
During the phase of tests and talks, the listener must proceed to the documentation of his work.
With this intention, it is based on a standard support developed by the PwC firm which presents key controls of J.D. Edwards to be tested. This support represents the best practices of the PwC firm « Best Practices » and all its experiment in the field of the review of JDEdwards gathers.
It constitutes the base of documentation for the listeners, one speaks about «the Matrix of controls ».
This matrix is appeared as an Excel file.
It is a question of testing a whole of controls set up by the company to cover the potential data-processing risks.
These controls are classified according to the following modules and topics' :
· The data security and control of the access « J.D. Edwards Security »;
· Permanent data «Master Dated »;
· The accounts receivable «Accounts Receivables »;
· The accounts payable «Accounts payable »;
· Fixed assets «Fixed Assets »;
· Stock «Energy Chimical Solution »;
· General ledger «General Ledger »;
· Reports/ratios of integrity «Integrity carryforwards ».
This matrix makes it possible to describe controls, to list the tests to carry out for the evaluation of the aforesaid controls and to document the results of the tests carried out.
The results of the tests will be synthesized according to a system of scoring which makes it possible to inform about the degree of confidence to grant to the data-processing environment of the company.
In what follows, we will quote principal controls as well as the tests referring module by module to it.
The permanent data correspond to the source data of the information system whose frequency of modification is relatively weak. Each data must be single in the data base.
The principal permanent data are :
· Source data relating to the customers : corporate name, addresses, people to be contacted, credit limit, handing-over, etc...
· Source data relating to the suppliers : corporate name, addresses, people to be contacted, bank account number, etc...
· Source data relating to the products : designation, reference, composition, price, VAT, etc...
· Source data relating to the fixed assets : designation, reference, rate of depreciation, etc...
· Source data relating to accountancy : plan of the accounts, automatic instructions of accounting, rate of exchanges, etc...
· Source data relating to the production : basic articles, tanks, vehicles, deposits, subsidiary companies, factories, etc...
For each group of data (Suppliers, Customers, Fixed assets, Banks, rate of exchange, etc...), only one owner must be designated. This owner is responsible for the follow-up of the authorizations of modification brought to the permanent data and also of the review of these modifications.
Taking into account the sensitivity and importance of the permanent data, computerized key controls should be set up in order to make sure that their updates (creation, modification, suppression) were made in a manner correct and authorized and that these updates are controlled a posteriori through the edition of the logs of audit.
The computerized key controls applied to the permanent data are generally represented, in practice, by procedures of update and maintenance of the permanent data that the data-processing listener will be brought to test their level of application.
Procedure of update and maintenance of the permanent data allows to define :
· Identity of the people entitled to update the permanent data ;
· The nature of the documents authorizing the update of the permanent data ;
· Identity of the people entitled to re-examine and validate these updates.
In order to ensure itself of the level of permanent data security of the company, the listener must test the level of application of the procedures.
The table hereafter presents controls which must exist on the level of the permanent data and the tests referring itself to it :
|
Key controls |
General tests |
|
|
|
|
The data-processing listener must test controls computerized to make sure of their existence and especially of their good application. The identified exceptions will be described in the internal report/ratio of audit.
|
Key controls |
Tests |
|
Rules of management :
|
|
|
Code blocage6(*) clients' accounts :
|
|
|
Credit limit customers :
|
|
|
Goings beyond of appropriations customers :
|
|
|
Interfaces 7des(*) applications with the module «accounts receivable» :
|
(edition, sale, repurchase of the goods). (CF Annexes) |
|
Customer orders :
|
|
|
|
|
Notes of flow /credit :
|
|
|
Sale books :
|
|
|
Cashings :
|
|
|
Unpaid:
|
|
|
|
|
Provisions and adjustments:
|
|
|
Manual invoices:
|
|
|
Reports/ratios of integrity:
|
|
As one evoked on the level of the introduction, the principal purpose of the review of the controls automated on the level of J.D. Edwards is to provide to Management a reasonable insurance as for the integrity and the reliability of the data processing.
