
Publier un mémoire
Consulter les autres mémoires

|
Publier un mémoire Consulter les autres mémoires |
|
|
The team of financial audit definite the nature of the intervention of the data-processing team of audit. The missions of data-processing audit, in support with the financial audit, can take two forms: review of the system checks data-processing or re-examined one or more applications.
Even if they are a mission review of one or several applications, the listener must start his mission by the summary awareness of the general environment of control of the data-processing function of the company.
Main goal of the summary review of the data-processing system checks is to evaluate the adequacy of controls within the data-processing department. This evaluation makes it possible to bring an opinion on the internal level of audit within the information system.
During this mission, the data-processing listener will have to re-examine the segregation of the tasks within the data-processing organization, the operations of exploitation around the environment of the operating system, work of development and maintenance of the applications, the data-processing security management, the management of the safeguards and the plan of continuity of exploitation.
Data-processing controls of applications are controls conceived to prevent or detect the errors and the irregularities being able to have an impact on the financial statements.
Controls of applications are exerted on the level of a cycle or a transaction. They have the aims of controls directly:
. The exhaustiveness of the recordings ;
. The exactitude of the recordings ;
. Validity of the recordings ;
. The access restricted in the active and the recordings.
During this review, the listener concentrates his work on the review of controls of the direction, the accesses, the entries, the rejections and the treatments.
In what follows, one will present the stages of the process of audit of a data-processing application, in support with the financial audit, in an integrated environment.
The process comprises three stages : Planning, Execution and Finalization.
At the time of this phase of the mission, the listener must take note of the data-processing environment of the company.
This awareness is limited to the systems which contribute to the establishment of the Financial statements.
Principal work of the listener at the time of this phase consists with a census of average data processing.
The awareness includes the collection of a specific further information relating to for example the following elements:
· The application or the systems which contribute to the establishment of the financial statements ;
· Computer equipement ;
· Controls of the direction exerted on the data-processing function;
· The complexity of the computerized treatments (volume of the operations, calculations complex, data exchanges, etc) ;
· The architecture of the existing information system;
· The general description of the applications ;
· Significant changes in terms of systems and data-processing environments ;
· Problems former identified to the level of the systems ;
· Data-processing projects in progress and to come.
The phase of collection of information is more important the first year or the year of the change because it helps to fix the strategy of audit (High, Some or No).
On the other hand, the following years, taking into account accumulated knowledge of audit, the process must be faster since the listener is interested only in the changes of the exercise.
At the end of this phase, the listener must normally have a clear idea on the information system of the company. The listener is brought to prepare a cartography of the systems (presentation of the information system : applications, interfaces) and a applicative card (information specific to the applications : names, nature, waiter, place)
Execution
After having taken a sufficient knowledge of the data-processing environment of the company, the data-processing listener passes to the production run.
During this phase, the objective of the listener is to appreciate the internal level of audit of the processes of management of the company and its impact on the certification of the accounts.
The listener aims at evaluating the adequacy and the quality of controls around the data-processing applications in order to ensure itself of the reliability of produced information.
The listener proceeds to the review and analyzes controls of the direction, access controls, entries, data rejected and treatments.
· Controls of the direction :
These controls are applied to the final information produced by the treated data. They are carried out a posteriori by people distinct from those in load of the treatment. Their goal is to detect errors or irregularities likely to occur upstream.
The information processing system offers to the direction several information useful for the piloting of the entity and the supervision of the activity.
Controls of direction can consist of the review and the follow-up of the logs of audit, the detection of the operations and the abnormal balances, etc
The objective of the listener is to make sure that the controls set up by the direction guarantee at the end of the treatments the reliability of produced information.
· The access :
In the organization of any company, one can find several departments. Each department exploits data-processing applications specific to its tasks. For example, the personnel of the sales department must limit itself to the use of the applications of this same service without having access to the applications of the financial service or of production. In practice, one frequently identifies people having access to data-processing applications which are not in relation to their operational tasks.
The listener must ensure himself of the respect of the rights of access granted to the users.
· Entries :
The entries can be defined as being all the data used in the treatments. They are the permanent data (name, first name, code article, price, code customer, bank account number, the wording, etc) and the transactions (Invoices, Purchase orders, etc).
The listener must make sure that the data are introduced and seized in the system in an exact way, exhaustive and single.
· Rejections :
In the companies which have a reliable and optimized information processing system, reports/ratios of rejection must be published regularly. These reports/ratios are re-examined by a person entitled in order to identify the rejected data, to analyze them and finally go up information for its assumption of responsibility by the operational directions having initiated the operation. The listener must check the edition of these reports/ratios and the correction of the errors.
· Treatments :
The listener must evaluate the quality of the controls applied to the treatments. These controls aim at providing a reasonable insurance that the transactions generated by the system are correctly treated by the computer over the good accounting period.
The results of the evaluation of controls of the direction, the entries, the access, the rejections and the treatments form for the data-processing listener the base of appreciation of the internal level of audit of the processes.
After the evaluation of the internal level of audit of the processes, the data-processing listener reports of his work at the team of financial audit. This conclusion will be retained as bases for the choice of an adequate strategy of audit on the level of the countable component concerned with the treatment of the application.
According to the approach of PricewaterhouseCoopers, three strategies of audit are possible :
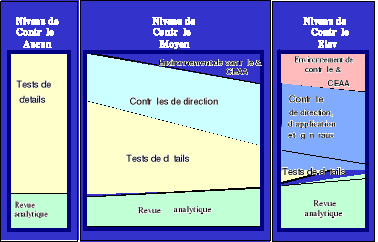
Figure 3 : Strategies of audit
This situation supposes that none controls applied is reliable : Controls of pilotings, data-processing system checks and controls of applications.
If the strategy of audit followed is NO, the financial listener must :
· To be unaware of the tests on key controls (controls of piloting and controls of applications) and on general data-processing controls ;
· To focus its work on the tests of detail like some analytical procedures.
The adoption of this strategy supposes the reliability of controls of piloting.
The financial listener is based on controls of the direction which ensure that there no were major failures. The confidence which the listener grants to these controls is decisive at the time of the determination of extended from the tests of detail.
The step of the listener consists with:
· To document controls of direction ;
· To test key controls of direction (of piloting and application) ;
· To be unaware of the tests on general data-processing controls ;
· To complete work of audit made up essentially of tests of detail as well as analytical procedures.
In this case of key controls (of direction and application) exist, are documented and powerful. The listener carries out tests on these controls to make sure of their effective operation and their permanence.
Thus, this step consists with:
· To document controls of direction, the system checks data-processing and controls of application;
· To test the data-processing system checks ;
· To select and test key controls of direction and application ;
· To carry out analytical reviews.
· The tests of detail are excluded at the time of the choice of this strategy.