To reach and confirm this insurance, the data-processing team of audit must focus part of her work on the review of the controls applied to the level of the organization, the environments, the menus and the procedures in order to guarantee the safety of J.D. Edwards.
Controls are summarized at the following points :
|
Key controls |
Tests |
|
Segregation of the tasks:
|
|
|
Data-processing environments:
|
|
|
Systèmes9 orders(*):
|
|
|
Fast access (Fast Path): Description: J.D. Edwards allows the fast access to its modules and standard reports/ratios by using specific orders (exp. : the execution of the order «G09» allows the fast access to the general ledger G/L).
|
|
|
Shortcut keys (Function Key): Description: J.D. Edwards gives access quickly the resources of the system by using combinations of keys of the keyboard.
|
|
|
Opening and closing of the accounting periods:
|
|
|
User profile:
|
|
|
Creation of user profiles:
|
|
|
Rights of access:
|
|
During the mission, the listener must have at his disposal several documents which are used to him as a basis for its work of controls. These documents are is reports/ratios generated starting from the system or many procedures specific to the company.
In what follows, the documents will be presented important that the data-processing listener must consult within the framework of his work of review of a ERP.
· LOGS of audit or Auditrons:
Are newspapers published by the system by the execution of specific orders. These newspapers recall all the operations of change (creations, modifications, suppressions) made on the level of the permanent files such as the file suppliers « to beg file », file customers « customer file », management of the thirds « Address Book », the program of adjustment and price « Price and Adjustment Schedule ».
In these reports/ratios, one finds the name of the person who carries out the requests for change, the name of the person who controls the regularity of these changes, the date of modification, the old value and the new value.
· The check procedures of will auditrons :
The Logs of audit must be controlled to identify the actions not - authorized and to avoid them in the future. So that control is beneficial, it must obey a formalized and well defined procedure.
This document indicates the goal of the check procedure of will auditrons, the intervening people, the periodicity of edition, the responsibilities, the methods practical and the applications.
· Reports/ratios of integrities :
The reports/ratios of integrity present the problems of integration which can exist between the balances of the accounts of the various modules of J.D. Edwards « WITH/R, With/P, F/A, etc » and their direct charge on the level of the general ledger « G/L ».
These reports/ratios are an integral part of system J.D. Edwards.
They must be published :
· During the installation of J.D. Edwards and following the migration of the data.
· Daily, for the majority of these reports/ratios.
If these reports/ratios are not published regularly, the integrity of given can be affected, which represents a great risk : « High Risk off Dated Integrity Issues ».
The examination of the reports/ratios of integrities helps with :
· To make sure that the system functions correctly ;
· To correct any problem in time in an efficient way.
It is extremely important of :
· To parameterize the reports/ratios of integrities ;
· To publish these reports/ratios periodically and to try to solve the differences ;
· D-to establish the reports/ratios of integrities until they do not contain any more differences.
The reports/ratios of integrities which one can extract from J.D. Edwards are as follows:
ü Accounts payable : WITH/P
· The P047001 report/ratio compares the pays of the accounts payable in the module accounts payable with the balances of the accounts suppliers charged in the general ledger.
· The P04701 report/ratio checks that the total amount of each batch in the accounts payable is equal to the corresponding amounts in the general ledger.
ü Accounts receivable: WITH/R
· The P03702 report/ratio compares each batch of the gross values receipts registers with the accounts receivable with the table customers of the general ledger.
· The P03701 report/ratio checks that each Batch of the accounts receivable, which corresponds to him the total of the received amounts, is balanced with the corresponding Batches in the general ledger.
ü Fixed assets: F/A
· The P127011 report/ratio compares the balances recorded with the table accountancy fixed assets with the pays of the table of the General ledger.
· The P12301 report/ratio identifies all the transactions which were registered in the General ledger and should be, but it, are not registered yet in the accountancy of the fixed assets.
ü General ledger : G/L
· The P007011 report/ratio presents the schedule of the lots not yet entered while being based on the control panel of the batches.
· The P007031 report/ratio lists the batches which affected but are not balanced. The difference appears in the report/ratio.
· The P097001 report/ratio presents the clear balance of each company.
· The P09705 report/ratio shows the divergence of each period between the pays of the balance and the balances in the general ledger.
· The P097021 report/ratio shows the divergences of the amounts on the level of the companies between the accountancy and the tables of the accounts.
ü Stocks: ESC
· The P41543 report/ratio shows the types of divergences between the tables of accountancy of stocks and those of the general ledger:
- The detail of the article in stock exists without having a correspondence with the general ledger.
- The article is not balanced with its correspondent of the general ledger.
· The P41544 report/ratio shows the divergences for the quantities and the amounts between the accountancy of stocks and the general ledger.
Below an example of report/ratio of integrity :
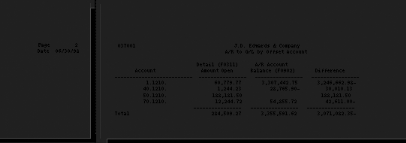
Figure15 : Report/ratio of integrity
· Rights of access :
Are cards formalized which define the rights of access of the users to the various menus of the system, while respecting the profile of each one.
In order to avoid any confusion in the attribution of the rights of access, each request for creation, modification and suppression of user profile should specify :
· The group to which the new user must belong ;
· Additional rights to grant.
Rights of access « Action Codes Security » by programme of each user group must be formally defined. A functional description of each program elaborate and is presented at the person in charge user concerned.
· ACTION codes carryforward :
It is a report/ratio published for each file belonging to the permanent files «Master files ».
This document presents the identities of the user groups « To use Id » which has the right to modify, to create, remove data on the level of the permanent files.
For each group, the report/ratio presents the user profile assigned as well as the allotted safety measures.
· Rules of management «Order Acivity Rules» :
These documents present the logical sequence of the process of activities of a company using J.D. Edwards. Are the rules of management of the company.
The treatments are codified in an automatic way. It is necessarily necessary to pass from one stage at the stage which succeeds it. Each passage of a stage to another must be authorized by a designated person.
Diagram Ci below presents the sequence of the actions of a
process of sale : 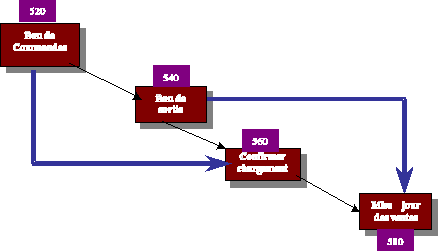
Figure 16: Key phases of a process of activity: Cycle Ventes
With the exit of the review of existing controls on the level of module A/R of the software package of management integrated J.D. Edwards (the review of the level of existence and application of these controls), the data-processing listener raises the points which, according to its own judgment, can assign the level of control to the level of the processes of the company.
The listener indicates, then, his reports, the associated risks as well as the recommendations referring itself to it.
The data-processing listener prepares the final report/ratio of his intervention (this report/ratio is added to the report/ratio of financial audit), in which he formulates the conclusion of his work (recommendations, description, etc).
The team of financial audit will use this report/ratio as bases for the choice of the strategy of audit (High, Some, No) adequate to adopt.
Following liberalization of the markets and vis-a-vis the increased threat of competition, the companies are with the research of the most developed means which their would make it possible to improve their competitiveness and to achieve their goals with knowing creation of value. New information technologies, and in particular the ERP, constituted, during the two last decades, one of these principal means of development. Indeed, majority of the companies, as well the small ones and medium-sized companies that the large international firms, are currently based on information systems built around the ERP.
In this new landscape which characterizes the majority of the companies, the listeners are vis-a-vis systems presenting of information increasingly available, just and protected. However, these systems are, sometimes so complex, that their exploitation requires a particular expertise. Thus, the control of the risks inherent in this system exceeds competences of an only using listener, methodologies and the traditional tools, and requires the implication of data-processing listeners.
It is not with a change of trade, but with an evolution of the methods and working tools which the listener must prepare. The listeners who will confine themselves with accountancy will be gradually plastered with a secondary role and are likely to see restricting their interventions with some operations of high technicality like the decree of the financial statements, or the preparation of the tax or social declarations specific.
The listeners should, consequently, level themselves and this, by the development of their knowledge and competences in order to be able to play a major part in all these new fields, and to revalue even more their contributions for the companies.
Among the tools and methodologies which a financial listener would gain to control and adopt at the time of his missions, it is advisable to quote reference frame COBIT.
This reference frame, developed and maintained by the ISACA treats in particular the fields of the strategy and the data-processing organization, the acquisition and the implementation of the information processing systems, the exploitation and the maintenance of the information processing systems and of the control and follow-up of the data-processing function.
Description of the procedure of management of the gas coupons:
The management application of the gas coupons allows the edition of the tickets fuels, the repurchase of these tickets and the follow-up of stock tickets. The tickets contain expiration dates, the amount, the name of the company, a sequence number and a bar code.
The customer orders are recorded on a standard document. Arrived at the deposit, the purchase orders are re-examined by a person in charge who controls the state of credit of the customer directly on the system before seizing the order on the application cross.
Then, the coupons are on the spot printed by another person (a state of follow-up of the numerical sequences of the tickets periodically is re-examined, signed and delivered to the customers).
Following the delivery of fuel at the stations, the managers can pay the company with coupons.
A state of these coupons (BRB: Good of Repurchase of the Goods) is addressed to the deposit.
The repurchased coupons will be seized in the application using the reader bar code. The keyboarder checks the conformity of the number and the amount of the goods with the BRB. Following the seizure of the coupons, notes of credit in the name of the managers are published. The original one of this note of credit is addressed to the person in charge customers on the level for the seat. A copy will be classified in the deposit.
At the end of the day, the person in charge for this application treats all the goods published (invoices customers) and repurchased (notes of credit customers) on the application and carries out the extraction of the batches to send them to accountancy J.D. Edwards. A daily state of control is published to control the exactitude of the transactions between the application and J.D. Edwards (amounts and a number of transactions). A monthly state of reconciliation of the account «Goods To be delivered» is published, analyzed and approved.
Description of the procedure of blocking of the orders:
According to the procedure of the studied company, when the order is blocked by the system, the keyboarder of the orders prepares a request for releasing which will be addressed to the «credit to control». This last, after discussion with the sales department, can either sign the request for releasing and force the system or to refuse the order.
A state of the customer orders blocked is published daily.
Description procedure of use of the notes of flow/credit:
In the case of our studied company, the notes of flow customers are used for the amounts of the insurances service stations (end of the year), clothing for the stations and the rents. These notes are approved by the «credit to control» before being seized in the system. The notes of credit are used for the coupons (payment of the managers).
Description procedure of use of the manual invoices:
In the case of the studied company, the manual invoices are used in the event of breakdown in the system. A numerical sequence of these invoices is adopted. With the resumption of the system, the invoices are seized on the level of this last and each manual invoice is fastened with the published invoice of J.D. Edwards.
· BRIAN JENKINS and ANTHONY PINKNEY ; Audit of the systems and the accounts managed on data processing, Edition PUBLI-UNION, 1996.
· HOWARD F.STETTLER ; To that : principles and general methods, Edition PUBLI-UNION, 1998.
· SMALL GERALD, DANIEL JOLLY and JOCELYN MICHEL ; Guide for the financial audit of the computerized companies, Edition CLET, 1985.
· JOCELYN MICHEL ; Guide for the operational audit of the data processing and the information systems, Edition CLET, 1989.
· JOSE PLANS; Practice of the data-processing audit, Edition EYROLLES, 1984.
· MARC THORIN ; The data-processing audit, Edition PUBLI-UNION, 2000.
· ABDERRAOUF YAICH ; The countable profession and new communication and information technologies, the Countable review and Financial RCF, N° 53, p. 17.
· THOMAS DAVENPORT and NITIN NOHRIA ; Restick work instead of dividing it ! , the expansion Review Management, Fall 1994, pp. 56-66.
Webography :
· HTTP: // www.sécurité-informatique.enligne-france COM
· HTTP: // www.audit-informatique.fr
· HTTP: // www.procomptable.com
· HTTP: // www.clusif.asso.fr
· HTTP: // www.afai.asso.fr
· HTTP: // www.audit.com
· HTTP: // www.itaudit.org
· HTTP: // www.isaca.org
· HTTP: // www.erp.com
· HTTP: // www.issa.org
· HTTP: // www.jde.fr
- AAI : Automatics Accounting Instructions
- AP : Accounts Payable
- AR : Accounts Receivables
- LOW : Business Advisory Services
- BPR : Business Reengineering Process
- CIF : The Council To that the Formation
- CEAA : Knowledge and Accumulated Experience of Audit
- CF : Corporate Finances
- COBIT : Control Objectify for Information and related Technologies
- CRM : Customer Relationship Management
- ECS : Energy Chimical System
- ERP : Enterprise Resource Planning
- F : Fixed Assets
- GL : General Leadger
- CAM : Production control Computer-assisted
- GRMS : Total Risk Management Solutions
- IFAC : International Financial To that Committee
- ISACA : Systems information To that the and Control Association
- ISO : International Organization for Standardization
- MANDELEVIUM : Master Dated
- MTBF: Mabkhout Tmar Belaifa Fendri
- NTIC : New Communication and Information Technologies
- OSRM : Operational System Risk Management
- CAP: Pierre Audouin Consultants
- PGI : Software package of Management Integrated
- PwC : PricewaterhouseCoopers
- KING : Return One Investment
- SCM : Supply Chain Management
- SODA : Segregation Off Duties Assessment
- TLS: Legal Tax Services
Figure 1 : Risks of audit
Figure 2 : Data-processing risks
Figure 3 : Strategies of audit
Figure 4 : Customer-server architecture
Figure 5: Evolution of the information systems of company
Figure 6 : The wide company
Figure 7 : Actors of the market
Figure 8 : Reasons of establishment of a ERP
Figure 9 : Evolution of the structure of activity of the company
Figure 10 : Modules of a ERP
Figure 11 : Flows of information covered by a ERP
Figure 12: Objectives of audit of a ERP
Figure 13 : The cartography of the systems of the studied company
Figure 14 : The applicative card of the studied company
Figure 15 : Report/ratio of integrity
Figure 16: Key phases of a process of activity: Cycle Ventes
* 1 Abderraouf YAICH, « The countable profession and new communication and information technologies », The Countable review and Financial RCF, N° 53, Third quarter 2001, Page 17.
* 2 www.sécurité-informatique.enligne-france COM
* 3 AS/400 : « Advanced System/400 » is an architecture made up of hardware and software elements, in particular comprising a data base and advanced safety members. The operating system of AS/400 is called OS/400 «Operational System/400 » (Produced IBM).
* 4 J.D. Edwards : Just software package of Management created in Denver in 1977. The PeopelSoft company acquired J.D. Edwards during the year 2003.
* 5 Lotuses Notes : Internal software of transport «Intranet » (Produced IBM)
* 6 the code blocking: During the creation of a clients' account in the company, a code is fixed to make it possible to block this account following the going beyond of the authorized credit limit. This code must be updated.
* 7 Interface : Are connections between the modules of J.D. Edwards and the other applications of the system (example : application Pays)
* 8 SODA : Tool developed by PricewaterhouseCoopers to check the respect of the separation of the incompatible tasks in the company.
* 9 Orders Systems : are requests launched by administrator J.D. Edwards (the first person in charge for system J.D. Edwards) to extract from the source data of the system.